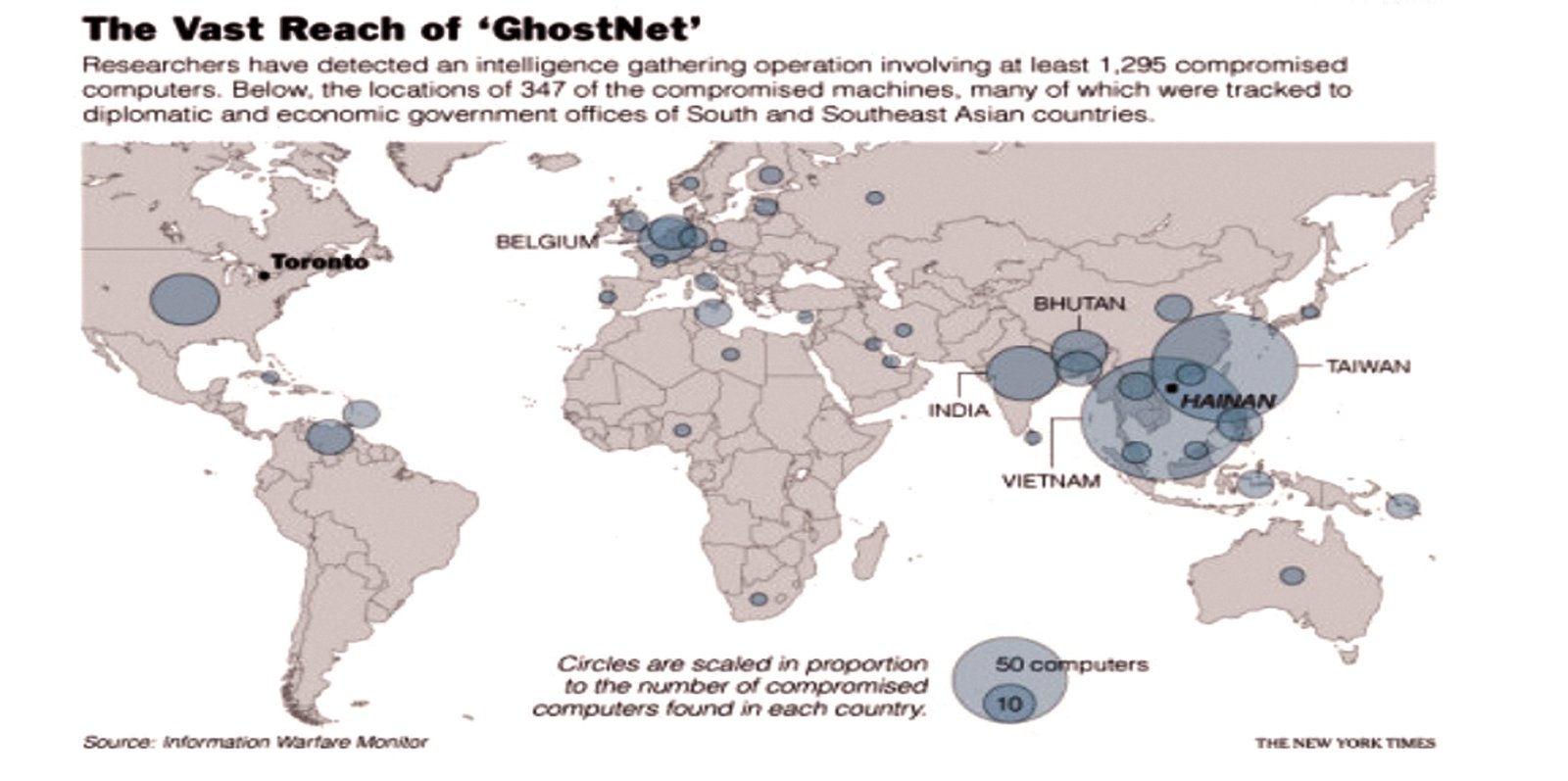
When the first building blocks of cyber space1 emerged in the 1960s, the concept of effective international cooperation for cybers ecurity was not a priority. Today, an ever-expanding information-based global cyber domain, dominated by wireless and fixed broadband, smartphones, the mobile Internet, cloud computing, open data, big data and social media, and linked infrastructures for transmission of information and the creation of a digital economy, is characterized by its trans-national or international character. It is generally accepted that this domain is multi-stakeholder in nature, and that information and communication technologies (ICTs) play a key role in the transformation of cyber space.
