India Foundation hosted a farewell reception for H. E. Naor Gilon, Outgoing Ambassador of Israel to India, on July 19, 2024. In his three-year tenure as the Ambassador of Israel to India, he has actively promoted and assisted in maintaining the strong ties between the two countries. Several eminent dignitaries attended the event and conveyed their best wishes to the outgoing ambassador.
Defining ASEAN centrality in the Indo-Pacific
India Foundation hosted a roundtable discussion on “Defining ASEAN centrality in the Indo-Pacific” with a delegation from S. Rajaratnam School of International Studies of Singapore on July 12, 2024 in New Delhi. The discussions were led by Amb Ong Keng Yong, Executive Deputy Chairman, RSIS, Singapore and Vice Adm Shekhar Sinha, Chairman, Board of Trustees, India Foundation. The session was also addressed by Amb TCA Raghavan, Former Ambassador of India to Singapore and Dr Sinderpal Singh of RSIS.
The discussions centred around the strategic importance of ASEAN, regional challenges, and the implications of China’s actions in the region. The importance of ASEAN’s strategic location, particularly with regards to the South China Sea, was emphasized due to its geopolitical and economic significance. ASEAN countries, being some of the most impacted by regional tensions, play a crucial role in addressing these challenges. The discussion highlighted China’s aggressive behaviour concerning its territorial claims over Taiwan, the Senkaku Islands, and the Paracel Islands.
In their opening remarks, Amb Ong and Adm Sinha touched upon various facets of ASEAN’s centrality to the Indo-Pacific. They stressed on the necessity for ASEAN to respond collectively to regional challenges and emphasized on the emergence of India as a key partner. The strong bilateral relations between India and ASEAN countries were also acknowledged as crucial for fostering regional cooperation.
The scope of discussions further included ASEAN’s pillars of engagement with the Indo-Pacific, differences between various Southeast Asian states and individual approaches to the Indo-Pacific and how Southeast Asia is possibly negotiating this vision of the Indo-Pacific.


Tibet Talks – 7 – The Resolve Tibet Act: Legal and Humanitarian Perspectives
India Foundation organized the seventh session of the Round-Table Discussions in the ongoing “Tibet Talks” series. The topic for this session was “The Resolve Tibet Act: Legal and Humanitarian Perspectives”. The session was addressed by Dr Tenzin Dorjee, Senior Researcher and Strategist, Tibet Action Institute. The Round-Table Discussion took place on 9 July 2024 (Tuesday) at the India Foundation office, with the session chaired by former Ambassador Dilip Sinha.

To start the discussion, Dr Dorjee emphasized the importance of the Resolve Tibet Act as it symbolized a change in the United States’ policy towards Tibet, especially with the Act explicitly stating that the U.S never recognized Tibet historically as a part of China. This shift in tone displays the U.S’ renewed focus on advocating for the collective right of self-determination instead of purely individual rights for the people of Tibet. Additionally, Dr Dorjee highlighted his own personal experiences: growing up in India, attending Tibetan schools, and living in the United States. He then underscores how three generations of Tibetans living in exile have maintained the Tibetan culture, language, and lifestyle that continues to flourish in India, given the country’s commitment towards protecting the government in exile while providing Tibetans with a space to live and preserve their culture in peace. Furthermore, Dr Dorjee details the importance of the Act’s passage for Tibet’s status on the world stage. With the Act invoking the idea of self-determination for the people of Tibet, the U.S is attempting to shift the mainstream perspective from a diplomatic to an international law point of view.
To conclude, Mr. Dorjee emphasizes how the Resolve Tibet Act has laid the groundwork for new opportunities to further expand the movement to free Tibet.

Book Discussion on ‘The Indentured and Their Route: A Relentless Quest for Identity’
India Foundation, in collaboration with India Habitat Centre, organised a book discussion on ‘The Indentured and Their Route: A Relentless Quest for Identity’, authored by Amb Bhaswati Mukherjee, President, India Habitat Centre and Ambassador of India to the Netherlands (2010-2013) at Gulmohar Hall, India Habitat Centre, on July 02, 2024. The event began with the initial remarks by Captain Alok Bansal, Director, India Foundation, who introduced the book to the audience and later moderated the discussions. Prof Amitabh Mattoo, Dean & Professor, School of International Studies, JNU and Dr T.C.A. Raghavan, Former Director General, Indian Council of World Affairs (ICWA) discussed the book with the author.

Ambassador Mukherjee eloquently highlighted the compelling narrative of this book, which sheds light on the heart-breaking journey of Indian indentured labourers who were compelled to leave their homeland for distant lands like the West Indies, Mauritius, Suriname, Reunion, and Fiji. Driven by desperation due to famine, poverty, and oppressive conditions in India, these individuals were lured by false promises that ultimately led to forced labour and significant loss of heritage.

Professor Mattoo praised the author, noting that this book is a breath of fresh air as it delves into an important area with elegance, drawing from diverse sources and imbued with poetic language. This book fearlessly challenges conventional wisdom and offers a novel perspective on indentured labour and their ancestral connection with their Indian homeland.
Dr. Raghavan shed light on the content of the book, stating that the book provides numerous examples, such as Fiji, where the identities of former indentured servants were on the brink of being systematically erased. These individuals, tied to colonial legacies, were compelled to sever their connections to their roots and histories. The book offers a profound insight into the enduring impact of indentured slavery, a practice often viewed as a temporary phase in human history, yet persisted for 70-80 years. He found the book to be deeply reflective and thought-provoking, challenging readers to consider the complexities of legacy and urging a re-evaluation of how we perceive diaspora communities today. The discussion was followed by Q & A session where several questions related to the book and the author were asked by the audience.


Rājadharma: The Bhāratīya Notion of Welfare State
Since ancient times, civilisations have recognised the need to regulate individual behaviour and social conduct to prevent anarchy and chaos. In the Bhāratīya Paraṁparā, this regulation found expression in the concept of Rājadharmạ, or the duties of a ruler, which emphasised the integration of temporal power with spiritual wisdom for the collective welfare. Ancient Bhāratīya thinkers, guided by practical concerns rather than abstract theorisation, envisioned political governance to promote universal well-being. They emphasised the importance of a ruler adhering to the principles of dharma (duty) and śāsana (regulation) to ensure peace, progress, and prosperity for all beings. The ideal of Rājadharmạ, exemplified by figures like Śrī Rāma, emphasises the holistic welfare of the entire cosmos, transcending narrow notions of material prosperity. It stresses the symbiosis of political power with spiritual wisdom, wherein governance is not merely about enforcing laws but also about upholding moral values and accountability.
Through a synthesis of dharma and śāsana, a ruler is expected to serve and protect the people selflessly (niṣkāmabhāva), ensuring their happiness and well-being (sarvabhūtahita” and “lokasaṅgraha). In modern times, the concept of Rājadharmạ remains relevant as societies strive for inclusive development and universal welfare. By embracing its principles of duty, responsibility, and spiritual wisdom, nations can aspire towards a more just, equitable, and harmonious world order. This research article aims to explore the concept of Rājadharmạ, or the duties of a ruler, within the Bhāratīya tradition, highlighting its integration of temporal power with spiritual wisdom for collective welfare. Through an examination of ancient Bhāratīya thinkers, it elucidates their emphasis on practical governance rooted in principles of dharma (duty) and śāsana (regulation) to ensure peace, progress, and prosperity for all beings.
Since the dawn of civilisation, there has been a recognised need to regulate human social conduct alongside individual behaviour. Humanity, both cooperative and selfish by nature, has grappled with instincts of cooperation and conflict, necessitating the establishment of order to prevent anarchy (arājakāta) and a “rule of the jungle” (matsyanyāya). For the preservation and advancement (yoga-kṣema) of communal life, social and political governance becomes imperative to prescribe and enforce order. Ancient Indian seers and sages envisioned order at the core of reality, known as ‘ṛta’, finding its expression in temporal power as ‘an authority’ (law) and ‘in authority’ (those who wield power). This temporal power (kṣatra tejā) was seen as subordinate to and tempered by spiritual power (Brahma tejā), ensuring its purpose served the greater good. In general, power (Śakti) must be imbued with wisdom (Śiva) for benevolent outcomes. Political governance, prone to perversion and corruption due to its overpowering nature, requires spiritual discipline, hence termed ‘Rājadharma’ or ‘Dandanīti’. These terms reflect the spiritual orientation of political power, engineered for universal peace, prosperity, and well-being.
Lord Rama, exemplified the exercise of political power in a spiritual manner, projecting his rule as an ideal of a welfare state, termed Rāmarājya, a Sarvodaya state. The suffix ‘sarva’ extends beyond human society to encompass the welfare of the entire cosmos, including animals, forests, and rivers. The underlying principle is that the universe is a habitat for all existences, animate and inanimate, sharing the same divinity and living together with mutual care and sharing. In good governance, everyone is treated as having both intrinsic worth and instrumental value, viewed not solely as an end or means but as both simultaneously. In communal life, coexistence and interdependence prevail, fostering reciprocity and mutual support among all elements of the cosmos, encapsulating the ideal pursued in an ideal state, thereby realising a genuine welfare state.
The ancient Indian thinkers on political affairs were primarily driven by practical governance concerns, eschewing abstract theorisation in their reflections. Neither in ethics nor in politics did they indulge in pure speculation; instead, they meticulously discussed the minutest details of state administration for the well-being of all beings (prajā). Various treatises, apart from the well-known epics and scriptures like Rāmāyaṇa, Mahābhārata, Purāṇas, and Dharmaśāstras, delve into polity and state administration, with references to now-extinct Arthaśāstra treatises. Unlike modern trends advocating rigid theories or ‘isms’, ancient Indian literature lacks such formulations. Instead, it offers subtle discussions on practical aspects of governance, aiming to guide rulers in day-to-day administration after providing them with education and training. These discussions are based on concrete experiences and pragmatic considerations, avoiding empty generalisations and pure abstractions.
Indian thinkers recognised the importance of bridging the gap between theory and practice, emphasising that the ideal must be achievable from actual experiences. This ideal, termed puruṣārtha, integrates the end (sādhya), means (sādhana), and modalities (itikartavyatās), ensuring that the end is beneficial, the means are conducive, and the modalities are accessible. In this approach, theory is not divorced from practice but interwoven with it in a dialectical relationship. Ancient Indian literature emphasised practical wisdom over abstract theory, employing empirical observation, analysis, and deduction methods and leading to the development of treatises on politics rather than political science.
While classical Bhāratīya political thought does not explicitly present a theory of the welfare state, it is rich in welfare ideals that serve as guiding principles for governance. The literature is abundant with profound concepts emphasising collective well-being, permeating political and cosmic organisation. These principles, integral to every ruler’s mandate, suggest a holistic approach to welfare that transcends mere governance, encompassing human existence and cosmic harmony. This comprehensive approach to welfare, deeply ingrained in ancient Indian political thought, is truly inspiring.
The entire Bhāratīya thought, across all its domains of reflection, is rooted in the fundamental belief that the cosmos is a divine manifestation with an inherent purpose and value. From ancient texts like the Puruṣa sūkta of the Ṛgveda to modern thinkers such as Vivekananda, Śrī Aurobindo, B.G. Tilak, and Mahatma Gandhi, this idea of a divine purpose permeates the philosophy. It is believed that the universe exists, sustains, and culminates in a state of supreme well-being and bliss, often referred to as Amṛtatva, Brahmatva, mokṣa, or nirvāṇa. All human endeavours, organisational structures, and the cosmic process itself are directed towards this end. Concepts like ‘svasti’ and ‘śivam’ signify the pursuit of universal well-being and bliss. Additionally, concepts like ‘śubha’, ‘sukha’, ‘śānti’, and ‘maṅgala’ express the ideals of goodness, happiness, peace, and auspiciousness inherent in Bhāratīya philosophy. The Vedic seers emphasised the well-being of the entire cosmos, as evidenced by the famous ‘Śāntipatha’ from the Yajurveda Saṃhitā (36.17, Vājasaneyi Madhyadina śukla), which underscores the holistic welfare of all beings:
“aum dyauḥ śāntir antarikṣa śāntiḥ pṛthivī śāntir āpaḥ śāntir auṣadhayaḥ śāntiḥ vanaspatayaḥ śāntiḥ viśvedevāḥ śāntiḥ brahma śāntiḥ sarva śāntiḥ śāntir eva śāntiḥ samā śāntiḥ reḍhi”[i]
(May there be peace and prosperity in the outer and inner space, on earth, in the waters, in the life-giving vegetable kingdom, in plants and trees, in the cosmos, in the entire reality, everywhere and at all times. May there be peace and prosperity. Peace and prosperity alone (never otherwise). May everyone attain and experience peace and prosperity.)
Every human activity- both individual and collective- has to be geared to realise this goal of peace, prosperity and perfection. The Ṛgveda (V.51.15) says, “ Svasti pantham anucarema sūryācandramasāviva.” All puruṣārthas (conscious and wilful human efforts) and all prayers and propitiations to supra-human agencies aim at this. There is a tacit realisation of inadequacy of human effort and the need for supra-human support or divine help. “Sanno kuru prajābhyah” (Let there be welfare of the entire creation), beseeches the Vedic seer. Even though the Sramana tradition opposed this mind-set, the Indian psyche remained unaffected. The point is that since the entire cosmos has inevitable and natural teleological orientation there is a deontological injunctive-ness in social, moral and political spheres to make a conscious attempt at pursuance of the good and the right, to follow the path of ‘Ṛta.’ The pursuit of this ideal was a collective endeavor, evident in countless prayers for unity and shared well-being found throughout Bhāratīya literature, particularly in the Vedas. The thinkers of this land prioritized the welfare of the entire cosmos, shaping human behavior, social structures, and state activities towards the common good and prosperity. The ideal of all thought and conduct was:
sarvo vai tatra jīvati gaurasvaḥ puruṣaḥ paśuḥ|
yatredaṁ brahma kriyate paridhirjīvanāya kam||[ii]
(May humans, animals, birds and all other existences coexist in peace and there is room for every life.)
It is to be noted that the guiding principle of the statecraft and political organisation and administration has to be welfare of the people and well-being of the cosmos and there is no incompatibility between the two. This was the ideal of a state depicted in the Rāmāyaṇa and practiced by Rāma, the King of Ayodhya. Even the Śrīmadbhāgvatam states:
na aham kāṅkṣye rājyam na svargam apunarbhavam
kāṅkṣye duḥkha tr̥ptānām prāṇinām artanāśanam.
(I do not desire kingdom, nor heaven, nor even liberation from rebirth.
What I desire is the cessation of suffering for all living creatures.)
There can be no better ideal of welfare state than the one propounded here. The word ‘rājan’ in one of its etymological meanings stands for a ruler who pleases the people and makes them happy. Another word ‘nṛpa’, a synonym of it, conveys the idea of the ruler as a protector and sustainer of people. Kauṭilya extends this idea covering the entire world. He points out that a ruler has to be well versed in Arthaśāstra apart from other background studies and the objective of Arthaśāstra is to deal with protection and well-being of the entire universe. He writes, “Pr̥thivyā labharthe palane ca yavanty arthaśāstrāṇi purvācāryaiḥ prasthāpitāni prayatnena samhṛtya ekaṁ idam arthaśāstram kṛtam.” He explicitly maintains that in the happiness of people lies the happiness of the ruler and in what is beneficial to the people lays his own benefit. To quote:
praja sukhe sukham rājñaḥ, prajānām ca hite hitam|
nātma priye hitam rājñaḥ, prajānām tu priyam hitam||[iii]
(In the happiness of the people consists the happiness of the ruler, and in what is beneficial to the people, his own benefit. What is dear to him as an individual is not really beneficial to him as a ruler. What is dear to the people is really beneficial to him)
A ruler has to be the preserver of order both temporal and spiritual. He is therefore referred to as ‘Dharmagopta’. He is not the creator of the order but only propagator (dharma pravartaka). He has to uphold the law and order and therefore he is called ‘dandadhārta’. This he has to do for peace, progress and prosperity of the people in just and fair manner. He has political power that acquires legitimacy only in so far as it promotes human happiness and enriches life. Manusmṛti (VIII.14) states:
dandah śāstī prajāḥ sarvāḥ, danda eva abhi rakṣati,|
dandah suptesu jagarti, dandah dharma vidur budhāḥ||[iv]
(It is public order that regulates people. It protects and secures them. It keeps awake in the midst of slumbering. The wise regard it and dharma as one and the same)
Kautilya also maintains that daṅda is needed to promote proper and equitable distribution of social gains, and for material prosperity and spiritual enhancement. He writes, “Ānvīkṣikī trayī vartanam yoga-kṣema sādhano dandah. Tasya nitir dandanitiḥ. Alabdha-labhārtha labdha-parirakṣinī rakṣitāvivardhinī vr̥ddhasya tīrthāsu pratipadini.”[v]
The concepts of yoga-kṣema are of particular significance in this context. They stand for preservation and furtherance of natural resources and also their just and equitable distribution. It is the duty of a state to ensure this. It is noteworthy that this is a forerunner of the idea of ‘Sarvodaya.’
The Indian treatises on polity are full of need for danda and also for the regulations for the dandadhṛta. For smooth, efficient and planned functioning of any organisation there is a need for norm-prescription, norm-adherence, norm-enforcement and punitive measures for norm-violation. So, to ensure norm-conformity there is a need for an authority of law and a person who is in authority. An authority is impersonal law but the person in authority is the ruler, a person or a body of persons, who execute and ensure law-abidance. ‘An authority’ is autonomous but a person ‘in authority’ is subject to rules and regulations. ‘An authority’ has intrinsic worth but ‘a person in authority’ has instrumental value to rule out anarchy and to ensure peace and justice. He is appointed for the sake of maintenance of law and order. For this he may build up institutions and introduce systems. But in all this he is duty-bound and therefore he has to abide by some rules and regulations. The ‘rāja’ also has a dharma, a law-abiding status. He must know his dharma and must have a will and ability to abide by it. In the Mahābhārata we have a very apt, telling and succinct account of this idea in the oath to be administered to a ruler at the time of his appointment when he is advised to protect the people lawfully and never to act in an arbitrary manner. He is required to take a solemn vow to observe dharma and to make people observe dharma in a free and fearless manner. The wording of the oath is as under:
pratijñāṁ ca varohasva manasā karmāṇā girā|
palayiṣyāmy ahaṁ bhāumam brahmaiti eva ca sakṛta||
yaś ca tatra dharma ityukto dandanīti vyapāśrayaḥ|
tamasaṅkam kariṣyāmi svavāso na kadācana||[vi]
(Make a promise, and with your mind, deeds, and words, I shall protect the earth as per my oath. Wherever the duty of righteousness and the policy of punishment are in place, I shall root out darkness. I shall never reside in a place where there is disgrace.)
Dharma has cosmic sphere of operation. It sustains the entire cosmos and all beings. It has both constitutive and regulative roles. It constitutes the life-force and sustaining power. The entire cosmos is dharma-bound and therefore the ruler also is dharma-bound. Rājadharma is double-edged. It puts desirable restraints on the public so as to enable them to realise their puruṣārthas but at the same time it makes the person in authority subject to restraints. The person in authority is not to enjoy power and privileges but to discharge duties and responsibilities. He cannot be immune to accountability and oblivious of his obligations.
Śukrācarya, a great political thinker of yore, maintains that the ruler is both a servant and a master of the people. Therefore, he has to protect the people as master by virtue of law and serve them by virtue of his wages. He writes:
svabhāga-bhṛtya dāsyatvam prajānām ca nṛpakṛtaḥ|
brahmānā svamirūpastu palanārtham hi sarvadā||[vii]
(The ruler serves and protects all living creatures in his country. However, he should always act as a Brahmin)
There is not only an insistence on proper education and training of the ruler, but it was also made mandatory that the state power (kṣatra teja) should be seasoned and tempered by spiritual power (Brahma Teja). To ensure that the state acts for the welfare of the people and to eliminate the despotic behaviour of a ruler, In Indian thought, politics was never devoid of dharma and was treated as a means to general well-being. As stated earlier, Rajadharma is double-edged. It puts desirable restraints on people’s behaviour, but at the same time, it makes the rulers responsible and accountable by restraining them. A symbiosis of dharma and śāsana is the cornerstone of a welfare state. No one can be a good ruler without being well-trained in dharma and śāsana. There cannot be a separation of politics and spirituality. Political power acquires moral legitimacy only when it is seasoned with spirituality. Only then can it serve its avowed goal of cosmic well-being. Genuine welfare is not the material well-being of a particular section of human society but the holistic welfare of the entire cosmos. It is spiritual welfarism that includes and also transcends material welfarism. This is the true meaning of raja dharma, which may be taken as a concept, theory, viewpoint, or course of action, but in whatever form it is understood, it has great potential for universal good.
Conclusion
It can be concluded that from the dawn of civilisation, a need arose to regulate human social conduct alongside individual behaviour. The human inclination toward cooperation and conflict necessitated the establishment of order to prevent anarchy and chaos. Social and political governance became imperative to prescribe and enforce order for the preservation and advancement (yoga-kṣema) of collective life.
The concept of Rajadharma, or the duty of a ruler, has its roots in the ancient Bhāratīya civilisation. The seers of that time envisioned a system where temporal power (kṣatra tejā) was subservient to and tempered by spiritual power (Brahma tejā) to serve the desired purpose. This was a response to the overwhelming nature of political governance and its susceptibility to corruption, thus leading to the development of the concept of Rajadharma or Dandanīti.
The legendary Bhāratīya ruler Śrī Rama exemplified political power exercised with spiritual wisdom, portrayed as an ideal of a welfare state in the epic Rāmāyaṇa. Following Mahatma Gandhi, this concept is referred to as Rāmarājya, a Sarvodaya State aimed at the welfare of the entire cosmos. This welfare extends not only to specific sections of human society but encompasses the entirety of existence.
The Bhāratīya treatises on polity emphasise the role of the ruler in upholding Rajadharma. They stress the need for daṅda (punishment) and regulations for its implementation. Smooth governance requires norm prescription, adherence, enforcement, and punitive measures for violations. An authority of law is essential, but the person in authority, typically the ruler, must adhere to rules and regulations. The ruler’s duty, encapsulated in Rajadharma, entails serving as a preserver of order, subject to accountability and obligations.
Rājadharma operates within a cosmic sphere, sustaining the entire cosmos and its beings. It imposes desirable restraints on the public and rulers, emphasising duties and responsibilities over power and privileges. The ruler is viewed as both a servant and a master of the people, entrusted with protecting and serving them.
Furthermore, integrating political power (kṣatratejā) with spiritual wisdom (brahmatejā) ensures genuine welfarism, encompassing the material and spiritual well-being of the cosmos. This holistic approach transcends material welfare to embody spiritual fulfilment and universal harmony. Therefore, the ancient Bhāratīya notion of Rājadharmạ encapsulates the ideals of a welfare state, where principles of duty, responsibility, and spiritual wisdom guide governance. This concept, rooted in pursuing universal good, remains relevant and holds great potential for fostering harmony and prosperity in modern societies.
Author Bio: Dr. Vandana Sharma ‘Diya’ is an Assistant Professor, Zakir Husain Delhi College, University of Delhi. She is also a Member of the Central Board of Film Certification, Govt. of India and Fellow with Indian Institute of Advanced Study, Shimla and a Researcher with Kedarnath Dhama, Ministry of Culture. She is a Former Fellow of ICPR, ICSSR, Ministry of Education.
References:
[i] Yajurveda, 36.9
[ii] Atharvaveda 8.2.25
[iii] Arthashastra., 1.19
[iv] Manusmriti.,7.18
[v] Ibid, 1.4
[vi] Mahabharat., 7.58.115-6
[vii] Shukracharyaniti (Here the word Brahmin means the one who is established in Sattvic acts, thoughts, speech and ways of leading his life.)
Interview with Shri M. J. Akbar
Rami Niranjan Desai:
In your journalistic career and also in your role as the Minister of State, External Affairs, Govt of India, you have closely observed India’s relations with the Middle East. While the region has been a priority for India, there is a distinct change now, in India’s dealings with the region. What are the factors that contributed to this change?
You obviously saw the early developments being MOS external affairs on the different relationship building that India, sort of had with the Middle East. Even though the Middle East has been a priority for India, it seems like something changed. Can you take us through what the foreign policy change was and what contributed to this positive relationship that we have with the Middle East today?
MJ Akbar:
Let me start with a question, not an answer, right? What on Earth is the Middle East? I don’t raise it as a semantic question or a kind of peripheral banter; I raise it as a vital element of our understanding of this region. The moment we call it the Middle East, we are not looking at it from the perspective of the region. We are not looking at it from the perspective of Asia or even from the perspective of Africa. We are looking at it from the perspective of the colonial powers, primarily Britain, and then its successor power in the region, America. For them, it is in the middle of their east. If you want to call any region in Asia, the Middle East, then, actually, the only Middle East is India. So first, unless we clear these cobwebs that have been planted upon our brain and into our intellectual DNA by colonialism, we are not going to be able to see reality. Let’s call it West Asia, which is a far better term. It is a term that we have used with great consistency, and I hope that this term will also find genuine currency even in the countries of the region we are addressing.
From the Indian perspective, the most crucial development under Mr. Modi’s prime ministership happened, like most great changes, almost surreptitiously. He redefined the arc of the neighbourhood. He also redefined what a neighbour is—not simply an accident of geography but defined by reach. As an illustration, today, we have, from across India, over a thousand flights to the Gulf every week. And on these flights, it isn’t easy to find a seat!
On the other hand, there is not a single flight to Pakistan. So, who is India’s neighbour? This consciousness that you mustn’t get trapped by geography and that you must rise above geography and see things and create new realities is one of the most significant achievements of Prime Minister Modi, which happened stage by stage, step by step. The starting point was when he became the Prime Minister and visited the UAE, becoming the first prime minister in about 36 years to do so. What was India doing for three and a half decades before that? And even before that, the visits were cursory rather than substantive. Mr Modi has turned it into a substantive relationship. These are all Arab nations, after all. He pulled the Gulf, and Egypt is part of the Gulf. And here again, I’ll offer you a reality that corrects our perspective’s dimensions. It takes less time to reach Dubai from Delhi than it takes to reach Cairo from Dubai. That’s how close we are to the Gulf. And from Mumbai, it is even closer.