The four broadly accepted stakeholders in global cyber space are governments, businesses, academia and civil society. In terms of approaches to cyber security, the emergence of a digital society, both nationally and globally, which is dependent on the security of cyber space for myriad aspects of human endeavor, has significantly broadened the focus of governments. Businesses, licensed to operate in cyber space by the governments of their jurisdiction, have reflected this evolution, taking the lead in providing the necessary technologies and innovations to implement cyber security policies. Academia, which often partners businesses in innovating and applying new cyber technologies, has always played a vital role in spreading greater awareness of cyber issues, including vulnerabilities impacting on the security of cyber space. Civil society has contributed vigorously to upholding fundamental human rights in cyber space, while attempting to cope with cyber vulnerabilities which have a direct impact on the sanctity of human lives regardless of national boundaries.
It has become apparent to all stakeholders that the increasing speed and expansion of cyber space also contain inbuilt weaknesses which can be exploited to jeopardize the security of cyber space, including its use for meeting the aspirations of humanity for a prosperous future, driven by easily accessible ICTs. This has pushed the issue of cyber security to the forefront, and highlighted the need to ensure effective international cooperation on cyber issues, through coherence and cooperation among cyber space stakeholders.
Background
The United Nations General Assembly (UNGA) had first discussed scientific and technological developments in ICTs in the context of international security in 1998. It adopted a resolution that year sponsored by Russia following this discussion, which emphasized that such developments could have both civilian and military applications, and that “progress in science and technology for civilian applications needed to be maintained and encouraged”.2 Subsequently, in December 2002, a UNGA resolution called for the creation of a “global culture of cyber security”, highlighting 9 elements which could contribute to this objective. These elements included awareness, responsibility, response, ethics, democracy, risk assessment, security design and implementation, security management and reassessment.3
The initiative of the UNGA was dovetailed subsequently into the launch of global discussions on the “world information society” by the United Nations, resulting in multilaterally agreed outcomes from the United Nations’ World Summit on the Information Society (or WSIS) at Geneva (2002) and Tunis (2005), referred to commonly as the “Tunis Agenda”.4 The need for the Tunis Agenda to keep up with momentous changes in cyber space between 2005 to 2015 was underscored by the UNGA in its High Level Review of the Tunis Agenda in December 2015.5 The Review acknowledged the role of multi-stakeholders in cyber space, and called upon them to proactively accelerate the use of ICTs as a “means of implementation” for the global sustainable development framework. This framework had been unanimously adopted by world leaders at the UN Summit held three months earlier, in September 2015, as Agenda 2030, with its core 17 Sustainable Development Goals (SDGs).6
International discussions on cyber issues among all stakeholders recognize the concept that “a chain is as strong as its weakest link”. Whether these issues relate to cyber security, or cyber-crime, or providing equitable access to cyber space, or bridging the “digital divide” between and within countries, it is acknowledged that progress (or failure) to secure any one area of cyber space will impact on the entire cyber domain.
Role of governments
Against this backdrop, the role of governments in creating an effective framework for international cooperation on cyber security is critical, as public policy is the prerogative of governments. Apart from their sovereign functions in negotiating and adopting an international legal architecture to facilitate various aspects of such cooperation, governments are themselves also increasingly the largest stakeholders of cyber space in terms of the implementation of their security and development policies.
Governments adopted a resolution in the UNGA in December 2003 on “developments in the field of information and telecommunications in the context of international security”. They upheld the need for the free flow of information while looking at concepts aimed at strengthening cyber security. The resolution asked the UN Secretary General to seek the assistance of a Group of Governmental Experts (GGE), appointed on the “basis of equitable geographical distribution and with the help of Member States in a position to render such assistance”, to report on the way forward to the UNGA.7 From 2005 onwards the UNGA stipulated only the geographical representation criteria for the UN Secretary General to follow while appointing experts to the GGE.8
This approach determined the way the GGE has functioned in two significant ways. First, in the absence of any multilateral roster of “experts” provided by member states, the UN Secretary General has selected countries, and not individual experts, to compose the GGE. The selected countries have been free to designate their experts for the discussions of the group. While some governments have opted for continuity in selecting their experts while participating in the different editions of the GGE, others have opted for rotating their nominees, which has prevented the GGE from adopting a collegial approach to its work. Secondly, discussions in the GGE have been skewed towards a narrow perspective on international cooperation on cyber security, based on the mandate of the First Committee of the UNGA, which is to look at “disarmament, global challenges and threats to peace that affect the international community …and challenges to the international security regime”.9 In the process, the initial emphasis of the UNGA in December 199810 to give primacy to civilian, rather than military, applications of ICTs has dropped by the wayside.
What has been the outcome of the work of the GGE so far on establishing effective international cooperation on cyber security? GGEs have normally worked for a two-year period. There have been five editions of the GGE constituted by the UN Secretary General so far between 2004-2017, with selected participating member states fluctuating from 15 in its first three editions to 20 for the fourth GGE and 25 for the fifth GGE. India has participated in the first three and the fifth GGEs.11The UN Secretary General has consistently nominated the five permanent members of the UN Security Council (China, France, Russia, the United Kingdom and the United States) to all editions of the GGE, implicitly linking its work to the dynamics of these five countries in the Security Council.
The first GGE could not agree on an agreed report in 2005, due to three areas of divergence. First, there was divergence on the impact of ICTs on national security and military affairs. Second, there were divergences on whether the proposed international framework for cyber security should focus only on the content, or only on the infra-structure, of ICTs. (Significantly, this divergence between content and infrastructure also led to the deadlock in updating the regulations of the specialized UN agency responsible for tele-communications, the International Tele-communications Union (ITU), at its Conference held in Dubai in 2012).12 A third area of divergence was on the issue of technology transfer to developing countries. These divergences led the UNGA to ask the UN Secretary General to constitute another GGE in 2009.
The second GGE, constituted in 2009, issued a consensus report in 2010. It recommended dialogue among member states to reduce the risk and protect critical national and international cyber infrastructure; confidence building and risk-reduction measures, including the use of ICTs during conflict; capacity building; and elaboration of common terms and definitions in cyber security.
The third GGE in June 2013 agreed with the proposition that international law, and especially the UN Charter, applied to cyber space, while confirming that state sovereignty applied in cyber space. It underlined that cyber security should be in consonance with respect for human rights and fundamental freedoms. It called on member states to respect their obligations not to allow proxies or non-state actors to use their jurisdictions for violating cyber security.