That is a change of perspective because Mumbai and Dubai have a vast gulf of water between them. And from there, we went to take the sequence forward, right up to Indonesia. And that’s the arc of the new neighbourhood, which has become one of the most productive elements. It is a very sustained and sustainable relationship, built on the most valuable part of any bilateral or multilateral relationship—the economic welfare benefits to the people. Geopolitically, we broke through a kind of wall constructed between us by a particular neighbour in the name of religion, and this process has been very beneficial to us. From COVID onwards, it began to stutter a little but will revive consciously because the base is too strong. What has been built has already achieved a great deal. And I think we will see a continuation of what has been created for the region’s benefit. Eventually, the world understands that very positive new geopolitics is in play.
Rami Niranjan Desai:
Absolutely. You made some fascinating points. Stability in West Asia is hugely essential for us to continue this engagement. How do you see the conflict between Israel and Hamas playing out. Do you think it will remain limited or in the long run, do you see it becoming a larger issue which can spread to Iran. How do you think India is dealing with it?
MJ Akbar:
A point I missed in my opening remarks was that the most interesting part of Prime Minister Modi’s foreign policy was that this whole bridgehead created with West Asia was not at the expense of our relations with Israel. And it is unique. It is remarkable, and they recognised it. The region accepted India’s outreach because they knew that Prime Minister Modi was not building any relationship that would be hostile to their cause. India is a power. India is a regional power. A regional power has and must have the capability of having relationships across binaries. Regional conflicts do not break our relationships. We have very good relationships with Iran. At that time, Iran was not the closest of friends with the UAE and the Saudis, but we built excellent relations with both and continue to do so. And this has been recognised in the region and is a significant contribution to them and the issue. So, India can create a balance in a challenging region. As far as the conflict goes, let’s score and underscore one fact—flames don’t have a geography.
Just as we speak, Hassan Nasrallah has threatened Cyprus because he says that the IDF—the Israeli Defense Forces, are training in Cyprus for a possible invasion of Lebanon. This war is not going to end so soon. There are many new discordant elements that one hears from within Israel. Recently, the IDF made two important statements. One is that Hamas is not going to be defeated so easily because it is an ideology. It is not simply an army. It’s equivalent: Can you defeat the communist ideology even if you defeat the PLA? So, that’s a very wise position to take. They’re asking for not an end to conflict but a restructuring of war objectives. War objectives are always the most essential elements of war and must be rational. They have to reflect a sense of justice against justified grievance. They cannot become irrational.
Right. And I think these are the difficult questions now bothering the region. Horrific scenes are being played out every day from the Palestinian camps and the tragic death of young people in the Israel Defense Forces—young people on both sides of the conflict. The old never die from the decisions they make. I think India should have a significant role in resolving this crisis.
Rami Niranjan Desai:
You also said there’s no end to this because it’s like an ideology. Hamas is an ideology. Where can India fit in? India also depends on West Asia for its energy requirements. Hence, the stability of this region is hugely important to India. You also said that Prime Minister Modi has navigated in such a way that he enjoys the trust of all parties involved. So what can India do to ensure that there is stability in this region and that its impact on trade and energy flows to India is not hampered?
MJ Akbar:
The trade and energy flows will continue irrespective of the conflict because trade is not one-sided. The energy producers need a market as much as the market needs the energy. So, that is not the top of my concerns. The concerns are really of destruction, where there should be positive construction. What can be created by amity, and I am not even using the term harmony, is far more valuable than what can be achieved by rampant destruction. That’s the lesson of every war because it is essential to remember that we are not in the age of empires. The Age of Empires collapsed with the end of colonialism. I know that neocolonialism has not ended, but colonialism has, and we are in the age of the nation-state. We are in the epoch of the nation-state. While this has not meant the end of war, internationally, there is more rational behaviour. Achieving a sustainable settlement of the region should be the only focus of all powers with a positive and beneficial attitude towards the region. War is no longer going to be fought in compartments. War is now an open battle. It affects everyone and everything. Governments also know this because a few governments are now beyond accountability. People extract a price if their affairs are not managed well. It affects all of us, and it is in the common interest of the rational world to find solutions to the conflicts in the region because I think Israel is also paying a very, very heavy price
Rami Niranjan Desai:
The international credibility of Israel is at an all-time low at this point. Do you think releasing the hostages held by Hamas would lead to a less assertive response from Israel, or do you think that will not change anything?
MJ Akbar:
You can’t clap with one hand. I mean, quid pro quo. That is the basis of all negotiations. There is no one-way offer. It won’t happen however much you may ask for it or however much you may wish for it. Both sides understand it. When we talk of the hostage crisis, why do you forget that a large number of hostages have been released? So, there have been deals before. Why should there not be a deal again? The problem, in my view, is the forces that have a vested interest in continuation of war. I’m not naming them because I don’t think guilt is only on one side.
Rami Niranjan Desai:
How can India play a role if the conflict remains localised and does not explode into something larger?
MJ Akbar:
The only nation that can become a bridge is one with pillars on both sides. India has pillars of goodwill on both sides, so why not India? However, this is a role that the US wants to play and has allotted to itself. But the Americans should also understand that this is an area in which India can help. The US could reach out to us. We do have a very good relationship with the White House, and here I mean a White House, irrespective of who’s the occupant of the White House.
Rami Niranjan Desai:
Correct. But as of now, what has been India’s position in the Israel-Hamas conflict?
MJ Akbar:
We have a position which is also the position of most nations, and that is to find a credible route map to a resolution. Do not treat conflict as an end in itself. What India is saying is in the interest of both sides. That is why it has credibility. India has no vested interest in the conflict but has a very strong vested interest in peace and in conflict resolution. But of course, it would require the acceptance of the US and perhaps Europe for India to find a place in the evolution of this unfortunate tragedy.
Rami Niranjan Desai:
Also in West Asia, one of the things that remains significant apart from what is happening right now is that we all talk about terrorism and it being a global security threat. Do you think India has some sort of leverage to combine its strength with West Asian countries to find some amount of cooperation to combat terrorism effectively?
MJ Akbar:
That fact is now non-negotiable. Terrorism as a weapon has been advertised as the weapon of the weak, and so on. Terrorism, however, is not acceptable, because the world has enough forums and enough space to move forward through the basis of negotiations. I once was asked by the Pakistani High Commissioner to Delhi as to when will there be peace talks. And I told him there will be peace talks when there is peace. You can’t have peace talks, at least in our bilateral situation, when you think that you can ignite terrorism as a form of blackmail. The Indian people are not ready to accept blackmail. So, abandon it. Why don’t you see the history of the last 50 years? There was a region called East Pakistan, which was as Pakistani as West Pakistan. Fifty years ago, it went through a cataclysmic liberation movement. After 50 years, it was not that relations with India instantly became better; they did not. There were dictators who continued to have a vested interest in conflict with India. But when Dhaka understood that it could gain far more from a positive relationship with India, look how well the relations have flourished. Look how Bangladesh has gained in terms of water, in terms of Farakka, in terms of all the neighbourhood requirements, the ten flights a day or more, perhaps now between India and Bangladesh. People are coming in, and people are benefiting. That is known as the reward of peace, which is the peace dividend. All we are asking is that every nation in the region recognise the enormity of the peace dividend and forget the very bloodstained returns of conflict.
Rami Niranjan Desai:
That’s so eloquently put. Even though we’re talking about West Asia, I’m always interested in Bangladesh. The kind of stability Bangladesh has had is because it had a stable government. It’s had Sheikh Hasina in the forefront. Pakistan doesn’t seem to have that. So is the expectation of peace too much to ask for?
MJ Akbar:
No, it’s not. While I have the greatest admiration for Sheikh Hasina, I have had the privilege of knowing her for a long while, when she was in a kind of isolation and in the opposition. What that Lady has gone through is a profile in courage and conviction and her own belief and ideals that is really, truly remarkable. The world should recognise that. What I’m also talking about is a national consciousness. And that national consciousness has existed in Bengal. So, Bangladesh has great projects with China. Well, it is an independent country. Why should it not? It is perfectly in its capacity and capability to exercise its will wherever it feels right. But today, the relationship between India and Bangladesh is crucial to the creation of economic growth advance in the whole region, our Northeast, Bengal and so on and so forth. All of it.
Rami Niranjan Desai:
Because we’re running out of time, I have a couple of questions that a lot of people here really want to know about. One is that we’ve been hearing a lot about the Petro deal. What do you think is happening there? How do you think it’s going to manifest? It’s likely that the Saudis will engage in the sale of crude oil in currencies other than the dollar. How do you see this playing out?
MJ Akbar:
It’s not just Saudis; it’s Russians. It’s the Chinese. It’s India. All countries are trying to find value in their currencies. The domination of one currency benefits only the owner of that currency. And this is taking a position not from a sense of hostility, but from seeking economic justice. If India and Iran, for example, can find value in each other’s currencies, well, why not? After all, currency is only an illusion. I mean, any rupee note is only as powerful as you believe it to be. A dollar is only as powerful as you believe it to be. When empires collapse, the first thing that collapses is the currency. So, every country would like to strengthen its currency. In a multipolar world, you will also need multipolar currency platforms.
Rami Niranjan Desai:
What if the US influence on the region were to decline? How would that impact the geopolitical landscape?
MJ Akbar:
I don’t think it would require an interest because again, influence is something that I have to also participate. If you’re going to influence me, I would also like to see some value in that inference. It’s all a question of negotiated value.
Rami Niranjan Desai:
How do you view the Chinese overtures in the region?
MJ Akbar:
China will play to its ability to try and expand its influence. It’s a kind of a quasi-China zone as far as it can, that is within its rights to do so. The interesting development, of course, is that after the break between China and Russia, after ’69, the return of the Moscow-Beijing partnership was a very, very vital element of the present-day world power equations. As we speak, President Putin has gone to North Korea and signed an agreement. North Korea is not an insignificant military power. The Chinese simultaneously have gone to South Korea, perhaps to allay fears that the Russian president’s visit to North Korea is not to be treated as hostile, but as part of equations that are important. As we speak, the Chinese are reaching out to Malaysia, and Putin has gone to Vietnam. So, old relationships are being revived, new relationships are being created, and new dimensions are being created to existing relationships. As the world is preparing for some degree of confrontation, I am not going to be so dramatic as to say it’s preparing for a World War. But it’d be more accurate to say that preparations are being made for a world confrontation.
Rami Niranjan Desai:
And the theatre of that would be?
MJ Akbar:
The theatre of that would be very, very visible. India, as the First Nation to declare independence from colonialism, has a profound historical significance. It has managed to retain the strengths of its unique ability not only to retain independence but to provide leadership to independent nations, which accumulates their influence without sacrifice of their independence.
Rami Niranjan Desai:
Thank you, Mr. Akbar. That gives us such a great overview of what is happening and what we can expect, even though, like you said, we don’t want to be too dramatic. But doesn’t look like a very bright sort of situation. But let me just end this short conversation with my last question to you. There’s been a lot of interest in IMEC, but it appears to be right now, in the back burner. How do you see the India Middle East Economic Corridor (IMEC).
MJ Akbar:
The IMEC is one of the ideas that has been on the table for a long while. Gwadar is another route, which is a parallel corridor. This is inception, early days. And these are ideas. These ideas first have to reach critical mass before they become a reality. Of course, that is the interesting part of international diplomacy. And you know, between the conception of an idea and the birth of an idea, there can be a long gap.
Brief Bios:
MJ Akbar: Shri MJ Akbar is the author of, among several titles, Tinderbox: The Past and Future of Pakistan. His latest book is Gandhi: A Life in Three Campaigns.
Rami Niranjan Desai: Rami Niranjan Desai is a Distinguished Fellow, India Foundation. An alumnus of King’s College, London she has degrees in Anthropology of Religion and Theology. She has been actively involved in research, fieldwork and analysis of conflict areas, with a special focus on the North East region of India for over a decade.
Transnational Jihad in West Asia and North Africa
كُتِبَ عَلَيْكُمُ الْقِتَالُ وَهُوَ كُرْهٌ لَكُمْ ۖ وَعَسَىٰ أَنْ تَكْرَهُوا شَيْئًا وَهُوَ خَيْرٌ لَكُمْ ۖ
وَعَسَىٰ أَنْ تُحِبُّوا شَيْئًا وَهُوَ شَرٌّ لَكُمْ ۗ وَاللَّهُ يَعْلَمُ وَأَنْتُمْ لَا تَعْلَمُونَ
Warfare has been prescribed for you, though it is repulsive to you. Yet it may be that you dislike something, which is good for you, and it may be that you love something, which is bad for you, and Allah knows and you do not know.
Surat Al Baqara : 216. سورة البقرة : ٢١٦
Introduction
Deaths from terrorism are now at their highest level since 2017- 8,352 in 2023, a 22 per cent increase from the previous year.[1] While ISIS, al-Qaida, and their affiliates have been very active, the major contribution to the death toll was from Hamas. The attack against southern Israel on October 7, 2023, by Hamas and ten other Palestinian armed groups, including the Islamic Jihad, Mujahideen Brigades, Al Nasser Salah al Deen Brigades, etc, has left thousands of dead, destroyed Gaza, and caused a human tragedy of colossal proportions. It has also acted like an adrenaline shot for reinvigorating transnational jihad.
Post October 7, 2023, the two main Jihadi configurations of the Islamic State (ISIS) and al-Qaeda have rejuvenated their subsidiaries, branches, and affiliates and are using the Palestinian cause and alleged human rights abuses in Gaza as the prime platform of their messaging, which aims at expanding their global threat potential. Similarly, the Hamas-Israel conflagration has given impetus to Iran’s Axis partners to invigorate their grid of militias in Iraq, Syria, Yemen, and Lebanon, showcasing Tehran’s strategic influence both in its environs and globally. Christopher Wray, the Director of the FBI, while testifying to the Senate Intelligence Committee in December 2023, spoke of a ‘heightened threat environment’ after October. Earlier, in March 2024, General Michael Erik Kurilla, Commander of the United States Central Command (CENTCOM), observed that the capabilities of ISIS and al-Qaeda, and their affiliated groups, especially ISIS- Khorasan had escalated considerably.[2] The Israel-Hamas conflict, which is now in its 8th month, shows no signs of abating, despite horrific collateral damage and international opprobrium. The current global scenario will certainly throw up substantial challenges for counterterrorism agencies worldwide as jihadi groups will undoubtedly exploit the political fractures and hostilities that have become marked not only in the West Asia and African regions but also in the US, Russia, Europe, and South Asia, leading to proxy war scenarios, wherein counterterrorism initiatives suffer due to mistrust and political intransigence.
Unsurprisingly, 2024 started on a bloody note. On January 3, 2024, ISIS’s affiliate ISIS-Khorasan, attacked the commemorative ceremony marking the killing of the erstwhile IRGC head, Qasem Soleimani, in Kerman, Iran, which killed over 103 people. The same group was responsible for an attack on a Roman Catholic church in Istanbul, killing one person, and the March 22nd attack on the Crocus City Hall music venue in Krasnogorsk, Moscow Oblast, Russia, killing over145. The attacks were all acknowledged by the ISIS mouthpiece Al Amaq News Agency, which also published laudatory messages from other ISIS branches and affiliates from West Asia and Africa. The reach and connections of the group with others in West Asia and Africa have raised blinking red lights, and an assessment of this threat perception is required not only for the security of the West Asia and North Africa (WANA), but globally.
There are now several red flags about possible terrorist attacks, especially in WANA, and about cross continental linkages with south and southeast Asia and the Caucuses. The maps below show the areas, and linkages will be discussed below.[3]
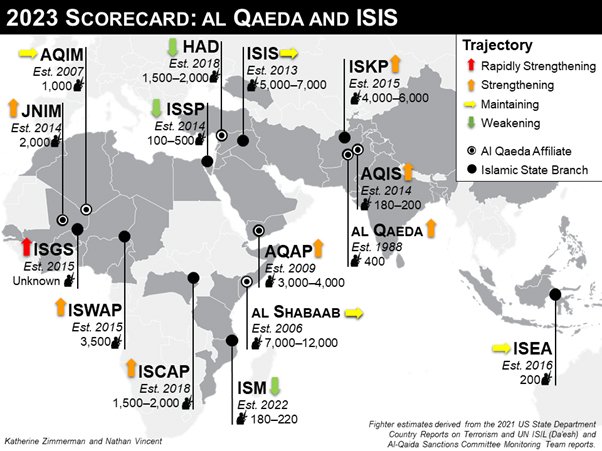
As can be seen, the Salafi-jihadi threat has spread its tentacles around West Asia, Africa, and Asia. They have exploited local conflicts, co-opted local warlords and organised crime syndicates local conflicts and have used extortion and intimidation, apart from radicalisation. to strengthen popular insurgencies which are supportive. These groups have been wildly successful in Africa, where a series of coups have destabilised the region, and seriously hampered counterterrorism operations.[4]
The Taliban takeover in 2021 has provided sanctuary in Afghanistan for training recruits from Africa, West Asia, and South Asia and for arms collection from the withdrawing US forces. This was due to the respite from counterterrorism actions due to a severe breakdown of all government institutions and political and inter-communal conflagrations.
The Libyan situation continues to be grim, with a four-cornered internal insurgency raging, and the situation in Sudan has gone seriously downhill over the past few months due to the conflict between the Sudan Armed Forces (SAF) and the Rapid Support Forces (RSF) escalating in Khartoum, destabilising government control and impacting fragile areas like Darfur, where mass killings and displacement have led to reports of ethnic cleansing.
In Syria, President Bashar Assad has managed to maintain the integrity of his country and the border; the Sykes Picot line remains intact. The central military conflict is now between the Syrian government and Turkish forces and factions within Syria. The conflicts continue to provide an optimum environment for Jihadi groups, which, although weakened, are by no means vanquished. The situation is similar in Iraq, and the Jihadi Salafi groups in the Levant have the potential to create local and global problems.
In 2023-2024, it has been seen that Jihadi Salafi groups, while focussing on the immediate areas of the Islamic world, have not lost sight of the more distant prospects, as evidenced by the Crocus Hall attack in Moscow, several attacks in Europe, and attempts in India and the USA. Post October 7th, there is a real and present danger from a terrorist act, as can be seen from the map of recent incidents given below.[5]
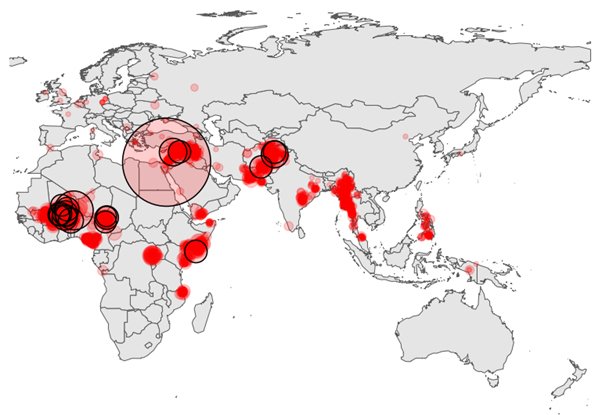
In this article, the transnational links of al-Qaida, ISIS, and other Salafi-Jihadi groups will be discussed, followed by a discussion on Iran’s “axis of resistance” and its burgeoning impact globally, and not just in the West Asian region.
The Global Reach of al-Qaeda: Networks and Allegiances
To revisit old history, Osama Bin Laden (Yemen/Saudi), Abdullah Azzam (Saudi), and Ayman Zawahiri (Egypt) and their cohorts, who had formed the Maktab al Khidmat, had been removed from Sudan at the encouragement of the US, as they had earned the ire of the Saudi Royal family, who did not want a Salafi contingent in a neighbouring country. The group was transported to Afghanistan by the US, and Nasrullah Babar, the then interior minister of Pakistan, introduced them to Mullah Omar, the Emir of the Taliban, to fight against the Soviet army. The Taliban, under the instructions of the Pakistani ISI, was told to extend them logistical and material help and fight under their guidance.
Post the Soviet defeat in 1988, the Maktab al Khidmat morphed into the al-Qaida, ostensibly for the spearheading of a global Islamic revolution that would eventually culminate in a Caliphate. The founders envisaged it as a “base” to which many other Jihadi outfits, like those from Uzbekistan and Xinjiang, and even the Rohingyas would join with the Ansars (foreign fighters). The al-Qaida was to stay as honoured guests of the Taliban and would acknowledge the Emir of the Taliban to be the Emir ul Momineen, the supreme leader of an Islamic community. The initial political motivations of settling the founders of al-Qaida, to use them against the Soviets, spectacularly backfired, leading to the bombing of the Kenyan embassy in August 1988, on the attack on USS Cole on October 12, 2000, in Aden, Yemen, and of course, the 9/11 attacks in the US.
Despite severe degradation following Operation Enduring Freedom, launched after 9/11, al-Qaida, after a short sabbatical, has emerged on the Global Jihadi map and has evolved into a decentralised network, with numerous affiliated groups across the globe pledging allegiance to its leadership.
Al-Qaida leadership
Al-Qaida faced a severe leadership crisis after the assassination of Osama bin Laden in 2011, followed by Anwar al Awlakki in Yemen in a drone strike (2011), and Nasir al Wuhyashi, who had been anointed as the next head of al-Qaida by Osama bin Laden, was also killed in Mukalla, Yemen, in 2015. The mantle of leadership did not fall on Ayman Zawahari, who was relegated to the position of group ideologue and notional Emir, with little control over day-to-day functioning or operational details. Operations and finances were being managed by Saif al Adel, based in Tehran, and Qassim al Raymi, the then head of the AQAP. They had envisaged and operationalised an attack against the US Naval Air Station Pensacola in Florida in December 2019. The leadership council of the al-Qaida, including Zawahiri, was unaware of the operation, which caused considerable disarray in the Group’s central administration. Though he was nominally named the Emir of al-Qaida, his killing in a drone strike in the posh Wazir Akbar Khan area of Kabul in 2022 made little difference, and he has not been eulogised by the al-Qaida social media or print mouthpieces.[6]
Saif al Adel @ Mohammad Salah al Din Zaidan
Seif al Adel, an erstwhile special forces officer from Egypt who had been closely associated with Osama bin Laden in Afghanistan and Pakistan, was earlier arrested when he, along with Osama bin Laden’s sons, Saad and Hamza, escaped to Iran. He was released through the efforts of Nasir al Wuhyasi, the then head of the AQAP, along with other cadres (see photo below), but refused to leave Teheran. Adel, who was reportedly close to the slain IRGC chief Qassem Soleimani, claimed that it would be better to have an al-Qaida presence in Iran, as there was a commonality of interest between the Iranian regime and the group regarding the “distant enemy,” the USA. His reluctance to leave Iran created dissent with the al-Qaida Central branch based in Afghanistan. Still, he bolstered his position by getting Tehran to have a line of communication with the al-Qaida, and by resonance with the Taliban. It needs to be noted, though, that the Iranian regime has refused to acknowledge the presence of Saif al Adel or other al-Qaida cadres in Iran. Also, it is significant to note that most attacks in Iran have been perpetrated by the ISIS, barring those by Baloch groups like Jaish e Adl in Sistan Baluchistan Province, and not by al-Qaida.
Saif Al Adel established control of the AQAP-al Qaida in the Arabian Peninsula and co-opted its leaders. Saif al-Adel won the support of the Yemeni branch and used it to increase his direct influence in Syria. He created a new al-Qaeda group in Syria called Hurras al-Din (the Guardians of Religion) and established a channel for transferring funds and fighters from Yemen to Syria. This group worked along with the Jabhat ul Nusra, headed by Mohammed al Julani, the main AQ branch in Syria. These groups continue to be active in Syria under the tutelage of Adel. While counter-terrorism attacks by the US have degraded ISIS in the Levant considerably, the AQ fronts have been more insidious, won over allies from the Syrian armed opposition, and their cadres are actively involved with local governance in the large tracts of ungoverned areas in Syria, which also helps in getting funding through ill legal oil trades.
Situation with the AQAP
Meanwhile, in Yemen, Saad bin Atef al Awlakki, an acolyte of Saif Al Adel, was appointed as head in May this year following the assassination of the previous head, Khalid Batrafi. Awlakki is Yemeni and has made a public call to the provinces of Abyan and Shabwa in south Yemen to resist any overtures from the UAE government. With his ascension, reconciliation with the UAE and Saudi Arabia seems remote. Of great concern is that the AQAP has considerable heft in the provinces of Abyan, Shabwa, Marib, the port of Mukalla, Hadramawt and north Aden. AQAP has targeted armed groups backed by the UAE, such as the Southern Transitional Council, Security Belt, Shabwani Elite, and Shabwah Defense Forces, stating that Emirati mercenaries needed to be eliminated. Due to Saif Al Adel and the current AQ policy, they have no significant differences with the Houthis, who are acting as proxies of Iran, and since 2022, there have been no attacks by AQAP on the Houthis.
Saif Al Adel established control of the AQAP (al-Qaida in the Arabian Peninsula) and co-opted its leaders. Saif al-Adel won the support of the Yemeni branch and used it to increase his direct influence in Syria. He created a new al-Qaeda group in Syria called Hurras al-Din (the Guardians of Religion) and established a channel for transferring funds and fighters from Yemen to Syria. This group worked along with the Jabhat ul Nusra, headed by Mohammed al Julani, the main AQ branch in Syria. These groups continue to be active in Syria under the tutelage of Adel. While counter-terrorism attacks by the US have degraded ISIS in the Levant considerably, the AQ fronts have been more insidious, won over allies from the Syrian armed opposition, and their cadres are actively involved with local governance in the large tracts of ungoverned areas in Syria, which also helps in getting funding through ill legal oil trades.
Al Shabaab and its importance
The above development in Yemen needs to be assessed against the backdrop that the Al Shabaab, an affiliate of al-Qaida, has gained considerable ground in Somalia, even within the northern region of Puntland, and the port of Bossaso, which is on the other side of Aden across the Gulf of Aden, a main international shipping route. Harakat al Shabaab al Mujahideen, known as Al Shabaab (the youth), was formed by Aden Hashi Farah Aryo, a mujahideen trained in Afghanistan. It gained traction during Somalia’s civil war in the 1990s as an alliance of shari’a courts and local armed groups which gained power and territory during the 2006 Ethiopian invasion. It once controlled over 40% of the territory, including parts of Mogadishu. It is now headed by Ahmed Diriye, also known as Ahmed Umar Abu Ubaidah, who was involved in the West Mall attack in Kenya in 2013 and is a UN-designated terrorist.