The fourth GGE in 2015 recommended some norms to secure cyber space. These included the recommendation that “States cooperate to prevent harmful ICT practices and should not knowingly allow their territory to be used for internationally wrongful acts using ICT.” It emphasized that “States should guarantee full respect for human rights, including privacy and freedom of expression. A State should not conduct or knowingly support ICT activity that intentionally damages or otherwise impairs the use and operation of critical infrastructure. States should also take appropriate measures to protect their critical infrastructure from ICT threats. States should not harm the information systems of the authorized emergency response teams of another State or use those teams to engage in malicious international activity. States should encourage the responsible reporting of ICT vulnerabilities and take reasonable steps to ensure the integrity of the supply chain and prevent the proliferation of malicious ICT tools, techniques or harmful hidden functions.”13
Further progress was halted when the fifth GGE process reached a deadlock at its final meeting in June 2017. This was due to divergences on how international law would apply to the use of ICTs by states. In a public statement, the United States affirmed that “the framework of international law provides States with binding standards of behavior that can help reduce the risk of conflict by creating stable expectations of how States may and may not respond to cyber incidents they face”, a view which was not agreed to by some other members of the GGE.14
Role of Businesses
While the GGE has articulated behavioral norms based on international law for international cooperation on cyber security, some trans-national businesses headquartered in the United States have taken initiatives to foster international cooperation based on the technology that drives cyber space. In February 2017, Microsoft advocated a “Digital Geneva Convention”, that is meant to “commit governments to protecting civilians from nation-state attacks in times of peace” with the active assistance of technology companies.15 Facebook, Microsoft, YouTube and Twitter joined hands in June 2017 to launch a Global Internet Forum to Counter Terrorism.16
Earlier, in June 2016, Microsoft had proposed a roadmap for developing offensive norms, defensive norms and industry norms. It pointed to the difficulty in attributing and countering threats to cyber-security because of “global connectivity, anonymity, and lack of traceability”. Microsoft suggested that governments should adopt the model of public-private partnership in developing cyber security norms, as had been done in the case of the Financial Action Task Force (FATF), where consultation with the private sector helped effective implementation of financial norms, as well as a platform for private sector priorities to be addressed by governments.17
International cooperation on cyber security has also been pursued by businesses which maintain the global cyber infrastructure. Currently, 13 “root servers”, administered by 12 entities, control the functioning of global cyber space.18 In this context, norms developed through platforms such as the Internet Corporation for Assigned Names and Numbers (or ICANN), have become relevant. The main functions of the ICANN are to allocate domain names, numbering resources, and decisions on internet protocol parameters. Each of these functions has a significant ground-level impact on international cooperation on cyber security. A similar ongoing role is being played by the professionals who create cyber space, represented by the Internet Engineering Task Force (IETF)19.
Role of Academia
Academia’s contribution to establishing an international framework of cooperation on cyber security has a long history. Its focus on people as well as technology enables academia to address one of the major challenges of cyber security, which is the human factor. Generating awareness is perhaps the most significant contribution that academia can make to effective international cooperation on cyber security, by preventing the exploitation of vulnerabilities in cyber space. The constant flow of graduates from academia into both governments and businesses represents a continuous upgradation to the international community’s efforts to tackle issues of cyber security.
Academia has often taken the lead to make significant conceptual contributions to evolving an international framework of cooperation on cyber security. For example, almost a decade ago, a white paper prepared for the White House by Pradeep Khosla, the founding director of Carnegie Mellon’s CyLab, advocated that a more relevant approach to cyber security policy would be to look at a “data-centric” rather than a “device-centric” approach.20
Apart from generating greater awareness of the vulnerabilities of cyber space, and looking at the issue of cyber security from a multidisciplinary perspective, academia also plays a hands-on role in ground-level international cyber security cooperation. This is well illustrated by two universities in the United States (University of Southern California and University of Maryland) who manage two of the 13 root servers of the internet. A focused participation in the global discussion on the need for international cooperation on cyber security is the hallmark of academic think-tanks across the world, though many of them are funded by sources looking at cyber security issues from a military perspective.
Role of Civil Society
Civil society is perhaps the most vocal stakeholder of cyber space, using cyber tools such as social media to advocate its views. Ensuring the upholding of fundamental human rights online has been recognized as one of the core advocacies of civil society as governments work to establish a framework for effective international cooperation on cyber security. These rights include, inter alia, freedom of expression, privacy, and human dignity.
The Way Ahead
As this brief review outlines, the current multilateral effort to create an international framework for effective international cooperation on cyber security through the GGE of the UNGA has probably reached its limit. Countries which are active in cyber space have initiated steps to position their views on issues like cyber norms and application of international law in a confrontationist, rather than cooperative, mode. Without a cooperative approach among governments at the multilateral level, the initiatives taken by businesses, academia and civil society to augment an appropriate international framework are greatly diminished.