Al Shabaab is showing remarkable resilience to counterterrorism initiatives by the African Union’s Transition Mission to Somalia (ATMIS) and Somali government forces and has often routed them with high levels of attrition. The ATMIS is winding down operations in Somalia, and it is apprehended that the resulting power vacuum will allow the Al Shabaab greater latitude. The group has now established some bases in Puntland, one area where international piracy initiatives were launched. The Al Shabaab leadership leaders have been covertly funding Somali pirates for revenue generation. Of global concern is the deal that the Houthis are forging with Al Shabaab for the supply of weapons. The two groups have an understanding, despite sectarian differences, that arms supply such as surface-to-air missiles and attack drones to the al Shabaab would seriously deteriorate the security scenario around the Gulf of Aden and Bab el Mandeb, the main shipping routes, especially for oil.[7]
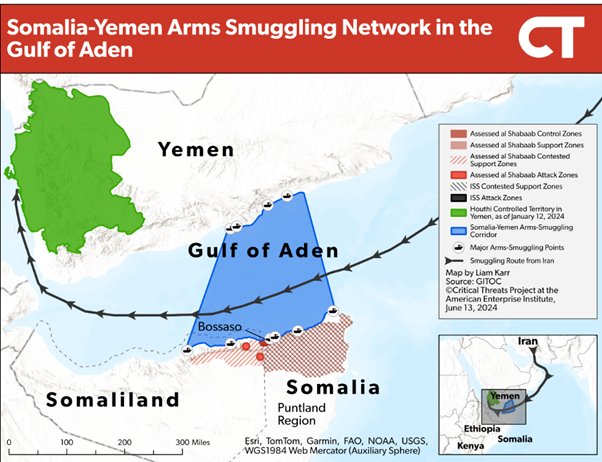
Jama Nasr al-Islam wal Muslimin-JNIM
The JNIM, which translates as the Group for the Support of Islam and Muslims, is a prominent jihadist organisation in West Africa which was formed in March 2017. The JNIM is an amalgamation of several regional extremist groups, including Al-Qaeda in the Islamic Maghreb (AQIM), Ansar Dine, the Macina Liberation Front, and Al-Mourabitoun. The Group’s formation was publicly announced by its leaders in a video message, signalling a unified front for Al-Qaeda. This was evidenced in the joint statement given out after the Hamas attack on Israel, which fulsomely praised Hamas and called for further attacks on Jews. The Group, which has expanded its reach across the Sahel region, including Mali, Niger, and Burkina Faso, aims to overthrow local governments and establish an Islamic state governed by Sharia law. It has engaged in kidnapping for ransom, attacks on military and civilian targets, and collaboration with other jihadist factions. The Group is closely affiliated with the AQAP and the Central AQ in Afghanistan.
The leader of JNIM is Iyad Ag Ghaly, a Malian Tuareg who previously led Ansar Dine. He was instrumental in removing French and other foreign troops from Mali. Under his command, the Group has pursued an agenda of implementing strict Sharia law for which he has formed various sub-units operating semi-autonomously across Mali, Burkina Faso, and Niger. This decentralised approach allows JNIM to adapt to local conditions and maintain resilience, and it has shown considerable success against counter-terrorism efforts.
The Group has claimed responsibility for the attack on June 11, 2024, that killed over 100 Burkina Faso soldiers in Mansila area near the border with Niger. The site of the attack was close to the borders with Niger and Mali; both countries host insurgencies linked to both Al Qaeda and Islamic State. In another major attack on a gendarmerie and civilian auxiliary post in Burkina Faso on May 5, 2024, and a Nigerian army base on May 20 2024, over 100 people were killed. The brutality of the attacks has caused military forces to abandon the targeted bases, creating a power vacuum which the JNIM is filling. The political fallout has been a drift of the weakened governments towards Russia, causing consternation amongst the US and allies about potential strategic losses over political heft and valuable natural resources.
Call for Jihad
Saif Al Adel, the Emir of the Al Qaida, called (June 2024) upon “the loyal people of the Ummah interested in change to go to Afghanistan, learn from its conditions, and benefit from the Taliban’s experience. This call was issued by the as-Sahab media, a mouthpiece of the organisation, titled “This is Gaza: A War of Existence, Not a War of Borders.”[8]
The call makes it clear that al Qaida has established bases in Afghanistan, and believe that they have political immunity there. His call for’ Hijra’ is reminiscent of the early 1990s. He further adds that all Islamic people should strike to cause maximum pain against ‘Zionist” targets around the world.[9]
Simultaneously, the AQAP has launched a new online anti-West propaganda campaign called “Inspire Tweets” which exhorts the Ummah that jihad is the only solution, the need of the hour is for supporters to engage in various types of attacks including bombings, armed assaults on unexpected targets, and strikes on train stations and airports to retaliate for killing Muslims. Additionally, the campaign calls on al-Qaeda supporters to carry out cyberattacks to hurt western economies. Earlier in December 2023, tweets asked followers to use ‘Open-Source Jihad (OSJ)’ material titled ‘The Hidden Bomb,’ directed at lone wolves, and groups of supporters, which had guidelines and tips on how to make IEDs, bypass standard security measures in United States airports etc.[10]
This call for Hijra and the open-source jihad needs to be seen in tandem with a United Nations Analytical Support and Sanctions Monitoring Team report dated January 29th that states that the al-Qaida has opened eight new training camps, five madrasas, a weapons depot and safe houses in Afghanistan, that are used to facilitate the movement of its members to and from Iran and other areas in West Asia and Africa. The report further reiterates the close connection between the Taliban and al-Qaida.[11]
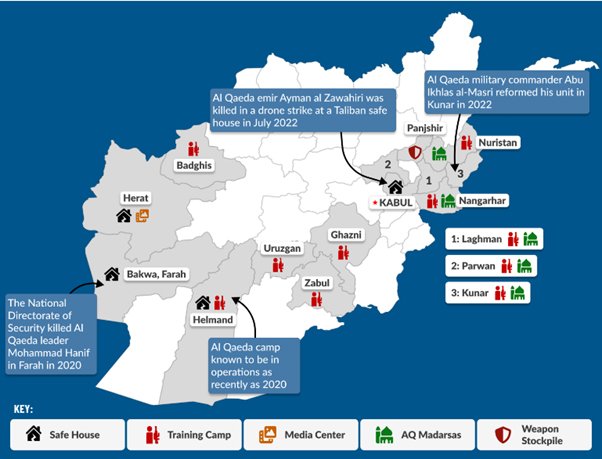
Afghanistan and Transnational Jihad
With al-Qaida opening doors for foreign jihadis, the pathway has also been facilitated for ISIS cadres, especially as ISKP has become one of the most active vilayats of ISIS. This, combined with the anti-migration policies of the EU and USA, will likely cause a reverse flow into Afghanistan. Several Jihadis from various countries are now seen in Afghanistan, an eerie recall of the early 1990s.
Over the last few decades, several jihadist organisations have tried to get a global outreach, be it the AQ, AQAP, Al Shabaab, or the various factions of ISIS. ISKP has been spectacularly successful, as witnessed in the latest attacks in Iran, Turkiye, and Moscow. But unlike other groups, the ISKP has no stable space in Afghanistan and is in constant battle with the Taliban and AQ, both for control of territory and drug trading routes. Since 2022, the Taliban, with some international help, has been systematically degrading the ISKP. On its part, ISIS, in the August 28, 2022, issue of its Pushto magazine Khorasan Ghag, claimed that its reduced activity was because the group’s Emir -Shahad al Muhajir had decided on a “strategic silence” policy. The policy was soon revised, and the group set up the Azaim Media Foundation, which publishes in Arabic, English, Pushto Urdu, Russian, Swahili, etc. The online messages and tweets are getting responses from all over West Asia and Africa for recruitment, funding, and logistic support.
Hence, it is seen that despite claims by the Taliban that no foreign terrorist group would be able to function on Afghan soil, the quality and number of attacks have escalated since 2022 end. The ISKP, from its tenuous holdings in Afghanistan, has set up recruitment and financial networks in West Asia, Europe, Somalia, and the US and has emerged as an integral part of the transnational jihad and one of the main contributors to ISIS’s terrorist profile.
ISIS in Syria and Iraq
On March 23, 2019, the coalition forces, led by the USA, claimed that they had liberated the final stretch of territory controlled by ISIS in Baghuz, Syria. But though ISIS has lost Mosul (Iraq) and Raqqa (Syria) and has been degraded in Syria and Iraq, the group is far from moribund, has a network of agents and sleeper cells in those countries, and has systematically set up branches all over the globe. In the Levant, counterterrorism pressure has degraded the Islamic State’s global senior leadership, including those leading efforts to conduct attacks in Europe. However, despite significant losses among senior ranks, the group has adapted by decentralising its command structures. The name of the current Caliph -the fifth one- Abu Hafs Al-Hashimi Al-Quraishi, was announced in August 2023 by his spokesman Al-Ansari. He has, however, ostensibly for security reasons, remained undercover, and his real identity is unknown, which has led members to question his credentials. In November 2023, the pro-ISIS Bariqah News Agency hinted that an audio or video message by the Caliph might not be ready for quite some time, indicating that he will remain undercover. Some reports have suggested that he has travelled from Yemen to Somalia.
This appears to be a real possibility, as for the present the ISS- Islamic State in Somalia, is the most active branch, which has strong links with ISKP. Following the January 4, 2024, audio message by ISIS Spokesman Abu Ḥudhayfah Al-Ansari, in which he pledged to escalate attacks across all regions in support of the “Muslims” in Gaza., there has been a quantifiable increase in violence and threat perceptions in the region has escalated. Currently there are an estimated 2500 Islamic State fighters in Syria and Iraq— more than double estimates from late January.
There have been around 69 confirmed attacks by the Islamic State in central Syria till June 2024.The attacks in Badia, in March this year resulted in the deaths of at least 84 Syrian soldiers and 44 civilians. This was followed by attacks in the desert area of Homs, with over 15 soldiers of the Syrian armed forces loyal to President Bashar Assad killed. The scale of violence against the security forces was alarming as ISIS cadres stormed regime outposts, ambushed patrols, capturing and executing soldiers and capturing arms. There were also targeted attacks on the US backed Syrian Democratic Forces (SDF). Armed forces abandoned posts, leaving large swathes of the country without security cover. The UN assessed in January this year that the IS had established an operational hub in the Badia desert in Central Syria, but opined that it was likely that Syrian Government and Russian forces would neutralise/ contain it soon.[12]
The situation is similar in Iraq. Of note is the attack on May 13, 2024, this year on military outposts in eastern Diyala and Salahuddin provinces, where a commanding officer and several soldiers were killed. These attacks in Syria and Iraq suggest that the rural areas continue to harbour militant cells, and that the earlier declaration of victory over ISIS in Iraq and Syria by the U.S was a little premature. Problems, including sectarian divisions and proxy wars, have undeniably undermined the Iraqi government’s counter terrorism efforts and enabled the ISIS’s revival. The Iraqi government has also been hamstrung by the U.S. partial withdrawal of forces in 2021, but the armed forces are rallying around, and have conducted several counter-terrorist operations. In March 2024 , the Iraqi forces launched a notable offensive, that resulted in the death of a prominent ISIS leader, Samir Khader Sharif Shihan al-Nimrawi who was the point person for transfer of funds arms and cadres between Syria and Iraq.
Moreover, Prime Minister Mohammad Al-Sudani’s government has had to battle crippling sectarian polarisation that occurred after the US intervention in Iraq in2003. This problem is still some way before resolution, and added to the current geopolitical turmoil in the region stemming from the ongoing Israel–Hamas war has undermined regional stability and encouraged ISIS’s resurgence in the region.
ISIS in North Africa
Over the last few years, successful counterterrorism operations and the rigid enforcement of strict national anti-terrorism legislation, coupled with innovative deradicalisation and rehabilitation programmes, have diminished the threat posed by ISIS in Egypt. The Egyptian government has invested in several development and infrastructure policies in the area where the local branch of the Islamic State, also known as vilayat Sinai or Ansar Bayt al-Maqdis (ABM) is active. However there still are some active cadres who periodically attempt to attack the Security forces, especially around the Sinai. The last violent clash between the Egyptian army and ABM was in 2022 near the Suez Canal. Still, the terrorists were soon overpowered, a tribute to the excellence of the Egyptian intelligence service, the GIS (General Intelligence Service). It needs to be pointed out that the GIS, which has excellent HUMINT, had informed Mossad about the possibility of a major Hamas attack across the Gaza Strip in September this year.
In Libya, jihadist groups are facing several challenges due to sustained counterterrorism attacks against their positions. In southern areas like Fezzan, clashes between the Islamic State and Al-Qaeda are helping security forces. On its part the ISIS, exploiting the political and economic predicament in southern Libya is cooperating with tribal elements involved in smuggling, human trafficking and illicit trade, which helps the group to be financially stable and helps recruitment. According to a recent report by Europol, Syrian mercenaries – often with radicalised profiles are being brought into Libya– by Russia (through the Wagner Group), who might pose additional security risks to the country.
Morocco has not had an Islamist-inspired attack since 2018 but remains vigilant over the offline and online threat of violent extremism. The Moroccan intelligence has prevented several attacks and dismantled jihadist cells that operate in cyberspace. The Moroccon deradicalisation and reintegration programmes, such as ‘Moussalaha’ (‘Reconciliation’), have proved to be very successful and can serve as a blue print for other countries. It has benefited hundreds of jihadists, especially foreign terrorist fighters (FTFs) returnees. The situation in Algeria is much the same, and due to tight security mechanisms and reconciliation policies that allow jihadists who surrender to security services, which would give them information, to receive amnesty and economic assistance.
Tunisia continues to face several terrorist-related challenges. Jihadist groups such as Katibat Uqba Bin Nafi (KUIN) and Jund Al-Khilafa (JAK), which, though weakened – are active in the mountainous areas along the Tunisian-Algerian border. They pose the risk of guerrilla /lone wolf attacks. Also, Tunisian rehabilitation programmes are not as well received or as exhaustive as the Moroccan programmes, and hence, Algiers continues to face problems with the foreign returned fighters.[13]
Map of Jihadist groups in Africa
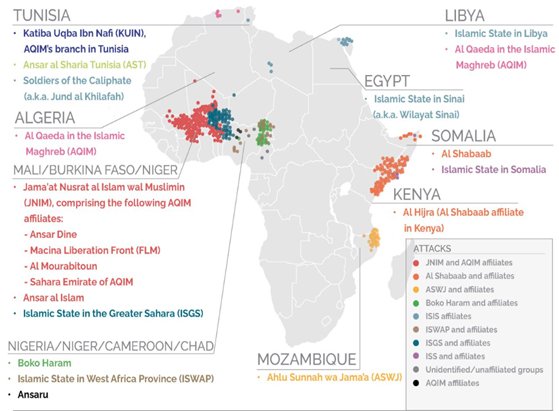
Jihadi groups in Africa
Violent conflict is one of the main factors driving terrorism, with over 90 per cent of attacks and 98 per cent of terrorism deaths in 2023 taking place in countries in conflict; all the African countries impacted by terrorism have been involved in prolonged armed struggles. In the current global scenario, the epicentre of terrorism has shifted from West Asia and North Africa into sub-Saharan Africa, mainly in the Sahel. Around 59 per cent of all fatalities due to terrorist attacks are from the Sahel, with significant contributions from Burkina Faso, Mali, Mauritania, Nigeria, Niger, and Somalia in the east. These conflicts are important as they often morph into proxy wars with powerful countries, which signal a lack of ethics. These proxies usually result in debilitated governance, mass migration, hunger, and uncontrolled climate change, leading to coups with uncertain futures. Apart from endangering relations with neighbouring countries, many nations with coups have withdrawn from international bodies such as ECOWAS and local peacekeeping forces.
The nexus between organised crime and terrorist groups in the Sahel is marked by illegal gold mining and oil trading, apart from human and drug trafficking, kidnapping and extortion, and livestock hustling and activities such as cattle and livestock rustling.[15] Notable examples of such groups are the JNIM, the Boko Haram in Nigeria, etc, which are affiliated with al-Qaida and the Islamic State vilayats in Africa. These are usually active in the same areas, frequently leading to violent clashes between the groups. While these clashes have a debilitating effect on the social fabric, resulting in mass migration and human rights abuses, they help counterterrorism initiatives by local governments and international agencies. Criminal activities ensure that these groups in the Sahel are reasonably well funded and able to support the central leadership, including proactive branches like the ISKP.
ISIS DRC
According to U.S. Intelligence, the senior ISIS leadership is of the view that Africa is an area where they should invest time and energy, as the continuing conflicts there make for a permissive environment. The I.S. announced the launch of the Islamic State Central Africa Province (ISCAP) in April 2019 as a unified structure between ISIS-Democratic DRC and ISIS-Mozambique. The Allied Democratic Forces (ADF), a Ugandan Muslim insurgent faction active in eastern Congo since the 1990s, had committed a wave of brutal attacks on civilians in late 2019 and killed around 850 people last year, according to U.N. figures. The ADF, which gained prominence for attacking Christian communities, has morphed into the ISCAP, which is now trying to expand its sphere of influence. The group is said to be involved in diamond and gold smuggling and has efficient financial and recruitment networks.[16]
Ugandan and DRC armed forces have been launching attacks on ISCAP positions, but the group has shown considerable resilience. On January 24th this year, ISCAP launched a major attack in Ngite, in the territory of Beni, in resource-rich North Kivu province, which borders Rwanda, causing security forces to withdraw from the area. ISCAP has entrenched itself in the region, which is on the route of transporting Cobalt and diamonds. In December, the group was accused of two attacks in western Uganda in which 13 villagers were killed. The DRC, which continues to have a low-intensity conflagration with Rwanda, is conducive to I.S. growth due to its internal turmoil. The ISCAP could cause severe problems in the future and impact WANA.
Islamic State in Somalia (ISS)
ISIS’s financial strength and sustainability depend on maintaining safe havens and global connectivity. Hence, the group’s leadership has prioritised independent revenue streams for its vilayats by establishing regional control hubs called the Administration of Distant Provinces (ADP), which later (2022) evolved into the General Directorate of Provinces (GDP). ISIS in Somalia (ISS) has generated millions of dollars from extortion, supporting piracy and exploiting the Somali financial system to launder money through hawala and mobile money transfers. The ISS emerged as ISIS’s primary revenue generator, earning approximately USD 6 million. Hence, its local office in al-Karrar, Somalia, has been made the regional General Directorate of Provinces (GDP) with control over Yemen, Kenya, etc. Given its importance in the financial system of ISIS, the US initiated a counterterrorism initiative to kill the head of the GDP in Somalia, Bilal al Sudani, in 2023, which was successful. Abdul Qadir Munim, an influential cleric, has been appointed in his place, and he wields considerable influence in ISIS, next only to the Emir. Recently, the al Karrar Office routed funding through various hawala in the region, including South Africa, and has used South Africa-based banks to transfer funds from the GDP to other ISIS vilayats. Reports suggest that funding and logistic help have been given to the ISKP from the al Karrar office.
Conclusions
- The Hamas attack on October 7th has reinvigorated the global Jihadi scenario.
- Groups affiliated with Iran, including the Hamas, Palestinian Islamic Jihad, Hizbollah, and the Houthis have stated that they will attack Israeli interests globally, and will also attack US and Western interests for supporting Tel Aviv.
- There is a definite understanding between Iran and the Al Qaida, which can be seen with all the branches and affiliates of the group. Sectarian differences have been subdued for joint action against the US and Israel.
- The Emir of the Al Qaida, Saif al Adel, has asked all Jihadis to go to Afghanistan for training. He has also called for reviving Open-Source Jihad for facilitating group and lone wolf attacks.
- This is important for India, as the Lashkar-e Toiba, Pakistan, has traditionally been cooperating with the al Qaida.
- This call is also important as anti- migration policies are now coming into play, and this could cause a flow of militants back into Afghanistan, and through porous borders into Pakistan, which could have security implications for India. This would energise the Al Qaida in the Indian sub-continent-AQIS, which has a number of Indian members.
- The Gulf of Aden which is a crucial choke point in the energy supply routes is being targeted by the Houthis, who have attacked ships in the area, and have even reached up to Socotra Island, which is a matter of great concern for India.
- Houthis are cooperating with Al Shabaab, an Al Qaida affiliate in Somalia, and have reached an agreement to share weapons and logistic support. Al Shabaab has funded Piracy for revenue generation. Arms and cadres reaching Somalia could easily be transported to the Indian sub-continent.
- ISIS and Al Qaida rivalry is wreaking havoc in Africa. Both groups are trying to generate revenue through illegal utilisation of the natural resources there.
- Proxy wars and power plays are being enacted in Africa which will have global ramifications.
To sum up: there are flashing danger signals following the Hamas attack and its aftermath. There is an immediate need for greater security measures coupled with serious initiatives for confidence building and integrating Muslim groups.
To quote Rumi- “Out beyond the ideas of wrong doing and right doing, there is a field. I’ll meet you there.”
Author Bio: Ms. Prabha Rao is a Distinguished Fellow, India Foundation. She is also the Executive Director, South Asian Institute for Strategic Affairs and Distinguished Scholar at the Institute for Defence Studies and Analyses, New Delhi. She is a former IPS officer from Karnataka cadre (1982 batch) who went on a deputation to cabinet secretariat and served in several locations abroad. She also runs an NGO — Encourage India, for skilling victims of trafficking and left-wing extremism.
References:
[1] https://www.economicsandpeace.org/wp-content/uploads/2024/02/GTI-2024-web-290224.pdf
[2] https://www.foreignaffairs.com/united-states/terrorism-warning-lights-are-blinking-red-again
[3] https://www.aei.org/articles/the-state-of-al-qaeda-and-isis-in-2023/
[4] https://www.aei.org/articles/the-state-of-al-qaeda-and-isis-in-2023/
[5] https://www.christiandaily.com/news/africa-surpasses-middle-east-as-the-epicenter-of-terrorism.html
[6] https://sanaacenter.org/publications/analysis/
[7] https://x.com/criticalthreats/status/1801641885577957775
[8] https://x.com/CJBdingo25/status/1804433672705090031
[9] Longwarjournal.org/archives/2024/06/al-qaeda-leader-calls-foreign-fighters-to-afghanistan.php
[10] https://www.counterterrorismgroup.com/post/the-hidden-bomb-inspire-releases-footage-detailing-household-bomb-making
[11] https://www.longwarjournal.org/archives/2024/05/architect-of-doha-agreement-wrongly-claims-al-qaeda-in-the-indian-subcontinent-has-been-dismantled.php
[12]https://x.com/GreyDynamics/status/1806206097876775146ref_src=twsrc%5Egoogle%7Ctwcamp%5Eserp%7Ctwgr%5Etweet
[13] https://www.ispionline.it/en/publication/jihadism-in-north-africa-a-resilient-threat-in-times-of-global-crises-132039
[14] https://www.realinstitutoelcano.org/en/report/riders-on-the-storm-north-africas-pathways-to-resilience/
[15] https://www.economicsandpeace.org/wp-content/uploads/2024/02/GTI-2024-web-290224.pdf
[16] https://home.treasury.gov/system/files/136/Fact-Sheet-Countering-ISIS-Financing-2-27-24.pdf
Turbulence in West Asia: Implications for India
American activist and political philosopher Martin Luther King famously argued, “Injustice anywhere is a threat to justice everywhere.” A parallel can also be drawn regarding the outcome of injustice, which is conflict. It is a fact that conflict anywhere poses a threat to peace everywhere. This ‘threat to peace’ becomes particularly relevant and urgent when conflict arises in a nearby region, often described as an “extended neighbourhood”. This situation holds true for all countries, and India is no exception. The developments in West Asia over recent months have raised significant concerns for policymakers in New Delhi. West Asia has never been a metaphorical island of peace. Protracted conflicts, artificial state formations, colonial legacies, and sectarian tensions have been defining features of the region. Recent incidents such as the terrorist attack on Israel by Hamas, Israel’s ground offensive in Gaza, missile exchanges between Iran and Israel, and attacks on shipping vessels by Houthis in the Red Sea have escalated tensions in West Asia to new levels.
The region has always been susceptible to the influence and interference of external powers, with its history shaped more by states outside West Asia than within it. Since the third decade of the twentieth century, the US became a significant player in the region, defining its trajectory. While it continues to exert influence, its role as the foremost external actor has significantly diminished, opening the door for other players like Türkiye, Russia, and China to assert themselves. Their presence has had a profound impact and thus demands serious scholarly attention. For India, the region holds critical importance due to its energy security, diaspora, remittances, regional aspirations, and external security concerns.
This paper will first define the concept of the extended neighbourhood in the context of India and then examine the roles of the US, Türkiye, Russia, and China in shaping the politics of West Asia. The next section will address the pivotal issue in West Asia, the Israel-Palestine conflict. Subsequently, it will delve into its current dynamics and discuss the major challenges and opportunities in West Asia for India.
West Asia as India’s Extended Neighbourhood
West Asia is considered by many scholars as part of India’s extended neighbourhood. The concept of an “extended neighbourhood” encompasses India’s projection of power through cultural and ideological ties, alongside military strength and economic influence. Over time, this concept has expanded to encompass India’s geographical boundaries, extending to the east, south, north, and west. This broader perspective is often described as a comprehensive “360-degree vision” of India’s opportunities beyond South Asia, which some perceive as economically and politically limiting. During the first NDA government under Atal Bihari Vajpayee, the idea of the Extended Neighbourhood gained prominence, emphasising that India’s interests and engagements extend well beyond South Asia to include both its immediate and additional neighbours.[1] Subsequent governments have continued to endorse this concept, with the Modi government particularly enhancing efforts to bolster India’s influence in its extended neighbourhood.[2]
Tracing the Role of US in West Asia
The United States’ involvement in West Asia has been complex and varied, driven by a combination of geopolitical objectives, economic interests, and ideological considerations. While US engagement in the region dates back to the early twentieth century, it became significantly more pronounced during and after World War II. A major catalyst for US involvement in West Asia was its strategic imperative to secure access to oil reserves. Consequently, strong alliances were forged with oil-rich nations in the region, including Saudi Arabia and Iran. Throughout the Cold War, West Asia was viewed by the US as a crucial theatre in its global struggle against communism.
A pivotal event in US-West Asia relations was the establishment of the state of Israel in 1948. The United States played a key role in facilitating Israel’s creation and has maintained a robust partnership with the nation ever since. However, in recent years, there has been a gradual reduction in US involvement in the region. This shift in policy has been influenced by factors such as domestic political pressures, evolving global dynamics, and a reassessment of strategic priorities in West Asia. Furthermore, the United States’ decreased engagement in West Asia has created opportunities for other countries like China, Russia, and Türkiye to increase their influence and fill the void left behind.
Türkiye as a New Player in West Asia
Another key actor that has emerged as critical in West Asian affairs is Türkiye. Over the last two decades, President Recep Tayyip Erdogan has worked to establish Türkiye as a significant force in West Asia, exerting power and pursuing its own geopolitical objectives. During the past decade, Türkiye’s involvement in West Asia has been characterised by confidence, aspirations for regional dominance, and evolving partnerships. Türkiye’s pursuit of EU membership, with limited success, has prompted increased engagement in the West Asian region.
A pivotal aspect of Türkiye’s role in West Asia has been its involvement in the Syrian crisis. Türkiye has supported multiple opposition factions in their resistance against Syrian President Bashar al-Assad, providing military and logistical support. Another significant factor contributing to Türkiye’s influence in West Asia has been its connections with Islamist organisations. Under Erdogan’s leadership, Türkiye has cultivated relationships with Islamist governments and groups in the region, such as the Muslim Brotherhood in Egypt and Hamas in Palestine.
Russia’s Engagement with West Asia
For nearly a decade, Russia has been competing with the US to regain influence in West Asia, a position it hasn’t held since the Soviet era. In 2015, Russia significantly escalated its involvement in the region by supporting Syrian President Bashar al-Assad’s government during the country’s devastating civil war. This support from Russia and Iran effectively prevented the collapse of the Assad regime and thwarted Western efforts, particularly those led by the US, to establish a pro-Western government in Syria.
Russia’s strategic sale of advanced weaponry, including fighter jets and air defense systems, not only generates revenue but also enhances Moscow’s leverage and influence in nations that purchase these systems. Iran, Syria, Iraq, and Egypt are among the significant customers of Russian defense equipment.[3]
Although Moscow has refrained from forming official alliances in West Asia, it has sought to gather and cultivate strategic allies that advance its objectives, including mitigating its global isolation resulting from the conflict in Ukraine. Moscow and Iran have strengthened their relationship, particularly in the realm of defense. Iran has been supplying Moscow with significant unmanned combat aerial vehicles for its conflict efforts in Ukraine.
Facing economic isolation due to sanctions from the US, EU, Japan, and others, Russia has been cultivating relations with West Asian countries to access essential supplies like microchips and gain entry into their financial and commercial markets.[4]
Russia’s once amicable ties with Israel have noticeably deteriorated, with the country now publicly supporting Hamas. This stance reflects Russia’s pronounced pro-Palestinian position in the ongoing Israel-Palestine conflict, part of a broader geo-strategic plan to cast the US, Israel, and the West as responsible for the situation while positioning Russia as a peacemaker. Russia’s West Asia policy aims for strategic alignment with its interests while avoiding unnecessary commitments.[5]
China as the New Peace Broker in West Asia
China’s engagement in the region can be traced back primarily to the Iran-Iraq war, during which it supplied weapons to the combatants. However, after the war, its influence in the region waned. As part of its foreign policy, China has traditionally refrained from interfering in the internal affairs of other nations. Nevertheless, there has been a noticeable shift in its foreign policy approach in recent times. At the 2022 Boao Forum for Asia’s annual conference, Xi Jinping introduced a new initiative called the Global Security Initiative (GSI). The GSI statement marks a departure, advocating that China should be seen not just as a provider of goods but also as a peacemaker, emphasising its strategic importance alongside its economic significance. This initiative also indirectly challenges the rationale behind initiatives like the Quad and the Indo-Pacific strategy.[6]
In 2023, Saudi Arabia and Iran announced the normalization of ties mediated by China, issuing a joint trilateral statement confirming an agreement between the Kingdom of Saudi Arabia and the Islamic Republic of Iran. The agreement focuses on resolving internal issues to ease tensions without external involvement, aligning with China’s alternative global security strategy. However, China’s mediation in the Riyadh-Tehran peace process is driven by strategic interests rather than purely altruistic motives, particularly given the Gulf’s significance to China’s economic and energy interests.
China has invested billions of dollars in Gulf projects to support its Belt and Road Initiative (BRI) and secures a substantial portion of its energy supply from the region. Despite sanctions, Iran remains China’s third-largest oil supplier, following Saudi Arabia. Joint ventures like Aramco-Sinopec further illustrate China’s efforts to meet its energy demands. China’s role as a mediator in the Saudi-Iran agreement underscores its strategic objective of using initiatives like the Global Security Initiative (GSI) to exert influence in West Asia as a counterbalance to the US.
It should be noted that, like other parts of the world, West Asia is also witnessing an ongoing power struggle between the US and China. The primary reasons for the US’s dominant presence in the region have been to protect Israel, combat terrorism, prevent nuclear proliferation, maintain military bases, and supply weapons to allies such as Saudi Arabia. The established diplomatic and political hegemony of the US is now facing a challenge from China’s increasing influence. The recent Saudi-Iran deal is a clear indication that China’s rising influence in West Asia will contest US dominance and its capacity to shape the region’s stability and politics.[7]
Israel-Hamas Confrontation and The Palestinian Question: The Elephant in the Room
The recent confrontation between Israel and the Palestinian Hamas Movement has once again drawn global attention to West Asia, an area fraught with ancient conflicts and complex geopolitical dynamics. The wars in this region offer valuable insights into the intricate political landscape that defines the area. The October 7, 2023 attacks by Hamas terrorists on Israel and Israel’s subsequent response highlight a shift in warfare dynamics—from traditional battles between national armies to prolonged engagements against non-state actors. It also underscores the ongoing challenges faced by Israel and the US in adapting conventional tactics to counter unconventional threats posed by groups like Hamas, Hezbollah, and the Houthis.
The current conflict between Israel and Hamas has debunked several misconceptions prevalent in the region. Initially, Israel’s ‘divide-and-rule’ strategy towards the Palestinians appeared effective until October 7, 2023, when the dynamics shifted. Despite deals struck with Hamas, Prime Minister Benjamin Netanyahu’s dismissal of the Palestinian Authority (PA) as negotiation partners underscored Israel’s evolving challenges. There was a prevalent belief that global interest in the Palestinian cause had waned, assuming Palestinians were too divided and oppressed to pose a credible threat to Israel. However, the escalating conflicts in Gaza have proven otherwise, reigniting hostilities and demonstrating that the Palestinian cause remains potent and capable of catalysing renewed violence in the region.
Moreover, the recent confrontations and the responses of Arab states, particularly the UAE and Qatar, have disrupted the previously calm relations that had developed between Israel and the Gulf states over the past decades. These relations were vigorously supported by the US and motivated by a shared concern over Iran’s influence. The 2020 Abraham Accords, signed between Israel, the United Arab Emirates, Bahrain, and Morocco, laid the foundation for a burgeoning regional security alliance. Discussions on normalisation with Saudi Arabia also indicated progress in this direction. However, the absence of Gulf states in recent events has left Israel and a US-led coalition to contend with Iranian proxies such as the Houthis in the Red Sea region on their own.[8]
India and West Asia: Challenges and Opportunities
India’s strategy towards West Asia has undergone significant transformation over the years. Following independence in 1947, India initially pursued a primarily geopolitical strategy focused on cultivating positive relations with Muslim-majority countries in the region to counter potential influence from Pakistan. Energy security was not a major consideration in India’s engagement with West Asia during this period, despite its reliance on the region for energy supplies.
However, starting from the 1970s, India’s approach to West Asia began to pivot towards economic concerns and energy demands. The oil crises of the 1970s and subsequent economic growth in the Gulf region prompted India to shift its diplomatic focus towards oil-rich countries in West Asia.
In the post-Cold War era, India’s foreign policy in the region evolved further, becoming more pragmatic due to economic reforms and advancements. Economic factors now play a crucial role, outweighing political rhetoric in shaping India’s strategy towards the volatile region. Since assuming power in 2014, the Modi government has prioritised West Asia, fostering high-level visits and expanding relations beyond oil to encompass defense, space cooperation, pharmaceuticals, infrastructure, and more. West Asia presents both challenges and opportunities for India, influencing its strategic engagements and economic interests in the region.[9]
India’s Contemporary Focus in the West Asian Region
India’s West Asia policy is built upon three key pillars: Gulf Arabs, Iran, and Israel. Notably, none of these three entities trust each other and often find themselves in conflict. Balancing relations among them has been challenging yet crucial for India’s national interests. Energy security ranks as a top priority for India, aiming to ensure a stable and reliable long-term energy supply. India has become the world’s third-largest consumer of energy and is poised to increase its consumption further in the coming decades. West Asian countries have traditionally been India’s primary suppliers of crude oil, with Iraq emerging as the largest supplier in 2023, followed by Saudi Arabia and the United Arab Emirates.
India views territories in West Asia, particularly the UAE, Saudi Arabia, and Iran, as preferred trading partners. Trade volumes between India and these nations have consistently risen. West Asian countries perceive India as a rapidly expanding economy capable of competing with major global economies. Currently, India is negotiating a Free Trade Agreement (FTA) with the Gulf Cooperation Council (GCC) to enhance economic ties with West Asian countries. India also seeks to attract Foreign Direct Investment (FDI) from wealthy Gulf nations, which have significant potential for investment across various sectors in India, yielding mutual benefits.[10]
In recent years, Israel has emerged as a crucial defense partner for India, with bilateral ties strengthening notably under the Modi government. India’s proximity and collaboration with Israel are also underscored by their participation in the newly formed regional group I2U2 (India, Israel, UAE, and US).
India and West Asian countries are increasingly concerned about the threats posed by Islamic extremism, terrorism, and maritime piracy. Consequently, they are focusing on enhancing military cooperation and collaborative efforts to combat these challenges. There is a growing apprehension regarding the escalation of criminal activities, illicit financial flows, and unlawful trafficking of weapons between the two regions.
India has entered into defense cooperation agreements with several countries in the region, including the United Arab Emirates (UAE), Oman, Qatar, and Saudi Arabia. These agreements aim to facilitate military training, joint exercises, cooperation in military medical services, collaborative development and production of advanced military equipment, as well as defense science and technology exchanges. Both India and West Asian nations have been affected by the recent increase in piracy incidents in the Indian Ocean, particularly in the Gulf of Aden. India considers the security of the Indian Ocean vital due to the large number of oil tankers that transit through these waters. Indian navy vessels have been deployed to deter piracy activities in the region.
Safeguarding the interests of the Indian diaspora, which comprises around nine million individuals, is a significant aspect of India’s strategic objectives in West Asia. The Indian diaspora in the Gulf region plays a crucial role in contributing to foreign currency reserves. India is the world’s leading recipient of remittances, as reported by the World Bank on Remittances and Migration. According to the Reserve Bank of India, from 2014 to 2020, the Gulf region accounted for an average of 28 percent of total remittances sent to India. The United Arab Emirates (UAE) and Saudi Arabia are the primary sources of these remittances due to the substantial Indian expatriate communities residing there.[11]
India’s outreach to West Asia has shifted in recent years from bilateral engagements to sub-regional and regional interactions, adopting new strategies. One notable initiative is the India Middle East Europe Economic Corridor (IMEC), a connectivity project introduced in 2023 during the G20 summit in New Delhi, involving the UAE, Saudi Arabia, India, and several Western nations. IMEC aims to revolutionise integration across Asia, Europe, and West Asia by enhancing efficiency, reducing costs, securing regional supply chains, increasing trade access, fostering economic cooperation, creating employment opportunities, and cutting greenhouse gas emissions. Despite the ongoing Israel-Hamas conflict delaying its implementation, member nations remain committed to the project. For example, Prime Minister Narendra Modi and UAE authorities signed a framework agreement during Modi’s recent visit to the UAE to facilitate IMEC’s progress.
Furthermore, India seeks enhanced cooperation with the Gulf Cooperation Council (GCC), offering more opportunities for Indian companies with substantial investments in the region. Over the past decade, China’s economic and strategic influence has grown significantly in West Asia through initiatives like the Belt and Road Initiative (BRI), while Pakistan’s influence has waned due to internal economic and political challenges. India faces new challenges as regional players pursue their own “Act East” strategies and seek strategic alignments that avoid taking sides between China and India. Amidst competition among regional powers and the global repercussions of conflicts such as Israel-Hamas and Israel-Iran, West Asia will continue to play a pivotal role in shaping India’s foreign and security policy framework.
Countries in the region look to India to play a larger role globally, commensurate with its status as a major power, and trust its prudent and benevolent foreign policy approach grounded in strategic autonomy. Therefore, rather than merely facilitating dialogue among conflicting parties in the region, India could consider taking concrete actions and acting as a mediator to mitigate disagreements. Deploying Special Envoys to assess the situation and reassuring allies in West Asia that New Delhi is prepared to take proactive steps would be highly beneficial. While success is not guaranteed given the complexity of regional issues, making efforts to defuse tensions is inherently valuable.
Effectively leveraging soft and smart power is crucial to harness the region’s historical ties. This approach aligns with the objectives of regional powers like Saudi Arabia and the UAE, which are pursuing significant socio-economic reforms alongside more inclusive, secular, and humane policies. A recent example is the donation of land for and opening of a Hindu temple in Abu Dhabi. To promote stakeholder engagement through reciprocal investments in key economic and business sectors, focused efforts are essential.
Addressing the growing challenges posed by non-state actors and terrorist groups demands a robust and comprehensive strategy in intelligence, security, and defense. India’s strong track record of secularism and pluralism can serve as a counterbalance to aggressive actions by members of organizations like the Organization of Islamic Cooperation (OIC), such as Pakistan. India must also remain vigilant regarding potential shifts in West Asia’s geopolitical landscape, such as the emergence of CRIPTAQ (China, Russia, Iran, Pakistan, Türkiye, Afghanistan, and Qatar), which could significantly impact India’s regional outreach efforts.[12]
The frequency and intensity of Houthi rebel attacks at sea, spanning from the Northern Indian Ocean to the Red Sea, have significantly increased. Recently, Indian commercial ships have been targeted in these attacks. Consequently, due to the Red Sea situation, more than 90% of India’s cargo bound for Europe, the US East Coast, and North Africa is now being rerouted through the Cape of Good Hope route. Freight costs have surged substantially, sometimes up to six-fold, affecting all shipments, particularly those involving low-value, high-volume, and perishable items. Given India’s heavy reliance on crude oil and petroleum imports, this crisis could adversely impact efforts to stabilise fuel prices. Currently, India has issued a Navy warning and deployed destroyers and warships to patrol the Red Sea, Gulf of Aden, Central, and North Arabian Sea. The Modi government has instructed the Indian Navy to take proactive measures and has intensified maritime surveillance.
Conclusion
Conventional wisdom suggests that for a state to achieve global power status, it must transition from moral principles to pragmatic strategies, abandoning ethical considerations. However, India, as a civilisational state, has demonstrated that it can maintain moral high ground even in high-level negotiations. This stance is evident in India’s West Asia policy over the past decade, where the country has made significant strides. While upholding humanitarian causes such as Palestinian statehood, refugee issues, peaceful dispute resolution, adherence to international laws, and providing humanitarian aid during disasters, India has also pragmatically prioritised its own interests. This includes maintaining a de-hyphenated approach between Israel and Palestine, supporting Israel against terrorism, balancing relations between regional rivals like Iran and Saudi Arabia, advocating for the Chabahar port project in Iran despite US sanctions threats, and pursuing mini-lateral initiatives such as the I2U2 group.
West Asia is undergoing profound changes, and recent events have shattered the perception of regional stability, alliance formations, and geopolitical dynamics. The region lacks a dominant authority and is in a state of transition. Notions of a post-American West Asia and the strength of newly formed alliances have given way to a more complex reality where conflicts persist and the Palestinian cause gains prominence. West Asia remains a challenging and dynamic geopolitical puzzle that requires deeper understanding and challenges conventional wisdom. The threats of Islamic terrorism, instability, piracy, and oil price shocks continue to pose challenges for India as it aspires to become a Vishwa Guru. Therefore, India must remain vigilant, proactive, and pragmatic in navigating the complexities of West Asia.
Author Bio: Dr. Pavan Chaurasia is a Research Fellow at India Foundation. He obtained his M.Phil and PhD from the Centre for West Asian Studies, School of International Relations (SIS) at JNU. He was awarded the Junior Research Fellowship (JRF) by the University Grants Commission (UGC) from 2018 to 2023.
References:
[1] David Scott (2009) India’s “Extended Neighborhood” Concept: Power Projection for a Rising Power, India Review, 8:2, 107-143.
[2] Baldev Nayar and Thazhar Paul, India in the World Order: Searching for Major-Power Status (Cambridge: Cambridge University Press, 2003).
[3] https://www.gisreportsonline.com/r/russias-middle-east-resurgence-here-to-stay/
[4] https://www.washingtoninstitute.org/policy-analysis/how-middle-east-became-arena-putins-power-struggle-us
[5] https://www.internationalaffairs.org.au/australianoutlook/decoding-russias-position-in-the-israel-hamas-conflict/
[6] Rajagopalan, R. & ORF. (2022). China’s Xi Proposes Global Security Initiative. Policy Commons. Retrieved from https://policycommons.net/artifacts/2437268/chinas-xi-proposes-global-security-initiative/3458879/
[7] Saudi-Iran Peace Deal: Changing Dynamics of West Asia – Defence Research and Studies (dras.in)
[8] https://boundlessoceanofpolitics.co.in/2024/05/07/the-shifting-dynamics-of-west-asia/
[9] https://www.orfonline.org/expert-speak/evolution-india-west-asian-policy-57176
[10] https://economictimes.indiatimes.com/news/economy/foreign-trade/hope-india-gcc-fta-becomes-a-reality-very-soon-official/articleshow/101699298.cms?from=mdr
[11] https://www.academia.edu/101696365/Continuity_with_Changes_Indias_Policy_towards_West_Asia
[12] https://www.impriindia.com/insights/indias-with-west-asia-under-pm-modi/
Implication of Energy Transition on West Asian Stability
Energy is the lifeblood of any economy. Throughout history, wood and coal were the primary fuels that powered societies. However, the discovery of oil, due to its efficiency and ease of transportation, revolutionised the energy landscape, positioning oil as the dominant energy source. The increasing pace of industrialisation and the World Wars intensified the race to secure energy resources, making energy security a pivotal element in global politics. With soaring global demands and a finite supply, oil, often termed ‘black gold,’ acquired immense strategic value. Consequently, ensuring reliable access to sufficient and affordable energy became a cornerstone of national strategies worldwide.
In recent years, global conversations have increasingly centred on collective action to address the climate crisis. A critical step in this direction has been the call for a shift to cleaner and greener energy sources. There is near-unanimous agreement on transitioning from non-renewable to renewable energy resources, prompting most nations to develop and implement comprehensive energy transition plans.
In the West Asian context, this transition is particularly significant due to the region’s status as a major oil and gas rentier. Home to some of the largest reserves of oil and natural gas, West Asian economies are heavily dependent on energy-based export revenues, profoundly influencing governance and societal structures. Unlike the scarce nature of oil and natural gas, renewable energy sources are abundant. This could reduce the global relevance of West Asian oil and gas rentiers and significantly impact regional stability.
Despite the slow and uncertain pace of the energy transition, the strategic importance of energy resources and the historical geopolitics of oil and gas raise significant concerns about the transition’s impact on West Asian geopolitics and stability. This article examines these concerns by first providing an overview of the West Asian energy landscape and the region’s oil geopolitics. It then explores the broader geopolitics of the energy transition, focusing on how these changes may affect peace and stability in West Asia. Particular attention is given to the roles of climate technology and critical mineral supply chains in shaping the future geopolitical dynamics of the region.
West Asian Energy: Stocktake and Aspirations
West Asia holds a pivotal position in the global energy landscape, producing nearly 30% of the world’s oil[1] and possessing 48% of global oil reserves.[2] Key oil producers in the region include Saudi Arabia, Iraq, the United Arab Emirates (UAE), Iran, Kuwait, Qatar, and Oman. The hydrocarbon sector is vital to these economies, comprising 87% of Saudi Arabia’s export revenues, 95% of Iraq’s, 90% of Kuwait’s, 81% of Qatar’s, and 60% of the UAE’s. This underscores the significant role oil and natural gas play in influencing the economic stability and prosperity of West Asian nations.
However, when the global call for addressing the climate crisis by reducing greenhouse gas emissions was given, some of the key West Asian oil-producing countries responded positively knowing fully well that the first step would be to reduce and eventually shift from oil to cleaner and greener energy sources. With regards to the net zero target pledges, West Asian oil-rentiers to have committed themselves in policy documents include UAE (by 2050), Oman (by 2050), and Saudi Arabia (by 2060). Other states such as Kuwait and Bahrain have pledged to reach the net zero target by 2060.[3] On the other hand, while Iran, Iraq, and Qatar have not declared net zero targets, Qatar aims to reduce its greenhouse gas emissions by 25% by 2030.
UAE’s renewable energy endeavours include designing Masdar City – an environmentally sustainable city, multiple solar parks, including Noor Abu Dhabi Solar Park and Mohammed bin Rashid Al Maktoum Solar Park in Dubai, launching a wind energy programme, and upscaling green hydrogen production.[4] Kuwait also plans to award its first large-scale contract for a solar photovoltaic project by the end of 2024, along with projects in wind and concentrated solar power. Saudi Arabia has installed a renewable capacity of 2.8 GW, Qatar 800 MW, and Oman 500 MW.[5]
West Asian states are often referred to as rentier states due to their substantial dependence on external rents from oil. Scholars like Hazem Beblawi[6] argue that rentier economies shape the politics and societies of these states. In such economies, the government, as the principal rentier, becomes the most influential actor. With redistribution in the hands of the government, citizenship becomes a source of economic benefit. Since the government is not dependent on taxes, any act by the state is seen as benevolence and not a duty. The absence of taxes also reduces political participation by the citizenry. Although more recently, it has been observed that the oil-rentier states have been providing adequate public goods and services to their citizens, demanding accountability or transparency by the citizens continues to be disincentivised.
The hydrocarbon economy has deeply shaped the politics, society, and economy of West Asian oil-rentier states, granting rulers significant autonomy with minimal resistance from citizens. However, the global shift away from oil and gas could potentially disrupt this model. As the demand for these resources decreases, so too will the oil rents, forcing these states to either find new external revenue sources or transform their domestic economies. This energy transition could set off a series of transformative changes within these states, with far-reaching implications for regional stability.
Geopolitics of West Asian Oil
One of the most significant events that shaped contemporary world history was the discovery of commercial quantities of oil and gas in the Persian Gulf region. This discovery in a relatively fragile region prompted Western powers, beneficiaries of the first industrialisation phase, to maximise and secure their interests. In doing so, they introduced foreign influence into West Asia, exacerbating socio-political fissures within regional communities—a dynamic that continues to impact contemporary West Asian stability.
The first large oil deposit in the West Asian region was discovered in Iran in 1908. Through the Anglo-Persian Oil Company, the British were the first imperialists to capitalise on this opportunity. [7] The importance of oil in British strategic thinking became evident through their actions in Ottoman territories and the subsequent Sykes-Picot Agreement with France, which ensured access to rich oil fields and led to the arbitrary creation of nation-states.[8] By 1925, Britain, France, and the US had secured their oil interests in Iraq, discovering one of the world’s largest oil fields by 1927.[9]
Recognising the strategic and economic importance of oil, the US invested in oil exploration in Saudi Arabia in 1933. By the 1940s, America had secured its interests in Saudi oil through military and economic aid to the Kingdom.[10] In 1956, Egyptian President Nasser nationalised the Suez Canal, weaponising access to West Asian oil. This crisis altered the regional balance of power, leading to Nasser’s military defeat, Israel’s territorial changes, the withdrawal of France and Britain from the area, and a temporary rift between the US and other Western powers.[11]
In 1973, the support of Western powers for Israel during the Yom Kippur War led the Arab oil coalition to announce a total oil embargo. The ensuing ‘oil crisis,’ marked by a significant surge in oil prices, caused severe economic and political distress in the US. The embargo ended in mid-1974 after the US administration promised a more balanced approach to the Israel-Arab conflict, resumed arms trade with Saudi Arabia,[12] and Israel limited its territorial ambitions. This period also saw the birth of ‘Petrodollars,’[13] significantly contributing to the continuation of American hegemony.
Less than six years later, the Iranian Revolution of 1979 triggered a second oil crisis, marked by constrained oil supply and soaring prices. The revolution caused a collapse in US-Iran relations, prompting the US to rely on Saudi Arabia to meet its domestic demands and strengthen ties with Iran’s regional adversaries.[14] Over the next decade, two major wars occurred in the region: the Iran-Iraq War and the Gulf War (between Iraq and the US-led 42-country coalition, which started with Iraq’s invasion of Kuwait), both with significant implications for oil security. Although political differences were the primary triggers, securing oil reserves was a key focus of Iraq, the aggressor in both conflicts.
Over the years, US involvement and, arguably, interference in West Asia increased, leading to a growing dependence of most West Asian states on the US. While partially motivated by its strategic location, the importance of West Asian oil for the American economy, politics, and hegemony could not be discounted. However, the discovery of shale gas has reduced American dependence on West Asian oil, allowing the US administration more strategic and diplomatic flexibility. More recently, the Trump and Biden administration have signalled a shift in strategic priorities, moving away from West Asia and towards China.[15]
China, increasingly becoming a major West Asian oil importer, has deepened its ties with West Asian countries, even proposing a “Petro-Yuan” arrangement[16] to challenge the Petrodollar supremacy. West Asian oil rentiers like Saudi Arabia are looking to diversify their strategic alliances away from the American umbrella, with China presenting an attractive alternative. The closer the ties between China and the West Asian states, the higher the possibility of US-China rivalry playing out in the West Asian region, thus adversely affecting the already fragile state of regional stability. The emergence of states exercising strategic autonomy and possessing economic and political clout with a vision for energy transition, such as India, could also influence the stability in the region.
The pivotal role of oil in defining the regional balance of power in West Asia, shaping inter and intra-regional relations, dependencies, and vulnerabilities, is undeniable. However, while oil is unlikely to lose its significance in global politics in the near future, the energy transition could diminish its influence. This shift in focus towards factors that drive cleaner and greener energy could potentially increase the influence of states that control such factors. In West Asia, this transition could introduce new patterns of vulnerabilities, dependencies, and alliances, thereby reshaping the geopolitical landscape.
Geopolitics of New Energy Transition
Energy transition is an old phenomenon. Historically, dominant energy resources have shifted from wood to coal and, more recently, to oil and natural gas. Key drivers of these transitions have included growing populations, industrialisation, and the rise of emerging markets. Oil, in particular, became the most sought-after energy source due to its efficiency, ease of transport, and storage capabilities, while its limited supply granted geopolitical power to the few state actors controlling its production and distribution.