While bilateral and regional frameworks have been welcomed by the multilateral process under the United Nations, including during the Review of the Tunis Agenda in December 2015, the impact of these frameworks would be limited to participating countries. For effective global cyber security cooperation, the core focus must remain on a universally applicable framework, which has its focus on the weakest link in the global cyber chain.
How can this happen? The time has come for the UNGA to adopt a resolution to launch broad-based multilateral negotiations, with inputs from the major stakeholders, on international cooperation on cyber security. These negotiations should be launched by the UNGA as part of its review of the implementation of Agenda 2030.
The UNGA has acquired relevant experience for such multi-stakeholder negotiations, which have been led by governments, during the past few years, when global issues such as sustainable development and the evolution of a world information society were placed on the UNGA’s agenda, and successful outcomes reached.
In any such future negotiations, some potential areas of divergence could arise. One issue would be who would decide on the question of attribution for attacks on cyber security, given the skepticism among a majority of UN member states for such issues to be referred to the UN Security Council as currently structured, where necessary structural reforms, including on decision-making, have been resisted by some of its permanent members. Another potential area of divergence would be in adopting a common template to counter perceived cyber security vulnerabilities in industrialized and developing countries, and where national capacities to respond to threats require technology transfers and financial flows. Divergent economic interests of major multinational ICT businesses and new emerging ICT businesses will inevitably be reflected in these negotiations when counter-measures are conceptualized. Negotiators will have to identify provisions drawn from applicable international law, including the UN Charter, the WTO’s corpus of international trade law and international humanitarian law.
However, potential divergences cannot detract from the urgent need to secure global cyber space, through an internationally agreed framework on effective cooperation on cyber security. As the UNGA has pointed out repeatedly, the impact of effective international cooperation on cyber security is not only restricted to international peace and security, but also to development. In this context, there is need to broaden the negotiating mandate for an international framework to include the “development dimension” of cyber security, drawing upon the specific provisions contained in Agenda 2030 and the Tunis Agenda.
In any such international negotiation, the role of India in focusing on the “development dimension” of international cyber security cooperation will be crucial. The scale of India’s national programmes which apply ICT for development is unique, symbolized by the nine pillars of Digital India with its Aadhar database, provide a ground-level drawing board for conceptualizing and testing cyber security concepts, as well as the effectiveness of international cooperation in securing developmental programmes.21 A special focus would need to be provided by India during these negotiations on the impact on designated critical national infrastructure sectors.22 India’s advocacy of using a “development” perspective in the process to create a supportive international framework for cooperation in cyber security will be relevant for a large number of other developing countries, who are prioritizing the use of ICTs to meet their sustainable development goals under Agenda 2030.
The objective should be the creation of a framework on cyber security which will serve the global cyber domain in the same manner that the United Nations Convention on the Law of the Seas (UNCLOS), which was negotiated between 1973 and 1982, serves the global maritime domain.
References
1 Internet Society, “Brief History of the Internet”. Available at
http://www.internetsociety.org/internet/what-internet/history-internet/brief-history-internet
2 United Nations General Assembly Resolution A/RES/53/70 dated 4 December 1998. Available at
https://documents-dds-ny.un.org/doc/UNDOC/GEN/N99/760/03/PDF/N9976003.pdf?OpenElement
3 United Nations General Assembly Resolution A/RES/57/239 dated 20 December 2002. Available at
http://www.un.org/en/ga/search/view_doc.asp?symbol=A/RES/57/239
4 “Tunis Agenda for the Information Society”. Available at
http://www.itu.int/net/wsis/docs2/tunis/off/6rev1.html
5 United Nations, “Outcome Document of the high-level meeting of the General Assembly on the overall review of the implementation of the outcomes of the World Summit on the Information Society”, UNGA Resolution A/RES/70/125 dated 1 February 2016. Available at
http://www.un.org/en/ga/search/view_doc.asp?symbol=A/RES/70/125
6 United Nations, “Transforming our world: the 2030 Agenda for Sustainable Development”. Available at
https://sustainabledevelopment.un.org/post2015/transformingourworld
7 United Nations General Assembly Resolution A/RES/58/32 of 8 December 2003. Available at
http://www.un.org/en/ga/search/view_doc.asp?symbol=A/RES/58/32
8 United Nations General Assembly Resolution A/RES/60/45 dated 8 December 2005. Available at http://www.un.org/en/ga/search/view_doc.asp?symbol=A/RES/60/45