The current energy transition, however, is markedly different from previous ones. This new transition aims to move from oil to cleaner and greener energy sources such as solar, wind, geothermal, hydropower, ocean, bioenergy, and, to some extent, nuclear energy. There is an abundant supply for most of these, and states have different combinations of clean and green energy potential, which could reduce the energy dependence if not completely eliminate it. The primary challenge lies in developing the capacity to efficiently capture and utilise energy from these sources on a large scale. Thus, control over these capacities will shape the geopolitics of the new energy transition.
Energy transition is a process, and the end goal is several decades away. However, the process in itself has the potential to cause a strategic reshuffle of existing state relations. It could deepen state relations, increase competition, or forge new partnerships, and invariably, it could influence regional stability. Since energy plays a predominant role in inter- and intra-state relations within the West Asian region, any fundamental change will disrupt the status quo.
Decentralisation and Limited Stability
Renewable energy sources present unique challenges in control and distribution, as they rely on harnessing continuous energy flows rather than extracting finite stocks. These resources are more evenly distributed across geographies, promoting energy security for consumer nations by reducing dependence on external supplies.[17] The ‘prosumer country’ would build an energy model where energy production and consumption are broadly within the same territorial control.[18] This shift towards decentralised energy production and consumption within a country’s territory significantly departs from traditional energy models.
The energy transition poses a complex dynamic for oil-producing nations in West Asia. Historically, conflicts in the region have been driven by the desire to control oil resources. However, with the move towards renewable energy, such motivations may diminish. Yet, the critical role of oil in defining state economies and their relationships with citizens means that a transition could trigger domestic instability. The diminishing attractiveness of the oil industry will compel West Asian states to seek new strategic tools beyond oil price control to maintain their influence, posing a significant challenge.
The shift towards renewable energy in West Asia underscores the importance of political and economic diversification. As the region transitions away from an external rent-based economy, new sources of revenue and industries will emerge. Technology, offering strategic supremacy, will become a focal point, incentivising West Asian states to invest in research and innovation and attract international talent. Ensuring stability, security, and social goods will be crucial for retaining talent and foreign investment. Political diversification could facilitate smoother economic transitions and societal transformations, serving as a strategic tool to balance regional power dynamics.
The UAE’s gradual transformation and diversification have already presented a global model of success, with countries like Saudi Arabia, Qatar, and Kuwait following a similar path. For a region fraught with fragility, a balanced approach towards diversification and transformation triggered by the energy transition could mitigate further instability, even if it cannot usher in an era of regional peace.
Instability Curse of Green Oil
To leverage cleaner and greener energy, nations need affordable and reliable access to technology, raw materials, and finance.[19] Recent trends indicate that states are increasingly seeking control over these factors to gain geopolitical leverage. West Asian oil-rentier states, with their substantial sovereign wealth funds, are less dependent on external climate finance, limiting its geopolitical impact. However, for other developing states, climate finance sources can exert considerable geopolitical influence. In the context of West Asia’s energy transition, two critical factors—climate technology and critical mineral supply chains—will significantly impact regional geopolitics.
- Climate Technology – Harnessing clean and green energy necessitates a wide range of innovative technological products, including solar photovoltaic plants, wind turbines, batteries, and electric vehicles. Significant investments are also being made in the research and development of hydrogen-based economies to reduce greenhouse gas emissions and promote cleaner energy for domestic and industrial uses. The ownership of patents often determines control over these innovations. A 2021 International Energy Agency report highlighted a substantial increase in patents for low-carbon energy technologies between 2000 and 2019, nearly doubling those for fossil fuel technologies.[20] Leading players in patent portfolios for net-zero energy technologies include the US, China, Japan, South Korea, Germany, France, and the UK.[21] Amongst these, China holds the most extensive patent portfolio, with three times more patents than the US, in second place.[22] Its portfolio includes patents on core solar technologies, electronic vehicle batteries, and new and upcoming technology to harness hydrogen energy.[23] The centrality of the patents to the design and production of the technological product determines the power to monopolise the availability and affordability of the product. While China’s patent portfolio may have a mix of low- and high-quality inventions, it may still have a more significant say in monopolising the production of low-carbon and net zero-energy technologies.
- Critical Mineral Supply Chain – While cleaner and greener energy sources are abundant, the raw materials required for harnessing this energy are not evenly distributed. Production of low-carbon and net zero energy technologies requires varied combinations of critical minerals. These form the core raw materials for renewable power generation, power grids and other applications, including electric vehicles.[24] Essential minerals include lithium, nickel, cobalt, manganese, and graphite for batteries, rare earth elements for wind turbines and electric vehicle motors, and copper and aluminium for electrical networks and technologies.[25] The mining of critical minerals is spread across countries such as Indonesia, the Democratic Republic of Congo, the Philippines, Mozambique, Madagascar, Peru, Australia, China, Russia, and the US. However, China dominates the processing of these minerals. For instance, China processes more than half the global supply of rare earth elements, graphite, lithium, cobalt, and copper.[26] An interesting case is nickel, where although significant mining and processing occur in Indonesia, Chinese companies control 80% of the supply and 40% of raw mining, with Indonesian firms holding only 10% of the nickel mining in the country.[27] For any state envisioning a transition to cleaner energy, a reliable and affordable supply of critical minerals is essential to ensure energy security free from dependence and external interference. China’s monopoly on the supply chain—from raw mining to processing and refining—of critical minerals poses a significant geopolitical challenge. Control over these materials is fundamental for the production of most clean and green energy technologies, highlighting the geopolitical importance of securing access to critical mineral supply chains.
China’s increasing dominance in the current energy transition, with a monopoly over the most crucial factors responsible for the new energy landscape, has significant geopolitical implications. As China aims for energy security, its role in the West Asian context is becoming more pronounced. To harness the domestic cleaner and greener energy potential, the states in the region will inevitably deepen their relationship with China. However, for many smaller states, this has resulted in increased economic dependence and Chinese political interference. The West Asian oil rentiers, with their substantial sovereign wealth funds, are in a more secure position, reducing the possibility of being strong-armed by China. This dynamic underscores the complex geopolitical landscape of the energy transition in West Asia.
For a region that is looking beyond the American umbrella to exert its strategic autonomy, Chinese opportunities, including in the energy transition domain, are lucrative. However, given the American history in the region, strengthening relations with China makes the region vulnerable to the fallouts of US-China rivalry. This could lead to the deepening of existing political fissures in the region, making it more unstable.
Another potential source of instability could arise from the rivalry between oil and gas-producing states. Natural gas is considered to be a cleaner source of energy compared with oil. This would imply that in the initial phases of the energy transition, states could aim to increase the share of natural gas in their domestic energy mix while reducing the share of oil until greener energy sources can be used on an industrial scale. Within the West Asian region, Iran, Qatar, and Saudi Arabia could benefit more than other oil-producing states. This shift could alter the economic and political leverage within the region, exacerbating tensions. The fragile Saudi-Qatar relations and the long-standing Saudi-Iran hostility, despite recent normalisation efforts, could be further strained. The Sunni-Shia divide also adds to the complexity. With Iran potentially gaining more leverage due to its natural gas reserves, regional tensions could rise.
The use of nuclear energy as an alternative to hydrocarbon-based energy is also an area of concern within the region. With the regional hostilities, Iran’s nuclear program has already raised serious concerns for the regional and extra-regional actors. The insistence on increasing the share of nuclear energy to meet green energy targets, even if it is only for civilian use, particularly by Iran and Israel, could be seen with a sense of suspicion and concern by other actors.
Regionalisation
In 2018, the Indian Prime Minister had first proposed “One Sun One World One Grid (OSOWOG)” initiative, aiming to connect regional grids through a common grid for transferring renewable energy.[28] In 2021, Green Grids Initiative (GGI) was launched at COP26 in partnership with OSOWOG. GGI aims to construct infrastructure to connect energy-rich locations with continental grids, ensuring seamless transfer of renewable energy.[29] Australia is already working on providing solar energy through high-voltage undersea cables to Singapore, which is situated nearly 5000 kms away.[30]
Over the years, the Gulf Cooperation Council (GCC) has become one of the most economically influential organisations. All the six member-states – Bahrain, Kuwait, Oman, Qatar, Saudi Arabia, and the UAE, are oil-rentier economies and account for significantly high cleaner and greener energy potential. While the process for harnessing renewable energy is at an initial stage, developing regional electricity grids powered with greener energy, and supplying energy to other states in the region is an area of high potential for the West Asian states.
Through OSOWOG and GGI, and by leveraging the technology used by Australia, together the West Asian states could develop infrastructure to provide cleaner and greener energy to other states in the region and even beyond in the African and European continent. As they already have a collaborative arrangement through the GCC, leveraging it to become the pioneers of supplying renewable energy through regional electricity grids and undersea cables could elevate their regional geopolitical position.
Conclusion
No state is immune to the impacts of the climate crisis, which include rising sea levels, increasing temperatures, droughts, food insecurity, and forced displacement. The need to reduce fossil fuel consumption is paramount, making energy transition inevitable. With growing populations and increasing energy demands, a gradual energy transition is essential. However, its impact on global power distribution and the geopolitical status quo cannot be overlooked.
For oil producing West Asian states, energy transition from oil to cleaner and greener energy sources has the potential to destabilise the regional balance of power. While it reduces the likelihood of physical conflicts over energy resources, it introduces political and economic complexities that could heighten regional tensions. China’s dominance in climate technology and critical mineral supply chains will undoubtedly influence these states’ relationships with China. Amidst the US-China rivalry, this dynamic could lead the US to reassess its approach to the region, contributing to increased tensions. Intra-regional factors, such as the rivalry between oil and gas producers, the use of nuclear energy, and the potential use of regional grids, will also impact regional stability.
The foremost strategy for the West Asian states to navigate this complexity is to develop a farsighted and comprehensive economic and political diversification strategy. While China’s monopoly over crucial factors is significant, initiatives like the India-Middle East-Europe Economic Corridor and I2U2 can help balance multiple powers’ interests and concerns, providing domestic benefits and opportunities for the oil rentiers of West Asia.
Author Bio: Soumya Chaturvedi is a Visiting Fellow at India Foundation. Previously, she has worked as a Consultant at the G20 Division, Indian Ministry of External Affairs and as Senior Research Fellow at India Foundation. A lawyer by education, she holds a Master’s degree in International Relations from India and a specialisation in Asia Pacific Security from the UK.
References:
[1] Calculated based on the petroleum and other liquids production information publicly made available by the US Energy Information Administration, as accessed on June 04, 2024, https://www.eia.gov/international/data/world.
[2] Ekrem Biceroglu, Muhammed Emin Canik, Ahmet Dursun, “Middle East plays vital role in global oil production,” Anadolu Agency, August 11, 2023, https://www.aa.com.tr/en/economy/middle-east-plays-vital-role-in-global-oil-production/2965593.
[3] “Net Zero Scorecard,” Energy &Climate Intelligence Unit, as accessed on June 04, 2024, https://eciu.net/netzerotracker.
[4] “UAE Energy Diversification,” Embassy of The United Arab Emirates Washington DC, as accessed on June 05, 2024, https://www.uae-embassy.org/discover-uae/climate-and-energy/uae-energy-diversification#:~:text=Renewable%20Energy,-The%20UAE%20has&text=per%20kilowatt%20hour.-,The%20UAE%20has%20three%20of%20the%20world’s%20largest%20solar%20plants,200%2C000%20cars%20off%20the%20road.
[5] Kate Dourian, “Kuwait’s New Energy Strategy Takes Off but Oil’s Still Dominant,” The Arab Gulf States Institute in Washington, May 14, 2024, https://agsiw.org/kuwaits-new-energy-strategy-takes-off-but-oils-still-dominant/.
[6] Hazem Beblawi, “The Rentier State in the Arab World,” Arab Studies Quarterly 9(4), (1987), pp. 383–98. http://www.jstor.org/stable/41857943.
[7] John V. Basarin, “Oil: The Underlying Reason for Gallipoli,” Australian Institute for International Affairs, April 24, 2015, https://www.internationalaffairs.org.au/australianoutlook/oil-the-underlying-reason-for-gallipoli/.
[8] Martin William Gibson. (2012). British Strategy and Oil, 1914–1923 (PhD). Glasgow Theses Service. https://theses.gla.ac.uk/3160/.
[9] Rasoul Sorkhabi, “Oil from Babylon to Iraq,” GEOExPro – The Global Energy Sector From A Subsurface Perspective, April 02, 2009, https://geoexpro.com/oil-from-babylon-to-iraq/.
[10] David Ottaway, “The U.S. Saudi Arabia Since the 1930s,” Foreign Policy Research Institute, August 28, 2009, https://www.fpri.org/article/2009/08/the-u-s-and-saudi-arabia-since-the-1930s/.
[11] “Suez Crisis, 1956,” US Department of State Archive, as accessed on May 25, 2024, https://2001-2009.state.gov/r/pa/ho/time/lw/97179.htm.
[12] Supra note 4.
[13] JR MacLeod, “Saudi Arabia’s Quandary: The End of the Petrodollar,” Mises Institute – Austrian Economics, Freedom, and Peace, March 02, 2023, https://mises.org/mises-wire/saudi-arabias-quandary-end-petrodollar.
[14] Derika Weddington, “Rivalry in the Middle East: The History of Saudi-Iranian Relations and its Implications on American Foreign Policy” (2017). MSU Graduate Theses, https://bearworks.missouristate.edu/theses/3129
[15] Steven A. Cook, “The US Needs a New Purpose in the Middle East,” Foreign Policy, June 03, 2024, https://foreignpolicy.com/2024/06/03/us-middle-east-policy-pivot-iraq-war-withdrawal-oil-israel-terrorism-climate/.
[16] Summer Said & Stephen Kalin, “Saudi Arabia Considers Accepting Yuan Instead of Dollars for Chinese Oil Sales,” The Wall Street Journal, March 15, 2022, https://www.wsj.com/articles/saudi-arabia-considers-accepting-yuan-instead-of-dollars-for-chinese-oil-sales-11647351541.
[17] Andre Mansson, “A resource curse for renewables? Conflict and cooperation in the renewable energy sector,” Energy Research & Social Science, Vol. 10, November 2015, pp. 1-9, https://www.sciencedirect.com/science/article/abs/pii/S2214629615000791
[18] Daniel Scholten & Rick Bosman, “The geopolitics of renewables; exploring the political implications of renewable energy systems,” Technological Forecasting and Social Change, Elsevier, Vol. 103(C), 2016, pp, 273-283, doi: 10.1016/j.techfore.2015.10.014.
[19] Meghan O’Sullivan, Indra Overland, David Sandalow, “The Geopolitics of Renewable Energy,” Harvard University, Columbia University, and the Norwegian Institute of International Affairs, https://www.researchgate.net/publication/317954274.
[20] “Patents and the energy transition Global trends in clean energy technology innovation April 2021”, a report by International Energy Agency and European Patent Office, as accessed on 30 May 2024, https://www.iea.org/reports/patents-and-the-energy-transition.
[21] “Elsevier report highlights exponential growth of Chinese patents in carbon-free energy technologies,” ScienceBusiness, November 02, 2021, https://sciencebusiness.net/news-byte/patents/elsevier-report-highlights-exponential-growth-chinese-patents-carbon-free-energy.
[22] “China extends green tech lead to carbon capture and sequestration,” Nikkei Asia, May 19, 2024, https://asia.nikkei.com/Spotlight/Environment/Climate-Change/China-extends-green-tech-lead-to-carbon-capture-and-sequestration.
[23] Jane Nakano, “US-China Relations and the Global Energy Transition,” in Forum: Taking Stock of China and the Geopolitics of Energy, The Oxford Institute for Energy Studies, August 2023, Issue 137, pp. 44.
[24] Dolf Gielen, “Critical Minerals for the Energy Transition,” International Renewable Energy Agency, Technical Paper 5/2021, https://www.irena.org/-/media/Irena/Files/Technical-papers/IRENA_Critical_Materials_2021.pdf.
[25] “The Role of Critical Minerals in Clean Energy Transitions,” World Energy Outlook Special Report, International Energy Agency, March 2022, https://www.iea.org/reports/the-role-of-critical-minerals-in-clean-energy-transitions/executive-summary.
[26] “Energy Transition and Geopolitics: Are Critical Minerals the New Oil?,” World Economic Forum, White Paper, April 2024, https://www.weforum.org/publications/energy-transition-and-geopolitics-are-critical-minerals-the-new-oil/.
[27] Amena H. Sayid, “Nickel illustrates China conundrum on critical minerals,” Cipher News, May 29, 2024, https://www.ciphernews.com/articles/nickel-illustrates-china-conundrum-on-critical-minerals/.
[28] “About,” International Solar Alliance, as accessed on June 07, 2024, https://isolaralliance.org/work/osowog/.
[29] “Why Grids?,” Green Grids Initiative, as accessed on June 07, 2024, https://www.greengridsinitiative.net/.
[30] Loz Blain, “World’s biggest clean energy project to power Singapore from Australia,” September 28, 2021, https://newatlas.com/energy/sun-cable-australia-singapore-solar-undersea-powerlink/.
The Sectarian Divide: A Complex Mosaic of Sects and Subsects
Introduction
The Gaza War (2023–2024) has renewed attention to the explosive nature of the West Asia and North Africa (WANA) region. As the War continues, failing all regional and international ceasefire efforts, the region is experiencing heightened tensions between Israel and Iran while keeping the Arab states jittery. The conflict notwithstanding, the region is critical to global politics due to its geo-strategic location, energy resources, and centrality to the three Abrahamic faiths—Judaism, Christianity, and Islam. A complex web of political, social, religious, cultural, economic, geopolitical, and external factors has kept WANA conflict-ridden for over a century. The inability of the post-colonial states to adapt to democratic norms has allowed the festering of internal divisions, contributing to civil strife, uprisings, revolutions, violence, terrorism, and intra- and inter-state wars. In the decade since the Arab Spring protests erupted in December 2010 in Tunisia, the region suffered a series of violent conflicts, geopolitical competitions, and the proliferation of armed non-state actors (ANSAs) and terrorist groups. These, in turn, resulted in the multiplication of weak or failed states, posing severe challenges to their cohesiveness and threatening peace and stability in WANA.
Sectarianism is one of the most common frameworks utilised in International Relations and Middle East studies literature to examine, analyse, and explain the widespread divisions, strife, conflicts, and rivalries in WANA.[1] While helpful in explaining the region’s complexities, the broad semantic implications of the term lead to confusion. Sectarianism is an overarching term used to denote the identitarian divisions among communities. It is often used to define inter- and intra-faith, and ethnonational divisions, or the use of such divisions by states and non-state actors to gain legitimacy and advance their interests.[2] Nonetheless, when one refers to sectarianism in WANA, essentially the allusion is to the historic Sunni-Shia division within Islam that permeates across the region.[3] In other words, the Sunni-Shia divide is often considered to be the root cause of the challenges facing WANA countries.
The 1979 revolution in Iran and the foundation of the Islamic Republic under the leadership of Ayatollah Khomeini is often considered the most consequential contemporary event that sowed the seeds of the sectarian-identitarian divisions in WANA. After 1979, with its reliance on Shia theology and the ideological discourse of justice and resistance against American-Western hegemony and imperialism, Iran emerged as the leader of the Shias. Alternatively, the Kingdom of Saudi Arabia projected itself as the leader of Sunnis due to its custodianship of the Two Holy Mosques. However, the issue of sectarianism is more complex than its narrow and popular understanding, as the Sunnis and Shias are not cohesive and homogenous communities, and more importantly, the divisions between Iran and Saudi Arabia go beyond the sectarian divide.[4] Hence, sectarianism in WANA should be understood as a complex mosaic of and interplay among many primordial and political identities.
Sectarianism and its manifestations
Within the broad classification of Sunni and Shia sects, several political, jurisprudential, ethnonational, linguistic, ideological, and historical divides contribute to the complexity of sectarianism in WANA. Further, Iran’s and Saudi Arabia’s claims to be the leaders of the Islamic world go beyond their essentialist sectarian identities. For example, Iran’s relationships with its regional allies, namely Syria, Hezbollah, Hamas, and Houthis, transcend the narrow definition of sectarianism.[5] Similarly, the Saudi claim to leadership of the Islamic world surpasses its control over the Kaaba in Makkah and the Prophet’s Mosque in Madinah to include oil wealth, its relationship with the US, and its support for a future Palestinian state.[6] Besides, geopolitical factors are often more important in setting the direction of the foreign policy of the regional powers than sectarian considerations. Additionally, the internal dynamics of each state and the extent of sectarianism in them depend on the nature of the ruling regime and are not the same. Hence, a majority Shia country like Bahrain, ruled by a Sunni dynasty, is an ally of Saudi Arabia. In contrast, a majority Sunni country like Syria, ruled by a socialist, republican dynastic regime, is part of the Iranian camp.
Besides the historical, theological, and geopolitical Sunni-Shia division, sectarianism in WANA is reflected through religious and ethnonational divides. The prime example of a religious divide intermixed with ethnonational movements and combined with regional and international geopolitics producing a conflict is the Israeli-Palestinian issue. The Israeli and Palestinian claims over the land constituting Israel and the Occupied Palestinian Territories (West Bank, Gaza Strip, and East Jerusalem) are rooted in the historic Jewish and Islamic control over it and its religious significance for both communities. For Jews, Jerusalem is central to the faith as it is the location of the destroyed Second Temple. At the same time, for Muslims, Jerusalem is the first Qibla and the site from which Prophet Muhammad ascended to heaven during Miraj.[7] Hence, for both sides, while the nationalist claims of Israelis and Palestinians remain important, the religious component is a prime motivator for taking an uncompromising position on the matter, thus contributing to the continuation of the long and deadly conflict.[8]
Another major ethnonational issue that has produced conflicts, divisions, and an unsuccessful quest for a state is the Kurdish issue. The Kurds are a majority Sunni community living in a territorially contiguous area encompassing four states: Iran, Iraq, Syria, and Türkiye. With an estimated global population between 30 and 45 million,[9] the Kurds are often referred to as one of the largest stateless communities in the world. The Kurdish quest for autonomy and state goes back to the fall of the Ottoman Empire and the end of the First World War but has remained elusive.[10] In Iraq, the formation of the Kurdish autonomous region as per the 2005 constitution was a landmark event, but it did not lead to any progress towards an independent Kurdish state. Similarly, after the Arab Spring in Syria, the Kurdish-dominated northern areas were declared an autonomous region under the US-supported Syrian Democratic Force (SDF) control, but without much progress towards formal autonomy or a future Kurdish state. In Türkiye, the Kurds are the largest ethnic minority that has suffered due to the Turkish counter-insurgency campaign against the armed struggle waged by the Kurdistan Workers’ Party (PKK). In Iran, too, Kurds are a significant ethnic minority that fear losing their identity to the assimilating tendencies of the Islamic Republic.
Many other religious and ethnonational minorities in the region have suffered due to increased sectarianism. Christian minorities such as Copts in Egypt and Maronites in Lebanon, other religious minorities such as Zoroastrians and Baha’is in Iran, and Yazidis in Iraq, ethnic and tribal groups such as Berbers, Tuaregs and Blacks in North Africa, Armenians, Assyrians, Turkmen and Druze in Fertile Crescent region, Arabs, Baloch and other minorities in Iran and Bidoons and poor expatriates from Asia in the Gulf are groups that have suffered due to the sectarian, essentialist and narrow identitarian tendencies that prevail in the region. There are, moreover, divisions based on the secular-religious divide, which is felt strongly in countries such as Türkiye, Egypt, and Tunisia and often plays out in the form of popular support for Islamists. At the same time, the state remains rooted in secularist ideals. The most recent example of such divisions is the military coup in Egypt in 2013, whereby the Islamist-inclined government of Mohammed Morsi was overthrown by the deep state led by the then Defense Minister Abdel Fattah El-Sisi. In the Tunisian case, the secular-religious divide played out in 2021 after an elected populist President, Kais Saied, suspended the parliament and dismissed the judiciary to take complete control over the state.
The most widespread and popular Islamist group is the Muslim Brotherhood, with an ideology rooted in Islamic republicanism that aims for a socio-political reorganisation of Muslim states and calls for resistance against the imposition of Western values and norms.[11] The Brotherhood has roots in Egypt but is present in some form in almost all regional countries today. The groups and their affiliates gained strong public support in the wake of the Arab Spring protests despite the initial hesitation of the Brotherhood leadership. However, the fear of the Brotherhood gaining ground across the region and calls for political change alarmed the Sunni monarchies. This led to the Brotherhood being banned by most regional states, including the UAE and Saudi Arabia.[12] Despite that, the movement and its ideology remain alive, and the silence, whether perceived or actual, of the Arab states and their leadership against Israeli actions in Gaza since October 2023 might help the movement regain populist appeal.
The ideological component of Islamism and how it has contributed to the rise of sectarianism in WANA cannot be wholly dissociated from the issue of terrorism, manifested most starkly in the form of al-Qaeda and Islamic State. Both these groups have their roots in the puritanical and militant Islamism of the twentieth century, with a hybrid ideology fused by selective readings of Islamic texts through interpretations of scholars such as Ibn Taymiyya, Muhammad bin Abdul Wahhab, Syed Qutb, Abul Ala Maududi, Abd as-Salam Faraj, and Abdullah Azzam.[13] Osama bin Laden and Abu Musab al-Zarqawi, the men behind the formation of al-Qaeda and Islamic State, respectively, were inspired by such interpretations and used the wider socio-political dissatisfaction in Arab-Muslim societies to spread their ideology and gain support. Hence, al-Qaeda and Islamic State represent the wider sectarianism that spread through the rise of militant Islamisation and eventually forged into globalised jihadi terrorism. The same was visible in Iraq in the aftermath of the US invasion in 2003, leading to a sectarian civil war and eventually catalysing the rise of the Islamic State after the Arab Spring.
Sectarianism and states in WANA
Most WANA states have faced the challenge of sectarianism. As noted in the preceding section, the core of the sectarian divide is the socio-political fissures based on primordial identities rooted in religious, political, ethnonational, or ideological convictions. These narrow sectarian divisions have created a situation wherein most WANA countries have experienced sectarian divisions, causing political tensions and security concerns. For example, Sunni-Shia sectarian division in Saudi Arabia is often viewed as the reason for the alienation among a section of Saudi citizens belonging to the Shia community concentrated in the Eastern Province.[14] Although the socio-cultural opening under King Salman and Crown Prince Mohammed bin Salman has allowed greater space for the Saudi Shia community, the issue of division persists. Iran, too, has faced the challenge of managing its internal socio-political divisions based on identitarian politics, wherein a series of ethnic and religious minorities, including Baha’is, Zoroastrians, Sunnis, Arabs, Kurds, Baloch, and other smaller groups, have been alienated due to the assimilating tendencies of the majoritarian Persian-Islamic identity.[15] Similarly, minority groups such as Kurds and Alawis in Türkiye, Copts in Egypt, Palestinian-Arabs in Israel, Yazidis and Sunni Arabs in Iraq, Shias in Bahrain, Berbers, Tuaregs, and Blacks in North African states, and other groups have faced greater challenges due to the respective state’s behaviour towards them.
Notably, some of the regional states have faced more significant challenges due to sectarianism, and three countries, namely, Iraq, Lebanon, and Yemen, stand out. Three major groups, Shias, Sunnis, and Maronites, hold sway in Lebanon because of their dominant demography, which has been instrumental in determining the country’s consociational political system.[16] The political power is divided among these three groups, and although the idea was based on proportional representation, the situation has created severe problems for the country. First, the situation has evolved because of demographic changes, and the fixed system is no longer adequately representative. Second, the youth, smaller minorities, and women have faced exclusion because of the appropriation of power by corrupt political groups, leaving the ordinary people suffering. The creation of Hezbollah and its emergence as a state within the state have further contributed to the rise of political and sectarian divisions in Lebanon, pushing the country to the verge of collapse.[17]
Iraq, too, has suffered historically due to its political system and the identity politics that have prevailed since its foundation under the British Mandate. The three major sectarian-ethnic groups in Iraq are Shias, Sunnis and Kurds, but smaller sections of Christian denominations, Yazidis, Assyrians, and Turkmen, have lived in Iraq for centuries. Iraq was at the forefront of Arab nationalism in the 1950s and 1960s, but this led to suffering among the non-Arab minorities.[18] The situation for Kurds, Shias and Christians became highly challenging under the Sunni-socialist dictatorship of Saddam Hussain, with the state taking punitive actions against each of these groups on suspicion of secession. The hopes for political change in post-Saddam Iraq could not be realised as the US invasion led to increased sectarian strife, leading to a violent civil war, and this manifested in the rise of the Islamic State in the post-Arab Spring era. Despite a political system based on a carefully crafted constitution to bring a representative government and political system, Iraq has suffered due to intra-community divisions and infighting, causing widespread discontent among the people who consider the political system externally induced and corrupt.[19]
The situation in Yemen has historically been complicated because of the widespread tribal, sectarian, and ideological divisions that have reverberated since parts of Yemen came under British colonial control, and the situation worsened in the post-colonial phase. The division of Yemen into North and South and the continued sectarian divisions after the 1990 unification under Ali Abdullah Saleh raised widespread strife, alienating many groups such as the Zaidis in northern areas, Sunni tribes in the sparsely inhabited central areas and leftist-secular groups in the south.[20] Discontent among tribes meant that Al-Qaeda in the Arabian Peninsula (AQAP) gained ground, and post-Arab Spring, Yemen descended into a civil war, causing one of the worst humanitarian crises in contemporary history. Today, Yemen is a divided house wherein the majority of northern Yemen is under the control of the Houthi movement, that denied the Saudi-led GCC military intervention to overthrow it from Sana’a and other major cities and ports. On the other hand, southern parts of the country are controlled jointly by the internationally recognised government and the Southern Transition Council (STC).[21]
Sectarianism and regional order in WANA
It is not only the regional states that have been affected by sectarianism but the regional order is seriously affected by the rise of sectarianism and identity politics.[22] Intermixed with geopolitical ambitions, sectarianism has created an explosive situation in WANA, threatening regional security and stability. Competition, rivalry and tension among the regional states define today’s regional order. Based on narrow interests, these states act alone or in tandem with like-minded countries within or outside the region. One of the significant reasons for the states to act on narrow interests is their quest for survival. For all regional states, the question of the state’s and regime’s survival remains at the top of the agenda. Moreover, the competition for resources, influence, and power makes the regional states suspect each other, keeping the regional order dependent on external military and political involvement.[23]
Sectarianism is widespread due to regional politics’ organisation, as the majority of regional states were founded based on narrow religious, sectarian, tribal, or ethnonational identities.[24] Hence, narrow interests often trump the pursuit of a broader collective good. For example, the two major regional powers, Iran and Saudi Arabia, have since 1979 remained major rivals because of their inability to reconcile their differences, despite a series of rapprochements since the 1990s.[25] Türkiye and Egypt have continued to define their interests based on narrow identity politics. The same is true for Israel, UAE, Qatar, Iraq, Syria, Jordan, Algeria, Morocco etc. When it comes to regional politics and order, the Arab, Persian, Turkish, Kurdish, Jewish, Islamic, Shia, Sunni, secular, religious, and other essentialist notions come to the fore instead of the need for creating broad economic and political consensus and interdependence.
Regarding the regional politics in WANA, three competing orders vie for dominance. The first is led by oil-rich Arab Gulf monarchies, namely Saudi Arabia and the UAE, and their regional allies and partners, including Egypt, Jordan, Bahrain, and Morocco. It is based on the quest for domination for an Arab-Islamic-Sunni order that works on the strength of oil wealth in conjunction with US security cover and acceptance of Israel’s right to exist as a Jewish state. Based on this vision of the regional order, the Abrahamic Accords were signed, and a discussion on extending it to Saudi Arabia is ongoing. The problem with such an order is that the regional allies and partners are not always in sync and often diverge on crucial matters, including the continued non-resolution of the Palestinian issue. Predominantly, this order is ensured by the strength of the US military presence; nonetheless, the entry of China and Russia and the strategic hedging by dominant Sunni-Arab states have further complicated it.[26]
The second vision is led by Iran, which is based on the narrow Persian-Shia identity with a clarion call for resistance against American-Western domination and extermination of Israel. Led by Iran, this vision of the regional order has gained ground due to a series of Iranian strategic moves and events that Iran could exploit to gain influence. This has been defined as the rise of the Shia Crescent[27] wherein Iran has gained significant influence in Iraq, Syria, Lebanon, Yemen, and Palestine through its alliances with state and non-state actors.[28] While essentially calling for a regional order free from American-Western domination, both in political and cultural domains, it also denies the Israeli right to existence because of ideological and religious convictions. Thus, the narrow Persian, Shia, and Islamic basis of such a regional order runs in contradiction to the claims towards justice and self-determination given its denial of expression of non-Islamic identities.
Finally, both these visions of the regional order are challenged by a political Islam or Islamist-inspired regional order that has both moderate and extremist versions.[29] The moderates essentially have shunned any form of violence and receive support from Türkiye and Qatar to create a Sunni-Islamic-republican regional order that is free from external domination and ethnonational and sectarian divisions. Such an order, however, remains non-committed to the Israeli right to existence and has often found itself in an internal quagmire due to ideological and religious divergence. Besides, Islamism has its violent, extremist manifestations, including terrorist groups that call for a complete reorganisation of regional order by overthrowing regional states, as is the case with al-Qaeda and Islamic State. This has led to a situation wherein increasingly both Saudis and Iranians have grown more suspicious of Islamist groups, including the Muslim Brotherhood.
Notably, narrow sectarian and identitarian convictions are present in all three visions of the regional order. While the US-induced regional order led by Sunni-Arab Gulf monarchies and Israeli support remains dominant, the Iran-led regional order, with the support of its allies and proxies and by developing strategic partnerships with China and Russia has become a stark reality. The third, supported partially by Türkiye and Qatar, inspired by various ideological offshoots of Islamism, gained some ground in the post-Arab Spring regional politics, but today largely remains a vision without much national, regional or international support.
Conclusion
The WANA region has suffered severe challenges to peace, stability, and security due to the pervasive nature of sectarianism in national and regional politics. Sectarianism, defined as narrow and exclusive identitarian politics, permeates through the states and societal boundaries. Various historical, political, social, religious, ideological, and external factors have contributed to the creation and expansion of sectarian politics. Consequently, the region has suffered from divisions, conflicts, infightings, uprisings, and revolutions, further sharpening the sectarian political divide. This has harmed the regional states, contributing to their instability and insecurity; has devastated many communities, especially different minorities, threatening their existence; and has seriously affected regional politics and order, caused tensions and rivalries, and often led to threats of a regional war. The complex interplay of sects and subsects as a determining factor in politics in and among WANA states has created a complex problem that cannot be resolved without changing the basis of politics while accepting the reality and plurality of the people and their identities.
Author Bio: Md. Muddassir Quamaris Associate Professor, Centre for West Asian Studies, School of International Studies, Jawaharlal Nehru University, New Delhi.
References
[1] Nader Hashemi and Danny Postel, “Introduction: The Sectarianization Thesis,” in Nader Hashemi and Danny Postel (eds.), Sectarianization: Mapping the New Politics of the Middle East, New York: Oxford University Press, 2017, pp. 1–22.
[2] Fanar Haddad, Understanding ‘Sectarianism’: Sunni-Shia Relations in the Modern Arab World, London: C. Hurst & Co., 2020.
[3] Laurence Louër, Sunnis and Shi‘a: A Political History of Discord, translated from French by Ethan Rundell Princeton, NJ: Princeton University Press.
[4] Paul Dixon, “Beyond Sectarianism in the Middle East? Comparative Perspective on Group Conflict,” in Fredric Wehrey (ed.), Beyond Sunni and Shia: The Roots of Sectarianism in a Changing Middle East, New York: Oxford University Press, 2016, pp. 11–36.
[5] Afshon Ostovar, “Sectarianism and Iranian Foreign Policy,” in Fredric Wehrey (ed.), Beyond Sunni and Shia: The Roots of Sectarianism in a Changing Middle East, New York: Oxford University Press, 2016, pp. 87–112.
[6] Menno Preuschaft, “Islam and Identity in Foreign Policy,” in Neil Patrick (ed.), Saudi Arabian Foreign Policy: Conflict and Cooperation, London: I. B. Tauris, 2016, pp. 16–29.
[7] Miraj refers to the Islamic belief that Prophet Muhammad undertook a miraculous night journey from Masjid al-Haram in Makkah to Masjid al-Aqsa in Jerusalem, and from there, he ascended to Heaven (in the presence of Allah) on 26 Rajab 621 AD. See Ali Kose, “Miraj” in David A. Leeming, Kathryn Madden and Stanton Marlan (eds.), Encyclopedia of Psychology and Religion, Boston, MA: Springer, 2010, p. 573.
[8] Marshall J. Breger, Yitzhak Reiter and Leonard Hammer (eds.), Sacred Space in Israel and Palestine: Religion and Politics, Abingdon, UK: Routledge, 2012.
[9] Nearly 70 per cent of the Kurdish population is concentrated in the four WANA countries, while the rest lives in the diaspora, mainly in Europe.
[10] Michael M. Guntur, The Kurds: A Divided Nation in Search of a State, Princeton, NJ: Markus Wiener Publishers, 2019.
[11] Joas Wagemakers, The Muslim Brotherhood: Ideology, History, Descendants, Amsterdam: Amsterdam University Press, 2022.
[12] Cinzia Bianco, The Gulf Monarchies after the Arab Spring: Threats and Security, Manchester, UK: Manchester University Press.
[13] Shiraz Maher, Salafi-Jihadism: The History of an Idea, London: C. Hurst & Co., 2016.
[14] Fouad N. Ibrahim, The Shiʻis of Saudi Arabia, London: Saqi Books, 2006; Toby Matthiesen, The Other Saudis: Shiism, Dissent and Sectarianism, New York: Cambridge University Press, 2015.
[15] S. Behnaz Hosseini (ed.), Ethnic Religious Minorities in Iran, Singapore: Springer, 2023.
[16] Imad Salamay, The Government and Politics of Lebanon, Abingdon, UK: Routledge, 2014.
[17] Mordechai Nisan, Politics and War in Lebanon: Unraveling the Enigma, New Brunswick, NJ: Transaction Publishers, 2015.
[18] Adeed Dawisha, Iraq: A Political History, Princeton, NJ: Princeton University Press, 2009.
[19] Jacob Eriksson and Isaac Grief, “The Iraqi State’s Legitimacy Deficit: Input, Output and Identity-based Legitimacy Challenges,” Global Policy, 2023, 14 (2): 363–72.
[20] Paul Dresch, A History of Modern Yemen, Cambridge, UK: Cambridge University Press, 2000.
[21] Marieke Brandt, Tribes and Politics in Yemen: A History of the Houthi Conflict, New York: Oxford University Press, 2017.
[22] Bassel F. Salloukh, “The Sectarianization of Geopolitics in the Middle East,” in Nader Hashemi and Danny Postel (eds.), Sectarianization: Mapping the New Politics of the Middle East, New York: Oxford University Press, 2017, pp. 35–52.
[23] Raymond Hinnebusch, The International Politics of the Middle East, Manchester, UK: Manchester University Press, 2003.
[24] Uzi Rabi, The Return of the Past: State, Identity, and Society in the Post-Arab Spring Middle East, Lanham: Lexington Books, 2020.
[25] Anoushiravan Ehteshami, Competing Powerbrokers of the Middle East: Iran and Saudi Arabia, Abu Dhabi: The Emirates Centre for Strategic Studies and Research, 2008.
[26] Jean-Loup Samaan, Strategic Hedging in the Arabian Peninsula: The Politics of the Gulf-Asian Rapprochement, London: Routledge, 2019.
[27] During a television interview with NBC’s Chris Mathews, King Abdullah of Jordan used the term Shia Cresent for the first time in 2004. See: https://www.nbcnews.com/id/wbna6679774#.UcV3GZymV9s
[28] Vali Nasr, The Shia Revival: How Conflict within Islam will Shape the Future, New York: W. W. Norton & Co.
[29] Tarek Osman, Islamism: What it Means for the Middle East and the World, New Haven: Yale University Press, 2016.
West Asia & North Africa: A Region in Churn
There is a famous quote among Arab scholars. It is said that when the Umayyad Dynasty fell, they asked Abbasid Caliphate Abu Ja’far Al Mansur about the reasons for its demise, and this wise man cried out, “We handed over the small matters to adults and the big matters to the children, so we divided them between excess and negligence. Rather, he added with regret: We brought the enemy closer, hoping to gain his affection, and pushed the friend away, guaranteeing his loyalty. So, we suffered the treachery of the first and lost the loyalty of the second.”
However, many factors contributed to the fall of the Umayyad Dynasty. Its weakening started with the defeat of the Syrian army by the Byzantine emperor Leo III in 717 CE. Many other contributory factors, like the division among the rulers, intertribal feuds, economic factors, and the high rise of prices, besides the plague inflicted on the state, led to migration and the disintegration of the dynasty. The Abbasid dynasty defeated the Umayyad dynasty with the help of non-Arab Muslims and lasted from 750–1217 until the Ottomans took over.[1]
Nothing has changed from then to date, and the saga of Arab suffering continues. What is it like today compared to yesterday?
The transformation of the Arab nation from a sense of unity and solidarity to a fragmented collection of states is a significant aspect of modern Middle Eastern history. The concept of an “Arab nation” historically evoked a sense of shared identity, culture, and heritage among the region’s peoples. The centuries-long Ottoman rule over the Arab world is depicted as a period of stagnation and suppression of intellectual and scientific progress. The Ottoman Empire’s policies restricted the role of intellectuals, scientists, and progressive leaders, denying them opportunities for advancement and contribution to society.
The colonial legacy and the Sykes-Picot Agreement of 1916, named after the British and French diplomats who negotiated it, divided the Middle East and North Africa (MENA) into spheres of influence between the two colonial powers, disregarding local aspirations and identities. The content of the declaration seems no less distant or downright baffling. The prominent Jewish intellectual Arthur Koestler, repeating a frequent mantra, would call it “one of the most improbable political documents of all time,” in which “one nation solemnly promised to a second nation the country of a third.[2]
This betrayal of Arab leaders, who were promised independence in exchange for their support against the Ottomans, underscores the manipulative tactics of colonial powers in the region. This agreement, along with other colonial interventions in the region, laid the foundation for the modern nation-states in the Middle East, often drawing arbitrary borders that did not correspond to the ethnic or religious demographics of the region.[3]
The role of external powers, such as Britain, France, and later the United States, in shaping the political and economic landscape of the Middle East cannot be overstated. From colonial rule to interventionist policies, these powers have exerted significant influence over the region, often to further their strategic interests, leading to instability, conflict, and the suppression of indigenous movements for self-determination. The “birth of a ‘Jewish State’ in the heart of Palestine by Britain” alludes to the Balfour Declaration of 1917 in which the British government expressed support for the establishment of a national home for the Jewish people in Palestine. This declaration, coupled with subsequent British policies and the United Nations partition plan in 1947, led to the creation of the state of Israel in 1948, a development that has had profound consequences for the region, including ongoing conflict and displacement of Palestinian populations. The ongoing Israel war on Palestine is but a manifestation of the old policy, which will impact US and European Union influence in the region.
The transition from a unified Arab nation to a fragmented collection of states, shaped by colonial legacies and external interventions, remains a defining feature of modern Middle Eastern history, influencing regional dynamics and conflicts today. The struggle for control over the Arab world has been influenced by its rich natural resources, strategic geographical location, and historical significance as a crossroads between East and West. The Arab world is endowed with vast reserves of oil, natural gas, and other valuable resources. These resources have made the region a focal point for international competition and have attracted the interest of colonial powers seeking to exploit them for economic gain. Control over these resources has been critical to shaping the region’s geopolitical dynamics. The Arab world’s geographical location between Europe, Africa, and Asia has endowed it with strategic importance throughout history. Its position as a natural corridor between three continents has made it a crucial hub for trade, transportation, and military access. This has made the region a target for colonial powers seeking to control key trade routes and military chokepoints.
Colonial European powers, driven by economic interests and geopolitical ambitions, sought to maintain control over the Arab world by ensuring its fragmentation and division. By fostering internal divisions, supporting authoritarian regimes, and drawing arbitrary borders, colonial powers sought to keep the region weak and easily exploitable for their benefit. The United States, inheriting the legacy of colonial powers in the region, became a dominant player in the Arab world following World War II. With the collapse of the Soviet Union, the US emerged as the world’s sole superpower, further consolidating its influence over global affairs, including in the Middle East. American foreign policy in the region has often been driven by strategic and economic interests, mainly energy and Israel-centric, leading to interventions, support for friendly regimes, and efforts to maintain stability to ensure access to vital resources and ensure Israel’s dominance in the fragmented region. Israel’s expansionist policies, particularly regarding its treatment of the Palestinian-occupied territories, have long been a source of contention in the region. The Israeli government’s determination to achieve its objectives and its ongoing conflict with Palestinian groups exacerbate tensions and fuel instability, with potential repercussions for regional security and stability for years to come.
The future world order will likely be influenced by a combination of ongoing geopolitical trends and emerging challenges, particularly in West Asia.
The invasion of Iraq and subsequent events, such as the Arab Spring, have contributed to the destabilisation and fragmentation of modern Arab states. These events have led to internal conflicts, power struggles, and the breakdown of governance structures, creating fertile ground for extremist groups and regional tensions. The COVID-19 pandemic has further exacerbated existing crises in the Middle East, including economic stagnation, unemployment, and governance challenges. The pandemic has strained healthcare systems, disrupted supply chains, and exacerbated socio-economic inequalities, leading to social unrest and political instability in some countries. External regional players, including regional powers and global actors, have often intervened in the internal affairs of Middle Eastern countries to further their interests. This interference has fuelled internal conflicts, exacerbated divisions, and hindered regional stability and cooperation efforts. Additionally, competition for control over strategic resources, such as oil and gas reserves in the Mediterranean Sea, has intensified regional rivalries and conflicts.
Overall, the Middle East faces significant challenges and uncertainties in the years ahead, but opportunities also exist for positive change through dialogue, cooperation, and inclusive governance. The future world order will likely be shaped by how these challenges are addressed and how regional and global actors navigate the complex dynamics of the Middle East.
Regional Powers Influence
The West Asia and North Africa (WANA) region is characterised by the competing interests and ambitions of regional and global powers. The rise of Islamic parties in countries like Morocco, Tunisia, Libya, and Egypt, often backed by Turkey and financial support from countries like Qatar and Saudi Arabia, reflects a broader trend of political Islam gaining ground in the region. The extent of external influence in shaping political outcomes in these countries is a subject of debate and concern, particularly regarding their potential destabilising effects.
Turkey’s pursuit of a Neo-Ottoman policy, coupled with its support for the Muslim Brotherhood, reflects Ankara’s aspirations to assert itself as a regional power and influence events in the wider Muslim world. This has led to tensions with other regional players and raised concerns about Turkey’s intentions and actions among Western allies. It was Turkey, the Pakistan of West Asia, that allowed its territories to be used by mercenaries from all over the world. It trained and armed them fully and sent them across Syria and Iraq. More than 1,37,000 mercenaries from more than 83 nationalities entered Syria and fought alongside ISIS and al Qaeda terrorist organisations. More than 6 million Syrians were forced to migrate outside Syria.
There are more than two million kids in refugee camps in neighbouring countries who never went to school and are subjected to exploitation. The Syrian refugees live in pathetic conditions and are denied basic needs to survive. While Syria is trying to liberate its territories from the USA-Turkey occupation and rebuild Syria to encourage refugees to return, the USA continues to impose harsh economic sanctions, making life hood more difficult for citizens.
Israel, on its part, continues its policy of weakening Syria, supporting the jihadists, and opening makeshift hospitals on the occupied Syrian Golan. At the same time, it pursued a policy of attacking Syria military installations, killing Syrian civilians, Lebanese fighters, and Iranian advisors till the last attack on the Iranian consulate in Damascus that killed a prominent Iranian official in violation of the Geneva Convention.
Ever since the Iranian revolution in 1979, removing CIA agents, closing the Israel embassy in Tehran and opening a Palestinian embassy instead, Iran has been subjected to harsh economic and military sanctions by the US, and carrying out, along with Mossad Israel intelligence, covert operations targeting scientists and prominent figures.
Iran’s efforts to expand its sphere of influence in the region, particularly through its support for groups like Hamas in Palestine-occupied territories, Hezbollah in Lebanon, and various factions in Iraq and Syria, have contributed to the formation of what is often referred to as the Axis of Resistance. This axis represents a challenge to Western interests and alliances in the region and has prompted reactions from other regional and global powers.
The mysterious demise of the Iranian president and foreign minister in an American-made B212 chopper crash, along with senior officials, added more challenges to the already volatile situation in the region. The investigation team will find out whether the death was due to a technical fault in the chopper that carried the president and his team or whether it was an act of terror carried out by an adverse state that caused the tragic incident. The outcome of the investigation will determine the course of events in West Asia.
Global Power Competition
The evolving dynamics in the WANA region, including the growing influence of regional players and the involvement of external powers such as Russia and China, have implications for global power dynamics. The United States, in response to perceived challenges from Russia and China, may seek to rally its allies, including through NATO, to counterbalance these forces and maintain its influence in the region. The Russian influence in the region increased significantly in spite of the West pressure
The NATO countries made a new International Security Arrangement in June 2022. The new Strategic Concept describes the new security reality facing the Alliance, reaffirms NATO’s values, and spells out NATO’s key purpose of ensuring the Allies’ collective defense. Russia remains a threat to NATO members, and China’s growing influence politically, economically, and militarily is a matter of concern for future systemic challenges.[4]
China, seeking a wider role, succeeded where the US failed in the rapprochement between Saudi Arabia and Iran and was able to strike a deal that eased the tension between the two leading Islamic states. Beijing kept a good relationship with the region’s stakeholders and avoided political intervention in any country’s internal affairs. The Belt Road Initiative (BRI) changed China’s doctrine. It started searching for a foot on the ground in countries that fell in the line of the route and trying to find fault lines of the West’s mischievous in the region without crossing the redlines set by the US, which considered itself the custodian of the gulf region. The recent China-Arab States Cooperation Forum held in Beijing on May 30, 2024, highlighted the importance of achieving security and stability, ending internal interference in the affairs of each nation, respecting the sovereignty of the state, stopping the Israel war on Gaza, and calling for a peaceful solution and a two-state solution to the conflict. All these political issues of mutual concern should cement the economic and trade bonds between the two nations.[5]
The tension between China and the US/Western world has reached a peak, fuelled by China’s growing competition, particularly in technology (5G), the arms market, infrastructure, and strategic connectivity projects.[6] The partial withdrawal of US forces from Iraq has implications for regional power dynamics and the balance of power vis-à-vis Israel and other actors in the Middle East. The potential strengthening of resistance forces against Israeli occupation is viewed as a threat to the strategic partnership between the US and Israel. In US perception, the threat of terrorism still looms large in Iraq as ISIS is still active and any US troops’ withdrawal will leave a vacuum that Iran could exploit. The US inflamed tensions after the killing of Qasem Soleimani and Muhandis Abbas, leader of the Popular Mobilization Forces, on January 3, 2020. The Iraqi government demanded the US remove its troops and refused to allow its territory to become a battleground between the US and Iran.
Syria: A Forgotten War
Syria holds a pivotal position in the Middle East due to its geographical location, history, and cultural diversity. Situated at the crossroads of Asia, Africa, and Europe, Syria serves as a bridge between the continents. Its location has made it a crucial centre for trade and cultural exchange throughout history. The country’s geography includes fertile plains, mountains, and access to important waterways like the Euphrates River, which have sustained civilisations for millennia.
Syria boasts a rich historical heritage dating back to ancient times. It is often referred to as the “cradle of civilisation” due to the numerous ancient cultures that flourished within its borders, including the Mesopotamians, Egyptians, Phoenicians, Assyrians, Greeks, and Romans. These civilisations have left behind a wealth of archaeological treasures, including the ruins of Palmyra, the ancient city of Aleppo, and the Umayyad Mosque in Damascus. Syria is home to a diverse array of ethnicities, religions, and languages. The majority of the population is Arab, but there are also significant Kurdish, Armenian, Assyrian, and Turkmen communities, among others. This diversity is reflected in Syria’s linguistic landscape, with Arabic being the official language and other languages like Kurdish, Armenian, and Aramaic also spoken by various communities. Syria is one of the few places where ancient languages like Aramaic are still spoken. Aramaic, the language spoken by Jesus Christ, continues to be used in small villages such as Maaloula, Jabaadin, and Bakhaa, primarily by Christian communities. This linguistic heritage is a testament to Syria’s long and complex history. Syria was safe and peaceful by all means till US foreign intervention and policy of clean breaks implemented and started supporting and funding banned Muslim Brotherhood organisation secretly, and turning Syria into Afghanistan in the making.