9 United Nations. “Disarmament and International Security: First Committee”. Available at http://www.un.org/en/ga/first/
10 See footnote 3 above.
11 For a summary record of the work done by the four GGEs, the United Nations Office of Disarmament Affairs Fact Sheet, available at https://unoda-web.s3-accelerate.amazonaws.com/wp-content/uploads/2015/07/Information-Security-Fact-Sheet-July2015.pdf is useful. India was omitted by the UN Secretary General for the Fourth GGE due to alleged pressures from other countries to apply the criteria for rotational representation. From the Asia-Pacific region, China, Japan, Malaysia and Pakistan were chosen by the UN Secretary General. India was re-nominated to the Fifth GGE by the Secretary General in 2016.
12 For an outsider’s account of this deadlock, see “What really happened in Dubai”, Internet Governance Project, Georgia Tech. Available at
http://www.internetgovernance.org/2012/12/13/what-really-happened-in-dubai/
13 United Nations. Report of the GGE to the UN Secretary General No. A/70/174 dated 22 July 2015. Available at https://documents-dds-ny.un.org/doc/UNDOC/GEN/N15/228/35/PDF/N1522835.pdf?OpenElement
14 United States Department of State.“Explanation of Position at the Conclusion of the 2016-2017 UN Group of Governmental Experts (GGE) on Developments in the Field of Information and Telecommunications in the Context of International Security “. Available at https://www.state.gov/s/cyberissues/releasesandremarks/272175.htm
15 “The need for a Digital Geneva Convention”, Microsoft. Available at
https://blogs.microsoft.com/on-the-issues/2017/02/14/need-digital-geneva-convention/
16 Global Internet Forum to Counter Terrorism. Available at
https://blog.twitter.com/official/en_us/topics/company/2017/Global-Internet-Forum-to-Counter-Terrorism.html
17“From Articulation to Implementation: Enabling progress on cyber-security norms”, Microsoft. Available at
https://mscorpmedia.azureedge.net/mscorpmedia/2016/06/Microsoft-Cyber security-Norms_vFinal.pdf
18 A map of the 13 global root servers is available at http://www.root-servers.org
For technical details on root servers and related issues, see “What are Root Name Servers”, Netnod, Sweden. Available at https://www.netnod.se/i-root/what-are-root-name-servers
19 See “About the IETF”. Available at https://www.ietf.org/about/
20 EDUCAUSE Review.Academia’s role in security cyberspace, Jared Cohon, 2009. Available at
https://er.educause.edu/articles/2009/9/academias-role-in-securing-cyberspace
21 The breadth and depth of India’s cyber profile was presented during the Review of the Tunis Agenda by the UNGA in December 2015. It is available at
http://workspace.unpan.org/sites/Internet/Documents/UNPAN95026.pdf
22 For a discussion on the issues involved in protecting India’s Critical National Infrastructure, see “Protection of Critical Information Infrastructure: an Indian Perspective” by Col. R.K. Sharma, The Digital Policy Portal, Observer Research Foundation. Available at
http://www.digitalpolicy.org/protection-of-critical-information-infrastructure-an-indian-perspective/
(Asoke Kumar Mukerji is a former diplomat. He was India’s Permanent Representative to the United Nations in New York from 2013-2015. He supervised India’s participation in United Nations Review of the Tunis Agenda in 2015. He has led Government of India’s multi-agency delegations for International Cooperation on Cyber Issues with the United States, Russian Federation, United Kingdom, and Japan during 2011-2013.)
(This article is carried in the print edition of September-October 2017 issue of India Foundation Journal.)