The brutal war in Syria began in 2011. Syrians, inspired by the Arab Spring uprisings in other Arab countries, began peaceful demonstrations demanding a better life and greater political freedoms. They hoped this would lead to government reforms. However, the situation escalated when the West, along with regional allies like Turkey and some Arab states, intervened. They provided billions of dollars in support, training and arming various rebel groups, including some extremists. This intervention, intended to topple the Syrian government, contributed significantly to the violence.
The war has caused immense suffering for civilians. All sides have been responsible for atrocities, including the bombing of civilian targets, use of child soldiers, and destruction of public infrastructure. The UN has confirmed the use of chemical weapons by extremist groups like ISIS and al-Qaeda. However, the West has falsely accused the Syrian government of the same, aiming to demonise the government and topple the President. This complex situation has fuelled a humanitarian crisis, forcing millions of Syrians to flee the country and has raised fears of Syria’s fragmentation.[7]
The conflict in Syria has now become a focal point for various regional and international actors due to its strategic significance and complex web of alliances. The West and the US see the Syrian government led by President Bashar Al-Assad, as a key ally of Iran and Hezbollah, and therefore, they aim to weaken Iran’s influence by supporting opposition forces in Syria. Conversely, Russia perceives the fall of Syria as potentially empowering Turkey and increasing Islamic influence in the region, which could align with US and Western interests in containing Iran. As a result, both Russia and Iran came to support. Along with the Syrian army, the Lebanese Resistance Forces and the Iraqi popular fronts, have succeeded in neutralising ISIS and al Qaeda. However, the US occupied Northern Eastern part of Syria and created a separate enclave to create an autonomous Kurdish region led by separatist faction PKK which is designated by US itself as a terrorist outfit. The PKK shelters more than 55,000 ISIS cadets while looting Syrian oil and natural resources.
The concept of redrawing the map of the Middle East, as proposed by some US scholars and military experts, reflects efforts to reimagine regional boundaries and configurations in alignment with perceived strategic interests. This includes considerations such as ethnic and religious demographics, as well as geopolitical objectives. However, such proposals are highly contentious and raise significant ethical, political, and practical challenges.
India‘s Strategic Considerations
The spillover of Israel’s war on Gaza was felt at the Red Sea with regular attacks by Ansar Allah (Houthi) of Yemen, who threaten all ships to Israel till it stops its war on Palestinians. They started attacking by drones and missiles on military and commercial vessels, which led to the militarisation by the West of the Red Sea and to the launch of military operations by Western navies in a bid to protect the mercantile shipping transversing in the area. The US Navy deployed two aircraft-carrier task groups to the region. The US, along with the United Kingdom, Bahrain, Canada, France, Italy, Netherlands, Norway, Seychelles, and Spain, launched Operation Prosperity Guardian (OPG) in response to the Houthi-led attacks on shipping in the Red Sea.[8]
With the geopolitical situation becoming increasingly complex and uncertain, India, driven by oil and food security and as a trusted ally in the gulf region, has been quick to grab the opportunity and secure its presence in the Gulf states by signing bilateral agreements with each one to protect its national interests. Moreover, India has strengthened its ties with the US and has become actively involved in Gulf security by signing several security deals, conducting joint military exercises, and free trade agreements. With the US becoming more focused on the Indo-Pacific Oceans, Asia could offer a solution. Under the leadership of Prime Minister Narendra Modi, New Delhi has become more concerned about asserting its strategic supremacy in the region, competing with Beijing, and positioning itself as the natural power to establish security and ensure new partners in the Indian Ocean region. India has presented its credentials to neighbouring countries, increased the number of trips by its warships to regional countries, carried out military exercises, and provided military equipment and training. India has also engaged in joint surveillance and invested in ports to gain regional respect and influence.
Future Scenarios
The West Asia and North Africa States (WANA) region stands at a critical juncture, with competing interests and ambitions shaping its future trajectory. The actions of regional players, such as Turkey, Israel, and Iran, as well as the responses of global powers like the United States, will continue to influence events in the region and impact broader geopolitical dynamics. Possible scenarios include continued instability and conflict, attempts at regional reconciliation and cooperation, or the emergence of new power dynamics driven by changing geopolitical realities.
The future trajectory of West Asia will depend on how various internal and external factors interact in the coming years. Efforts to address root causes of instability, such as governance failures, socio-economic inequality, and regional rivalries, will be crucial in shaping the future of the region.
Author Bio: Dr. Waiel Awwad is a Senior International Independent Journalist & Political Analyst; Former President, FCC South Asia and a Distinguished Advisor (West Asia), Tillotoma Foundation.
References:
[1] The Abbasids maintained an unbroken line of caliphs for over three centuries, consolidating Islamic rule and cultivating great intellectual and cultural developments in the Middle East in the Golden Age of Islam. The Fatimid dynasty broke from the Abbasids in 909 and created separate line of caliphs in Morocco, Algeria, Tunisia, Libya, Egypt, and Palestine until 1171 CE. Abbasid control eventually disintegrated, and the edges of the empire declared local autonomy. The political power of the Abbasids largely ended with the rise of the Buyids and the Seljuq Turks in 1258 CE. Though lacking in political power, the dynasty continued to claim authority in religious matters until after the Ottoman conquest of Egypt in 1517. (7.4: The Abbasid Empire – Humanities LibreTexts).
[2] https://worldaffairs.blog/2018/04/21/debunking-10-lies-about-syria-and-assad/
[3] https://scholar.harvard.edu/files/martinkramer/files/forgotten_truth_balfour_declaration.pdf
[4] https://www.nato.int/strategic-concept/
[5] https://www.britannica.com/event/Sykes-Picot-Agreement
[6] https://www.chinadaily.com.cn/a/202406/01/WS665a545da31082fc043ca533.html
[7] https://mecouncil.org/publication/middle-east-and-the-future-of-international-politics-me-council/
[8] https://www.idsa.in/issuebrief/The-Indian-Navy-and-Maritime-Security-in-the-Red-Sea-SNAhmed-190224
West Asia: A Region in Turmoil
West Asia, a term distinct from the more politically charged “Middle East,” encompasses several sub-regions. These include Anatolia, the Arabian Peninsula, Iran, Mesopotamia, the Armenian highlands, the Levant, Cyprus, the Sinai Peninsula, and the South Caucasus. The Isthmus of Suez in Egypt separates this region from Africa.
The term “West Asia” appears to have gained traction in contemporary geopolitical and economic discourse since at least the mid-1960s.[1] As of 2008, the population of West Asia was estimated at 272 million, with projections reaching 370 million by 2030.[2] The region is predominantly Arab, Persian, and Turkish, as reflected in the dominant languages: Arabic, Persian, and Turkish, each with roughly 70 million speakers. Smaller communities speaking Kurdish, Azerbaijani, Hebrew, Armenian, and Neo-Aramaic languages contribute to the region’s linguistic diversity.[3]
While Islam is a unifying thread across much of West Asia, the region boasts a rich tapestry of religious traditions. Christians, Jews, Baha’is, and Zoroastrians all have a presence here. Even within Islam, there’s a spectrum of denominations, with Sunni and Shia being the most prominent. Furthermore, Islamic practices can vary significantly across cultures, even within these main branches. The Organization of Islamic Cooperation (OIC) is a critical player in West Asian regional politics. Established in Jeddah, Saudi Arabia, in May 1971, it’s the second-largest intergovernmental organisation globally, after the United Nations, with 57 member states spanning four continents. As outlined in its charter, the OIC’s core mission is to represent the Muslim world, safeguard Muslim interests, and promote international peace, security, harmony, and interfaith dialogue. The organisation has emerged as a prominent voice for the Muslim world in global political discourse, offering its perspective on strategies relevant to Muslim-majority nations.
Geographically, West Asia stretches from the eastern Mediterranean, encompassing countries like Syria, Jordan, Iran, and Iraq, to the Arabian Peninsula, including Saudi Arabia. Due to the enormous number of ethnicities within this region, a comprehensive profile would be pretty extensive. Iraq’s population, for instance, is comprised of 76% Arabs, 19% Kurds, and a remaining 5% of Turkmens, Assyrians, Armenians, and smaller groups.
Sectarian strife
West Asia is a critical region in modern history, plagued by inter-state and intra-state conflicts that significantly impact global strategic landscapes. Two key factors contribute to the high degree of unpredictability in these conflicts. Firstly, the vast reserves of hydrocarbons have exposed the entire region to the political and strategic manoeuvring of Western nations, primarily led by the United States. More recently, China has entered the fray, playing the “pro-Muslim card” in its oil diplomacy, with a visible presence in Saudi Arabia and Iran, the world’s top two oil producers.
The 1979 Islamic Revolution in Iran, deeply rooted in the country’s Shia traditions, marked a turning point in contemporary regional politics, igniting sectarian consciousness. The revolution manifested the growing prominence of political Islam in West Asia, challenging the “secular” enticements of pan-Arabism and pan-Islamism that had dominated the 1960s. Iranian jurists framed the revolution as “Islamic,” not a purely sectarian claim. As Talmiz Ahmad writes, “Many Sunnis initially viewed it as a successful mobilisation of Islam against a Western-backed secular regime, while others saw it as promoting the interests of ‘the poor and the oppressed.'”[4]
Drawing a parallel, Tunisian Islamist intellectual and political leader Rashid al-Ghannoushi linked the Khomeini revolution to the “global Islamic project” championed by prominent figures of political Islam like Abul Ala Mawdudi and Hassan al-Banna (founder of the Muslim Brotherhood). In their view, Islam provided a strong foundation for seeking freedom for their people from authoritarian and colonial control.[5]
Salafis and al Qaeda
In Saudi Arabia, Salafis, followers of Ibn Taymiyya’s teachings (1263-1328), are increasingly represented by a younger generation of scholars. These scholars defer to established Salafi jurists but consider themselves more knowledgeable not only in religious matters but also in contemporary issues like history, politics, and world affairs. A significant Salafi faction advocates for violence to establish their ideal Islamic society. Their ideology traces back to the “global jihad” organised in 1980s Afghanistan by a coalition of Saudi Arabia, Pakistan, and the United States.[6]
To bolster this state-backed jihad, thousands of young Muslims flocked to Afghanistan’s battlefields. There, they received indoctrination in Salafi Islam alongside weapons and subversion training. The Soviet withdrawal and subsequent collapse were hailed by jihadists as a victory of Islamic monotheism over Western atheism, or more simply, Islam’s triumph over the West. The fall of an atheist power, in their view, confirmed the righteousness of their fight. Returning home, these Arab Salafis, influenced by the “Sahwa” ideology (meaning awakening or introspection), demanded reforms in 1994, envisioning a “conservative Islamic democracy.”[7]
With the backing of the religious establishment (ulema), the Saudi regime cracked down on the Sahwa movement in 1994. This forced jihadists to emerge from the shadows of Sahwa al-Islamiyya. In August 1996, Osama bin Laden, a previous supporter of Sahwa, issued his “Declaration of Jihad against the Americans occupying the Land of the Two Holy Places.”[8] This declaration served as the foundation for a new “global jihad” led by al-Qaeda. Bin Laden viewed the conservative religious scholars (ulema) as instruments of the Saudi state, used to suppress “genuine” scholars who were truly committed and willing to fight for their beliefs. Two years later, in February 1998, al-Qaeda further escalated tensions with their announcement that “killing Americans and their allies, civilians or military personnel, is an individual duty for every Muslim wherever possible.” Talmiz Ahmad concludes that this declaration served as a rallying cry for global jihad, culminating in the events of 9/11 and its subsequent spread across West Asia and North Africa.[9]
Conflicts
West Asia occupies a critical position on the world stage, holding immense strategic, political, economic, and religious significance. Its energy resources and strategic location make it particularly important for the United States and emerging powers like India and China. The region boasts a rich history, having served as the cradle for numerous civilisations. However, for the past two centuries, it has become a battleground for the interests of major foreign powers. In present times, West Asia faces growing instability due to a multitude of conflicts. The ongoing tensions between Israel and Hamas, the hostility between Iran and Israel, the civil war in Yemen, and the presence of Iranian-backed militias in Lebanon all contribute to the region’s volatility.
The Sykes-Picot Agreement
After the downfall of the Ottomans, their former territory was divided among the victorious allied powers, chiefly Britain and France. The Sykes-Picot Agreement was a 1916 unofficial treaty between the United Kingdom and France, with assent from the Russian Empire and Italy, to define their mutually agreed spheres of influence and control in an eventual partition of the Ottoman Empire. The primary negotiations leading to the agreement occurred between 23 November 1915 and 3 January 1916, on which date the British and French diplomats Mark Sykes and François Georges-Picot initiated an agreed-upon memorandum.
The agreement effectively divided the Ottoman provinces outside the Arabian Peninsula into areas of British and French control and influence by the Sykes-Picot line. The agreement allocated to Britain the control of what is today southern Israel and Palestine, Jordan and southern Iraq, and an additional small area that included the ports of Haifa and Acre to allow access to the Mediterranean. The Arabs were not consulted abut the border change. Consequently, hostile tribes and factions were lumped together, a breeding ground for perpetual conflict.
The Israeli-Palestinian Conflict: A Historical Impasse
The Palestinian territory holds significant religious significance for Judaism, Christianity, and Islam, with Jerusalem serving as a holy city for all three. It enshrines some of their most sacred sites. In 1917, during World War I, the British government issued the Balfour Declaration. This declaration announced support for the establishment of a “national home for the Jewish people” in Palestine, then an Ottoman territory with a relatively small Jewish population. The declaration significantly boosted global Jewish support for Zionism and became a cornerstone of the British Mandate for Palestine, which later gave rise to Israel and the Palestinian territories.
The Balfour Declaration is widely considered a primary cause of the ongoing Israeli-Palestinian conflict, a dispute that has tragically claimed tens of thousands of lives and displaced millions. The conflict’s intractability often stems from the British government’s perceived contradiction of its previous assurances to the Arabs of Palestine regarding their role in governing the new nation.[10] Palestinians aspire to establish an independent state, ideally encompassing at least a portion of historical Palestine. However, achieving this goal remains elusive due to several factors such as Israeli defense of its borders and its control over the West Bank, the Egyptian-Israeli blockade of the Gaza Strip and internal political divisions within Palestine.
The Syrian Imbroglio
Syria is home to diverse ethnic groups and religious denominations such as the Syrian Arabs, Turkmen, Kurds, Assyrians, Circassians, Armenians, Greeks and Mandaeans, with Arabs being the largest ethnic group. Syria’s religious groups include Sunnis, Alawis, Shiites, Christians, Jews, Mandaeans, Druze, Salafis, Ismailis and Yazidis. The largest religious group is Sunni Muslims. In 1963, there was a Ba’athist coup d’état after which the Ba’ath Party maintained its power. From 1963 to 2011, the country was in a state of emergency, which meant that citizens did not have constitutional protections.
Several political scientists, military experts, and journalists have stated that the Syrian Civil War is primarily rooted in a feud between Russia and the United States and their allies in the region over natural gas pipelines passing through Syria on their way to European markets.[11] The ongoing conflict in Syria is widely described as a series of overlapping proxy wars between the regional and world powers, primarily between the United States and Russia as well as between Iran and Saudi Arabia.
Iran, a Shia country, sees Assad, a Shia, as its closest ally in the Arab world. Russia has carried out airstrikes against the protestors and supports the Syrian government in the UN. Syria has Russia’s only Mediterranean naval base and an airbase, apart from other military interests. Foreign Shia militias are recruited by Iran from Yemen, Afghanistan, and Iraq to fight in Syria. A coalition (SNC) of anti-government factions, based in Turkey, aims to set up a civil and democratic state in Syria. Several Gulf States have recognised the Coalition (SNC) as the legitimate government of Syria. The USA gives weapons, training, and military assistance to the rebels. Following the defeat of ISIS, the United States exited Syria. The Syrian government and rebel groups opposed ISIS and, after the latter was defeated, took over the territory that ISIS had previously controlled.
Iran-Israel feud
The downward spiral of Israel-Iran relations began with the 1979 Iranian revolution. Iran’s new Islamist regime viewed Israel as a Western colonial outpost and Zionism as a version of imperialism. Israel’s invasion of Lebanon in 1982 led to Iranian support for the creation of Hezbollah in Lebanon. After the end of the Cold War, Israeli strategy shifted from engaging with states on its periphery to building on its 1979 peace agreement with Egypt. Towards that end, it chose to perpetuate Iran’s isolation, viewing opposition to Iran as promoting nascent Arab-Israeli cooperation. A significant concern of Israel is Iran’s nuclear programme, which it considers an existential threat. Periodic statements by Iranian leaders of decimating Israel reinforce such concerns.
Iran’s hostility to Israel also extends to the Arab states who are trying to befriend Israel. Consequently, Tehran has raised militant outfits and deployed them as its proxies against the Arab states: Hezbollah in Lebanon, Hamas and Islamic Jihad in the Gaza Strip, Shi’ite militias in Syria and Iraq, and the Houthis in Yemen. Iran’s Islamic Revolutionary Guard Corps (IRGC) Quds Force—a branch of the Iranian Armed Forces, manages these proxies. To support these proxies, Iran has made massive investments in raising vast stockpiles of rockets, missiles and drones. The use of proxies provides Iran deniability and shields it from accountability for its destabilising policies.[12] In 2019, the US State Department designated the IRGC as a whole as a foreign terrorist organisation (FTO).
Hamas-Israel bellicosity
Hamas, an acronym for Harakat al-Muqawama al-Islamiya (Islamic Resistance Movement), is the largest and most capable militant group in the Palestinian territories. It emerged in 1987 during the first Palestinian uprising, or intifada, as an outgrowth of the Muslim Brotherhood’s Palestinian branch. The group is committed to armed resistance against Israel and the creation of an Islamic Palestinian state in Israel’s place. Hamas has been the de facto governing body in the Gaza Strip since 2007. It was designated as a terrorist organisation by the US State Department in October 1997.
In attacks on Israel as well as against ISIS and other Salafist armed group members based in Gaza, Hamas uses improvised explosive devices, short- and long-range rockets and mortars, small arms, and also man-portable air defence systems, antitank missiles, and unmanned aircraft. It also resorts to kidnapping, cyber espionage, and computer network exploitation operations. The October 7, 2023, attack by Hamas on Israeli civilians resulted in the deaths of 1,189 Israelis, with several Israelis also taken hostage, which led to the present Israel-Hamas war.[13] Israel’s military retaliation has killed at least 36,096 people in Gaza, mostly civilians, according to the Hamas-run territory’s health ministry.[14] Despite efforts by the US towards that end, there appears to be no end to the conflict. West Asia thus remains mired in a cycle of violence, fuelling regional tensions and rivalries between regional entities. As the hub of international trade and transit, the region’s instability adversely impacts global trade.
India-West Asia relations
India has significant stakes in the region, including energy, trade, and the large India diaspora. West Asia accounts for 70% of India’s imported energy demand. It is the gateway to landlocked and energy-rich Central Asia. The proposed North-South International Corridor will pass through some West Asian countries, bringing prosperity to their peoples. Economic links between India and the GCC nations are strengthening and increasing mutual reliance. India’s third and fourth-largest commercial partners are the United Arab Emirates and Saudi Arabia. India has the world’s third biggest Muslim population, with Saudi Arabia as an important pilgrimage destination. Six West Asian nations (UAE, Saudi Arabia, Kuwait, Oman, Qatar, and Bahrain) account for over 70% of all Indians living abroad. Their remittances help stabilise the Indian economy.
India has invested in Iran’s Chabahar port, which will serve as a commerce bridge connecting India, Iran, Central Asia, and Afghanistan. India has strong defence and security relations with Israel, which benefits its security and military modernisation efforts. West Asia is an essential aspect of India’s Indo-Pacific maritime realm. Naval cooperation is already gaining traction, with Oman granting Indian naval warships berthing rights in the Gulf of Aden to combat piracy. And finally, close collaboration with West Asian states is significant for India to fight radicalism and growing terrorism.
Conclusion
West Asia is the most militarised region of the globe. Energy resources and religion are at the root of conflicts. Several peace formulae have been proposed over the years but have failed. For durable peace, the foremost condition is that all denominations must accept that everybody has a right to live and prosper. External forces must curtail their interference in bilateral or multilateral engagement in disputed areas. Iran must disband or withdraw its proxies from the entire region. Many world powers and the UN strongly recommend the formula of creating two states in Palestine.
For India, peace in the region is a vital concern. India has good relations with the Arab states and Israel and is thus in a position to play a positive role in any future peace initiative to bring about a lasting solution to the many conflicts plaguing the region.
Author Bio: Shri K N Pandita has a PhD in Iranian Studies from the University of Teheran. He is the former Director of the Centre of Central Asian Studies, Kashmir University.
References:
[1] The Tobacco Industry of Western Asia, U.S. Department of Agriculture, Foreign Agricultural Service, 1964.
[2] Data for “15 West Asian countries”, from Maddison (2003, 2007). Angus Maddison, 2003, The World Economy: Historical Statistics, Vol. 2, OECD, Paris, ISBN 92-64-10412-7.
[3] Laing-Marshall, Andrea (2005). “Assyrians”. Encyclopedia of the World’s Minorities. Vol. 1. New York-London: Routledge. pp. 149–150. ISBN 978-1-135-19388-1
[4] Turmoil in West Asia, IDSA Monograph Series No. 50 April 2016, p 8-9
[5] Brigitte Marechal and Sami Zemni, The Dynamics of Sunni-Shia Relationships:
Doctrine, Transnationalism, Intellectuals and the Media, Hurst & Company, London, 2013, p. 228.
[6] Turmoil in West Asia, loc, cit. p.25
[7] Guido Steinberg, “Jihadi-Salafism and the Shias”, in Roel Meijer (ed.), Global
Salafism, Hurst & Company, London, p.117
[8] Turmoil in West Asia, loc cit. P 25
[9] Loc. cit p. 26
[10] For a full description of Israeli oppression of Palestinian Arabs see ‘1948 Palestinian expulsion and flight’ on Wikipedia
[11] https://byjus.com/free-ias-prep/syrian-civil-war/
[12] US States Department official website: https://www.state.gov/reports/country-reports-on-terrorism-2021/iran/
[13] AFP – Agence France Presse May 28, 2024: https://www.barrons.com/articles/new-tally-puts-oct-7-attack-death-toll-in-israel-at-1-189-3e038de6
[14] For a fuller description of the Israel-Hamas wars including the tragedy of 7 October 2023, see ‘Hamas attack October 7 a day of hell on earth in Israel’ by Samual Forey, Le Monde, October 30, 2023
POWER PLAY: THE CHINA, RUSSIA, IRAN, NORTH KOREA AXIS (CRIK)
Abstract
The world is in the throes of an intensifying contest between what seems to be a crumbling old order (USA-led West) and a rivalrous new Axis that is struggling to be born: China-Russia-Iran-North Korea (CRIK). This article seeks to analyse the nature of the emerging power play in terms of the following:
- Geo-Strategic Context
- CRIK as a Geopolitical Conglomerate
- The Wider Karma Bhoomi: BRICS & The Global South
- Pushback by the USA led West
- Prospects for the Future
At the Kremlin on 22nd of March 22, 2023
|
Geo-Strategic Context
Award-winning journalist John Pilger recounts Chairman Mao’s fervent appeal to Washington in 1944: “China must industrialise; this can only be done by free enterprise. Chinese and American interests fit together economically and politically. America need not fear that we will not be cooperative. We cannot risk crossing America; we cannot risk any conflict.” He received no reply[1].
Mao’s successors, a while later, decided to join the system and beat the USA at its own game—capitalism & innovation—and are now in bed with its bête noire Russia to challenge the American-led order. Russia and China sense opportunity, perhaps even smell blood, at the prospect of a visible decline in American power and are coming together in the hope of hastening the latter’s fall. We are, therefore, in a new kind of Cold War—one in which to quote Henry Kissinger, we are now closer to the mountain passes than the foothills[2] (he said this in 2020). By 2021, in Dr. Kissinger’s view, the Cold War had moved “through the mountain pass,” and was now “on a precipice.”[3] In this war, one protagonist is the USA-led West. In the antagonist camp, China has replaced the Soviet Union, and is partnering with its successor, Russia (the prickly past, notwithstanding), in a very consequential ‘friendship without limits.’ Iran and North Korea (the hop over of Iran is significant because not very long ago, when the JCPOA was being negotiated, Russia, USA, and China were on one side while Iran was on the other) have strengthened the sinews of this New Axis significantly. Three decades after the end of the first Cold War, the USA finds itself in a volatile rivalry with the two other nuclear powers—China and Russia, in a world far more complex and dangerous than it was a half-century ago[4]. The evolving power play has created the precise construct that Kissinger had warned about—a Bear-Dragon tandem in such delightful synchrony, that the USA is now faced with a humongous challenge: that of the Russian storm and the Chinese climate change, all together and all at once.
The New Axis has not only performed well in the Ukrainian and West Asian theatres of war but is also looking towards the global south (125 countries, 80% of the global population, 40 % of global GDP) as its wider ‘Karam Bhoomi’ with a rapidly expanding BRICS (the five original members have become ten and as many as fifty-nine from Thailand to Nigeria and Turkey are waiting to join) as the chosen instrument of delivery.
The state of global dysfunctionality today is so severe that there is a real possibility of the world getting divided into two sets of rules, orders, economies, and the internet. This potential division could have far-reaching implications for global affairs.[5]
What, then, is the nature of the New Axis? Is it merely a short-term convergence of interests, or are we witnessing the birth of a new, long-term geopolitical conglomerate? What are its objectives? What has it achieved thus far? What are the possible pointers and prospects for the future? These questions invite us to delve deeper into the complexities of this emerging global power axis.
CRIK As a Geopolitical Conglomerate
The centrepiece of the Axis is China, where, behind the patina of capitalism, there is still a Communist Party in charge, one driven by Marxism and Leninism.[6] Yet, the Axis seems to be driven less by ideological congruence and more by a desire to challenge the USA, its worldview, and what some analysts describe as ‘a hyper power stomping all over the world.’[7] Noted Chinese commentator Eric Lee, claims that Chinese ambitions are modest in relation to its weight – “We do not want to run the Asia-Pacific, let alone the world. All we want is that America should stop dominating the Asia-Pacific and the world”. Aggression and hegemonic ambitions are not Chinese culture, he asserts. “We built the Great Wall to keep the barbarians out, not to invade them.”[8]
Putin and Xi have met more than forty times; they are focused on combining their power and influence to stand up to the United States, frustrate US ambitions and speed along what they believe is America’s inevitable decline.[9] The Sino-Russian relationship is closer than at any time since the Korean War. It was in 2014 that the proximity began to grow – Russia, under sanctions after the annexation of Crimea, was looking for friends, and Xi was beginning to get more assertive about his foreign policy. Between 2013 and 2021, China’s share of Russian external trade doubled from ten to twenty per cent; between 2018 and 2022 Russia supplied 83 % of China’s arms imports – helping the Chinese military grow its air defense, anti-ship and submarine capacities significantly to make it a formidable military instrument in the Western Pacific.[10]
The full-scale invasion of Ukraine in February 2022 accelerated the process; the meeting in the Kremlin of March 2023, alluded to at the head of this article, may have sealed the romance with a kiss. North Korea, Iran and China, cumulatively, have contributed in substantial measure to the military resurgence of Russia in the Ukraine conflict. North Korea has supplied Hwasong-11A missiles and artillery munitions (2.5 million rounds), while the Iranians have supplied more than 3,700 low-cost Iranian drones. Three hundred thirty of these drones are now being manufactured locally, in Tatarstan (in Russia), every month for use in the Ukrainian theatre. The Iranians have leveraged the data generated in the Ukrainian theatre, carried out qualitative upgradations, and demonstrated the consequential prowess on Apr 14, 2024 (the missile-drone barrage on Israel). China, too, it is now clear as daylight, has supplied an array of military equipment to resurge the Russian war effort and re-invigorate its military-industrial complex: engines for drones, parts for jet fighters, radar & communication jamming equipment, precision machine tools, micro-electronics (for use in missiles & glide bombs) as also CNC machines (while the technical translation is ‘computer numerical control’ in practice the terms alludes to computer-controlled instruments used for metal processing and manufacture of munitions and aircraft).
In the first six months of 2023, Russia received drone shipments from Chinese trading companies valued at USD 14.5 million, while Ukraine received only USD 200,000 worth of similar shipments. The performance of Russian airpower having been denied the supply of tailor-made, high-end components from the West, due to sanctions, was for a long-time under-whelming. Due to a successful transition to dual use, cheaper, Chinese electronics, it has made a strong comeback in the Russian counter-offensives in Avdiivka and Kharkiv.[11] Russian reciprocity has been equally noteworthy – it is helping North Korea, for instance, in the launch of satellites/spaceships and has de-frozen North Korean financial assets lying in Russian banks. President Putin’s visit to North Korea in June 2024 (his first to Pyongyang in 24 years) is more than a propaganda coup for Kim – the strategic partnership that has been concluded is one of Moscow’s strongest security commitments in Asia, one that pledges “military and other assistance” if one of the signatories is invaded or in a state of war. Cheong Seong-Chang, an analyst at the Sejong Institute, a think-tank in Seoul, has compared the Kim-Putin pact with the South Korea-US mutual defense treaty.[12] In reaction to the pact, South Korea has said it is considering supplying weapons to Ukraine, while an American senator has called for the re-deployment of nuclear weapons to the Korean peninsula.[13]
Meanwhile, North Korea has been upping the ante, along both the land (DMZ – Demilitarised Zone) and maritime frontiers (NLL – Northern Limit Line) with South Korea. North Korea could also prospectively play a very significant role in the Taiwan contingency – activating the Korean peninsula, so as to keep the South Koreans tied down. If South Korea follows up on its offer to supply arms to Ukraine, given its deep stockpiles of howitzers and artillery munitions, it could be critical for Ukraine’s war effort. In sum, the Putin-Kim pact will have grave implications – not only for stability in the Korean peninsula but also for the trajectory of the war in Ukraine.
The other areas of collaboration namely food supplies, energy, space and the nuclear domain also sends signals that Russia is prioritising Pyongyang over the international non-proliferation regime and Russia’s obligations as a member of the UN Security Council. Russia has also vetoed the renewal of a UN panel that monitors compliance with Security Council sanctions against North Korea.
Iran and Russia, similarly, came together to keep Syrian President Bashar-al-Assad in power, in the wake of the civil war in 2011. Russia has signed major energy agreements with Iran to shield Tehran from the effects of US sanctions; it is now among the top suppliers of weapons to Tehran and is its largest source of foreign investment. Russian exports to Iran rose by 27% in the first ten months of 2022. China, too, has stepped up oil purchases from Iran significantly since 2020. Iran has been purchasing North Korean missiles since the 1980s; more recently, North Korea has supplied weapons to Hezbollah and possibly even the Hamas. There also is evidence to suggest that Chinese engineering know-how has been used in the design of the Hamas tunnels in Gaza. China, Iran, and Russia have held joint naval exercises in the Gulf of Oman for three years, most recently in March 2024. Trilateral naval drills involving Russia, China, and North Korea in the Seas of Okhotsk, Japan, and the East China Sea are also on the anvil.
More importantly, the deepening cooperation between the Axis nations has helped to circumvent the foreign policy tools (sanctions) that the West crafted to contain them; it has provided political top cover at forums like UN and is also being used to sharpen the information narrative through instruments like TikTok. It is becoming increasingly difficult to isolate the CRIK nations individually when they work together. The collective nuclear arsenals of the CRIK nations, it may be noted, in a few years are estimated to be twice as large as that of the United States.[14]
There is also wider contestation, driven strongly by the desire to shape what comes next. With Western sanctions blocking Russian access to European markets, Russian businesses have turned to China –industrial valves used mainly in the oil & mining sectors, offer a low-cost alternative to the European brands. Bilateral trade between Russia and China was USD 240 billion last year with the Chinese shipping cars, industrial machinery and smartphones to Russia. Russia, in turn, has replaced Saudi Arabia as the largest oil supplier to China.[15]
Russia has transmuted into a war economy that is now churning out more munitions than the USA and the entire West put together. While Russia’s annual defense spending has grown to USD 386 billion, the economy is also growing at 5.5% annually; with inflation running high at 7.4%, foreign investment has collapsed, and with trade with the West having been cut off, Russia has been pushed deeper into China’s economic embrace[16]. According to President Zelensky, at the Russian prompt, China used its considerable influence to sabotage the recently held, Ukraine Peace Summit in Burgenstock.[17]
While the slogan is multi-polarity, in practice, we are seeing the Axis challenging the foundational precept of American power – the freedom of the American Military to roam the globe, especially where such freedom intersects with the perceived spheres of influence of the Axis nations: Chinese ‘core interests’ in Taiwan and the South China Sea; Russia’s ‘near abroad’ – Novorossiya, so to speak; the Iranian proxy enterprise in Iraq, Lebanon, Syria & Yemen; as also the Korean peninsula. Concurrent escalation in the four theatres is fragmenting American power in significant ways. For example, whether this is a consequence of skilful CRIK statecraft or a series of geopolitical coincidences, is of course a matter of speculation. The dilemma before the Americans is whether they fight in three theatres or focus on winning in one. The USA must prioritise its strategic engagements – it does not have the military bandwidth to fight in two, let alone three theatres.[18] With a debt pile of USD 35 trillion and debt servicing pegged at USD 1 trillion (that which exceeds its defense budget at $950 billion), there is little wriggle room for the Americans to grow that bandwidth across multiple theatres.
The Russo-Chinese pitch is for a new polycentric, multi-nodal (nodes that engage and not poles that are in perpetual contest) world order that is more reflective of the globe’s diverse cultural and civilisational identities, as opposed to a monochromatic, Western view of the world. The Axis is not a formal grouping, yet it is one that is growing in strength and co-ordination. The growing intensity of the Sino-Russian co-operation is clear from the joint manifesto signed between Presidents Vladmir Putin and Xi in early 2022 that spoke about a ‘friendship without limits’ and called for ‘international relations of a new type,’ in other words, a multipolar system that the United States no longer dominates.
During President Putin’s recent visit to Beijing in May 2024, there were references to a ‘new era.’ A sweeping joint statement laid out roadmaps for the countries’ alignment on a host of issues including energy, trade, security, and geopolitics with specific references to Ukraine, Taiwan and conflict in the Middle East. The statement proclaimed that China-Russian relations have stood “the test of rapid changes in the world, demonstrating strength and stability and are experiencing the best period in their history,” the two leaders calling each other “priority partners.” Quite symbolically, Putin attended trade and cooperation forums in Harbin, the capital of China’s northeastern Heilongjiang province bordering Russia’s Far East. This region erupted in conflict between China and the Soviet Union in 1969. Putin also met with the students and faculty of the Harbin Institute of Technology; a university sanctioned by the US government in 2020 for its alleged role in procuring items for China’s military.
In terms of outcomes and delivery however, the Axis has been far more effective than even formal alliances, certainly more effective than NATO, it would seem; the ‘arsenal of the Axis’ is doing far better than the ‘arsenal of democracies.’ China’s industrial production capacities (value added) in 2004 were half that of the USA; today, they are two times larger. In natural consequence, the Chinese military- industrial complex today, is 5-6 times more efficient than its American counterpart. Cognisant of the renewed potency of the Russian war machine, the Americans have decided to undertake manufacture of artillery munitions on a war footing. Even with full scaling up they shall be able to deliver only 1.5 million rounds/month to Ukraine by the end of 2025; the Russians are currently producing 5 million rounds per month. Two days before the fall of Avdiivka, an operational audit of two Ukrainian brigades was carried out: one had a bare 15 artillery rounds left, the other had a mere 42 mortar rounds in its kitty.
A conceptual battle between the two systems, framed within the dynamic of democracy vs delivery, has also begun.[19] The Chinese argue that while the West champions individual freedoms, the Chinese prioritise broader societal order over personal liberties. They posit that in the USA, politicians are at the mercy of capitalists; China they argue, while it fosters the spirit of free thinking, innovation and enterprise, is not hostage to capitalist greed. That should explain the party-market standoff and the taking down of Big Tech to include big names like Jack Maa. In terms of poverty alleviation and social delivery, the Chinese system, they claim, is better than the West. The Axis nations reject the Western brand of democracy, while insisting that individual states have the right to define democracy for themselves. They oppose external meddling in their internal affairs, the expansion of US alliances, the stationing of American nuclear weapons abroad, and the use of coercive sanctions[20].
Though the current alliance may not be permanent, the shared goal of challenging the U.S.-led world order serves as a strong enough glue to keep it together for the foreseeable future, perhaps the next decade.
The Wider Karma Bhoomi
China and Russia in particular and the wider Axis, are also moving the game for impact and influence to other areas of the world, including the Global South. In Asia, Africa, Latin America and the Middle East, the Axis is making significant inroads. Look at how CRIK in general and China in particular, are chipping away at American attempts at containment, through some very smart, agile, fleet-footed responses. When ASEAN was formed in 1967, it was seen as a pro-West grouping. Yet, it was China that proposed an FTA with ASEAN in 2000. While ASEAN’s trade with the US grew from USD 135 billion in 2000 to USD 450 billion in 2022, trade with China boomed from USD 40 billion to USD 975 billion in the same period. Today, the ASEAN-China trade relationship dwarfs the EU-US relationship, valued at USD 950 billion.[21] China is the top trading partner for over 120 countries, including those traditionally aligned with the West and, more importantly, those seeking economic independence from Western dominance.
The BRI, RCEP, and AIB are the instruments of the alternate economic corridor that China is seeking to create—one designed ingeniously to tether China’s phenomenal manufacturing capacities with the material/needs of the world. We can gauge the success of such a strategy from the rapid expansion of BRICS and from the number of countries wanting to join the Shanghai Co-operation Organization (SCO) and the Eurasian Economic Union (EEU). Turkey, a member of NATO, has evinced interest in joining BRICS,[22] due to slowing economic growth in Europe and to the expanding opportunities in BRICS. The contribution of the BRICS economies to the global economy at 36%, exceeds that of the G-7.
There are other contests, too, though still in their relative infancy: De-dollarisation and new avenues of Energy Convergence. The re-set of the petro-dollar by Saudi Arabia, which has moved away from trading in oil exclusively through the dollar, could be an indicator of things to come. At the recent St Petersburg International Economic Forum (05-08 June 2024), President Putin said that the BRICS would soon develop an alternate payment system immune to unfair sanctions from the West.[23] China is a good market for Siberian gas now that Europe is not buying energy from Russia- described by Western commentators as a ‘gas station.’ In fact, Russia seems determined to prove that it is far more muscular and influential strategically than a mere ‘gas station.’
The Pushback: USA-led West
The above notwithstanding, it needs to be noted that the USA continues to be formidable: it accounted for 25% of the world’s GDP in 1980, and it still does. The Chinese economy has grown at the expense of Europe and others, not the United States. Seven of the world’s largest big tech companies continue to be American. America still has the world’s largest, technologically most adept military, albeit one that of late has been delivering sub-optimally: a grand initiator of conflict but a rather poor finisher. The Liberal Order, we must remind ourselves – USA, Europe, Australia, Japan, South Korea, and Singapore still account for 65% of global GDP, 75% of global military spending and 95% of ideation/global agenda setting.[24]
There is an attempt to ingest the hub and spoke alliance-partner framework with a fresh dose of energy and resolve: the USA-South Korea-Japan Tri- lateral, Quad, Squad, the resilience of the Filipinos in the Second Thomas Shoal are pointers to the fact that Chinese maritime prowess will not be allowed to break out from the first island chain with ease; IPACOM meanwhile, has been talking of a ‘hellscape’ to deter a prospective Chinese invasion of Taiwan. ‘Brain dead’ NATO also seems to be regenerating to life. On June 19, 2024, NATO Secretary-General Jens Stoltenberg warned that, “when they are more and more aligned – authoritarian regimes like North Korea and China, Iran, Russia – then it’s even more important that we are aligned as countries believing in freedom and democracy.”[25] NATO trendlines seem to be in synch with the sentiments of its Secretary General: by the end of this year, 18 NATO member states will enhance their defense expenditure to 2% of GDP. NATO is also debating the prospect of making 3 % the floor of defense spending.
The West, in general, is gearing up for the prospect of war; there is talk of a draft in Europe. So, the fight for ascendancy will be grim. Nobody has greater respect for the Americans as a comeback nation than the Chinese themselves. They know that it is way too early to proclaim victory. Xi’s challenge, therefore, is not only deeply thought through but also firmly undergirded by an order of his own making—CRIK is just the beginning.
Prospects for the Future
The next decade is critical. The two conflicting orders, one led by the USA-led West and the other defined by CRIK, are poised for intense competition, multiple crisis as also an intense clash of wills, which could also spillover into conflict. Great sagacity & wisdom will be needed to avoid wider war, as also considerable acumen to craft what may at best may an uneasy peace. Either way, we must brace up for the greatest show in human history.
In Cold War 1.0, a number of countries to include India, chose to be non-aligned and kept a distance from either bloc; while the moral persuasions of the non-aligned were strong, since they lacked geo-strategic heft, their material influence was not quite as material. In the current Cold War, countries like Brazil, South Africa, and India have reflected a new reality with sufficient heft, influence, and strategic autonomy to shape outcomes meaningfully. The salience of these global swing states in the ensuing contest between the two orders will be potent.
An assessment of the relative strengths of the two orders suggests that while the West, particularly the USA, will retain its supremacy, it will lose its hegemony. The USA needs to make strategic adjustments whence it is no longer the undisputed numero-uno. CRIK is not asking for a seat at the table; they are looking to build their table, one with their own rules. Therefore, the world could be headed towards an unusual experiment – one where a liberal international order sans a hegemon and CRIK learn to co-exist. The hazards arising out of the challenges of climate change, a nuclear catastrophe and now the horrific consequences of irresponsible AI, must drive the contest towards a thoughtful modus vivendi. Détente 2.0 – a smart admixture of engagement, deterrence and containment – may be the wisest way of stabilising Cold War 2.0.[26].
Author Bio: Lieutenant General Raj Shukla, PVSM, YSM, SM, is a former General Officer Commanding-In-Chief – Army Commander – of the Indian Army’s Training Command (ARTRAC). He is presently ‘Member UPSC,’ w.e.f. 18th July, 2022.
References:
[1]China vs. United States | Cold War | Nuclear Threat | Investigative Journalism (youtube.com) , accessed on 18 May 2024
[2]Niall Ferguson, Kissinger and the True Meaning of Détente: Reinventing a Cold War Strategy for the Contest With China (foreignaffairs.com), accessed on 30 May 2024
[3] David K. Sanger, New Cold Wars, Crown Publishing Group, 2024, page 446.
[4]David E Sanger, New Cold Wars, Crown Publishing Group, 2024, Inner Flap
[5]Antonio Guterres, UN Chief: We Must Avoid US/China Cold War, Associated Press, 25 Sep 2021, www.youtube.com
[6]Niall Ferguson in conversation with Urs Gehriger, The New Cold War, Die Weltwoche (Swiss weekly magazine based in Zurich), 03 May 2024
[7]Putin meets Xi Jinping in Beijing | Carl Zha Reacts (youtube.com) accessed on 17 May 2024
[8]China vs. United States | Cold War | Nuclear Threat | Investigative Journalism (youtube.com) , accessed on 18 May 2024
[9]David E Sanger, New Cold Wars, Crown Publishing Group, 2024, p 9
[10] Andrea Kendall-Taylor and Richard Fontaine, The Axis of Upheaval, Foreign Affairs, May/June 2024
[11]Frank Hofmann, How China indirectly supports Russia’s war in Ukraine – DW – 05/16/2024, accessed on 01 June 2024
[12] Song Jung-a in Seoul, Kana Inagaki in Tokyo and Joseph Leahy in Beijing, Japan and South Korea sound alarm over Putin-Kim pact, Financial Times, 20 June 2024
[13] South Korea considers sending weapons to Ukraine in response to Russia-North Korea deal | DW News (youtube.com), accessed on 21 June 2024
[14]Robert M. Gates, The United States now confronts graver threats, The Dysfunctional Superpower, Foreign Affairs, 29 Sep 2023
[15]Joe Leahey, Kai Waluszewski & Max Seddon, China-Russia: an economic ‘friendship’ that could rattle the world, Financial Times– The Big Read, 15 May 2024
[16]Jennifer Sor,Russia’s economy is so driven by the war in Ukraine that it cannot afford to either win or lose, economist says (msn.com), accessed on 01 June 2024
[17]Zelensky Says China Is Helping Russia Undermine a Peace Summit on Ukraine (msn.com), accessed on 02 June2024
[18]Elbridge Colby, Why Should We Care About America’s Defense Priorities? (youtube.com) accessed on 02 June 2024
[19]Nicholas Burns, US Ambassador to China,us china rivalry taiwan and hongkong 60 minutes – Search Videos (bing.com). accessed on 02 June 2024
[20] Andrea Kendall-Taylor and Richard Fontaine, The Axis of Upheaval, Foreign Affairs, May/June 2024
[21] محاضرة رفيعة المستوى | اتجاهات العلاقات الأمريكية – الصينية بعد الانتخابات الأمريكية 2024 (youtube.com), Kishore Mahbubani on Prospects for US-China Relations, High Level Lecture at the Emirates Centre for Strategic Studies & Research, ECSSR, accessed on 22 June 2024
[22] Why Turkey Joins BRICS and How This Will Impact the World – YouTube, accessed on 20 June 2024
[23] Western Empire Facing Same Collapse as Rome in its Final Days: Martin Armstrong – YouTube, accessed on 21 June 2024
[24] London Conference 2024: Dr Fareed Zakaria and Bronwen Maddox (youtube.com), accessed on 22 June 2024
[25] Song Jung-a in Seoul, Kana Inagaki in Tokyo and Joseph Leahy in Beijing, Japan and South Korea sound alarm over Putin-Kim pact, Financial Times, 20 June 2024
[26] Naill Ferguson, Kissinger and the True Meaning of Détente – Reinventing a Cold War Strategy for the Contest With China, Foreign Affairs, March/April 2024
A High-stakes Game
Since independence, India’s foreign policy has been remarkably consistent, resting on the twin pillars of economic prosperity (Samriddhi) and national security (Suraksha). A noticeable shift in foreign policy formulation took place after Prime Minister Narendra Modi assumed office in 2014, which saw three additional pillars being added to the existing two: ‘Samman’ (emphasising India’s dignity and honour), ‘Samvad’ (increased engagement with the global community), and ‘Sansriti’ (leveraging India’s cultural and civilisational heritage as a foreign policy tool). The new approach is grounded in pragmatism, being more assertive, bold, and proactive.[1] This has resulted in a dramatic turnaround in India’s relations with the global community, particularly with the West Asian countries.
Speaking at the Raisina Dialogue in 2016, India’s then External Affairs Minister, Ms. Sushma Swaraj, spoke of “bringing a new sense of purpose to our foreign policy.” She said, “India can and should raise its international profile” and “leverage our diplomatic influence to accelerate development at home… and send the message that India’s growth can be the world’s opportunity.” She also spoke of policy choices to drive change and emphasised the role of net security providers in maintaining global order.[2] In his keynote address at the same conference, the then foreign secretary (now India’s foreign minister), Shri S. Jaishankar, mentioned this change in India’s engagement with the Gulf countries. He said that despite a strong historical connection to West Asia, India’s links to the Gulf countries had come to be defined mainly by energy imports and labour exports. Stressing the need to build a more robust relationship, he said, “We are no longer content to be passive recipients of outcomes. India’s landmark ‘Act East’ policy would be matched with ‘Think West’.”[3] This was the first time the phrase ‘Think West’ was used, signalling that a shift in policy was underway.
India’s earlier reticent approach towards West Asia was rooted in two main factors. First, it stemmed from solidarity with the newly independent Gulf nations, owing to a shared history of colonial rule. Second, due to its non-aligned stance during the Cold War, India viewed socialist and secular states more favourably than regional monarchies. A shift occurred during the 1973 oil crisis, prompting India to prioritise engagement with oil-producing nations. However, this engagement was primarily economic, characterised by a transactional buyer-seller relationship. Additionally, the significant Indian diaspora in West Asia, a region dominated by Islam, necessitated a more nuanced approach. India’s foreign policy increasingly took religious considerations into account, influencing both domestic and international affairs.
When the BJP-led NDA government came to power in 2014, it shed the hesitations of earlier years, adopting a more robust approach to West Asia that aligned with India’s evolving worldview. While New Delhi remained sensitive to the potential impact of domestic issues on its relations with predominantly Islamic WANA countries, religion ceased to be an overriding concern. The focus shifted to forging strategic partnerships through political, economic, and security initiatives aimed at strengthening mutual interests. There was also a growing confidence and sense of purpose in engaging with Gulf countries, despite their mutual antagonisms. India successfully cultivated vibrant relations with Saudi Arabia and Iran, navigating their historical animosities. Similarly, India developed strong ties with Israel and Palestine, despite their longstanding conflict. This de-hyphenation of relations allowed New Delhi to build each relationship based on its own merits and for mutual benefit, reflecting India’s enhanced global stature.
In India’s neighbourhood, these relationships are part of India’s broader outreach in the Indian Ocean under the SAGAR initiative. SAGAR, an acronym for Security and Growth for All in the Region, was introduced by Prime Minister Modi in 2015. Through SAGAR, India aims to ensure a safe, secure, and stable Indian Ocean Region (IOR) by fostering economic and security cooperation with its maritime neighbours and enhancing their maritime security capabilities. Cooperation with Gulf countries is integral to the SAGAR initiative, aimed at maintaining free, open, and secure sea lanes of communication for international shipping, including humanitarian aid and disaster relief (HADR) missions.
The vision of SAGAR is inclusive, emphasising politico-economic-security cooperation and adherence to international maritime laws.[4] India’s engagement with West Asia now extends beyond energy, trade, and people-to-people contacts. While India remains dependent on the Gulf for its energy needs, the relationship has diversified into new areas. Gulf nations increasingly view India as a safe investment destination and a reliable security partner. This shift marks a departure from India’s earlier piecemeal transactional approach to a more holistic and strategic intent.
On the security front, the Indian Navy plays a crucial role in ensuring open sea lanes and mitigating piracy threats in the Western Indian Ocean. Currently, the Indian Navy has deployed a dozen warships in the Western Arabian Sea, along with two warships in the Gulf of Aden. This deployment addresses the challenges posed by Somali piracy in the Gulf of Aden and potential attacks by Houthi rebels in the Red Sea.[5] This represents a significant departure from previous deployments in terms of both strength and operational scope, contributing to maintaining calm and incident-free conditions in this part of the Indian Ocean.
The last decade has witnessed the Indian military conducting joint air, naval, and army exercises with the Emirates and Oman, as well as multilateral exercises involving Qatar, Bahrain, and Saudi Arabia. These exercises not only enhance interoperability with regional counterparts but also signal India’s capability as a net security provider in the region. India has also joined the 43-nation Combined Maritime Forces naval partnership based in Bahrain, facilitating multilateral security operations in the Gulf.[6]
However, West Asia and North Africa (WANA) face immense challenges. Ongoing conflicts in Syria and Yemen, strained relations between Israel and Iran, as well as Israel and Hamas, and the sectarian divide between Saudi Arabia and Iran pose significant hurdles to achieving peace and stability. These challenges are further complicated by conflicting interests among major regional powers. While events in West Asia may not directly impact India, disruptions in energy supplies could have unsettling effects on both India’s and the world’s economies. West Asia remains a high-stakes arena, where India, with its goodwill across the region, can potentially play a peacemaking role.
Author Bio: Maj. Gen. Dhruv C. Katoch is Editor, India Foundation Journal and Director, India Foundation
References:
[1] Ram Madhav, Panchamrit: The Five Pillars of Indian Foreign Policy in India’s Foreign Policy: Towards Resurgence, Dhruv C Katoch (Ed), New Delhi, Pentagon, 2016, pp. 20-24.
[2] https://www.mea.gov.in/Speeches-Statements.htm?dtl/26432/Speech_by_External_Affairs_Minister_at_the_inauguration_of_Raisina_Dialogue_in_New_Delhi_March_01_2016
[3] Conference Report, Raisina Dialogue March1-3, 2016, pp 61-63, available at https://www.orfonline.org/forums/raisina-dialogue-2016
[4] https://maritimeindia.org/revisiting-sagar-indias-template-for-cooperation-in-the-indian-ocean-region/
[5] https://www.orfonline.org/research/dynamic-shift-indian-navy-in-the-red-sea
[6] https://warontherocks.com/2024/05/indias-engagement-with-the-middle-east-reflects-new-delhis-changing-worldview/